从几个CTF题目学习内存取证(二)
接上篇,又是两个题目。
Memory-3
题目名Cookies.raw,盲猜就是和cookie有关,上来常规操作查看进程,cmd,等等都一无所获,查看用户密码,发现Cookie账户的密码也是cookie,所有内容都指向了Cookie,查找cookie相关文件。
┌──(root@kali)-[~]
└─# volatility -f Cookie.raw --profile=Win7SP1x86_23418 filescan | grep "Cookie\|Cookies\|cookie\|cookies"
Volatility Foundation Volatility Framework 2.6
0x000000003e401808 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e423038 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Accessibility\Desktop.ini
0x000000003e426238 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e4292d8 17 1 -W-rw- \Device\HarddiskVolume1\Windows\Temp\vmware-vmusr-Cookie.log
0x000000003e44d308 1 0 R--r-- \Device\HarddiskVolume1\Users\Cookie\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94308059B57B3142E455B38A6EB92015
0x000000003e451a58 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Saved Games\desktop.ini
0x000000003e479858 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TM.blf
0x000000003e47bc98 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat{5b0156fa-4cb4-11ea-88d3-b808cfa87f45}.TMContainer00000000000000000002.regtrans-ms
0x000000003e47d8f8 2 1 RW-rw- \Device\clfs\Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TM
0x000000003e47e038 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000001.regtrans-ms
0x000000003e47e5b8 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000002.regtrans-ms
0x000000003e47e6f0 1 1 RW-rwd \Device\clfs\Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT{6cced2f1-6e01-11de-8bed-001e0bcd1824}.TM
0x000000003e47ef30 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\ntuser.dat.LOG2
0x000000003e47f138 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Credentials
0x000000003e47f280 1 1 RW-rwd \Device\clfs\Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat{5b0156fa-4cb4-11ea-88d3-b808cfa87f45}.TM
0x000000003e47f700 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat{5b0156fa-4cb4-11ea-88d3-b808cfa87f45}.TMContainer00000000000000000001.regtrans-ms
0x000000003e47ff80 2 1 RW-r-- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat{5b0156fa-4cb4-11ea-88d3-b808cfa87f45}.TM.blf
0x000000003e480b48 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003e480f80 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Credentials
0x000000003e485448 3 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Recent
0x000000003e485508 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\WER\ReportArchive
0x000000003e486038 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Desktop\desktop.ini
0x000000003e488e18 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Favorites\Links\desktop.ini
0x000000003e4a7f40 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e4e9740 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Music\desktop.ini
0x000000003e4eb860 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Favorites\desktop.ini
0x000000003e4ec858 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e4f10d8 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Pictures\desktop.ini
0x000000003e4fe770 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e508968 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e50a1c0 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Libraries
0x000000003e50da60 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Downloads\desktop.ini
0x000000003e51c038 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Searches\desktop.ini
0x000000003e529248 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\desktop.ini
0x000000003e52a038 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Documents\desktop.ini
0x000000003e52b130 8 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003e52ec00 4 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e52fb40 8 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e530160 8 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003e532f80 8 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e553720 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Printer Shortcuts
0x000000003e554e00 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003e5580f0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003e55ebb0 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned
0x000000003e5777e0 1 0 R--r-- \Device\HarddiskVolume1\Users\Cookie\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F0ACCF77CDCBFF39F6191887F6D2D357
0x000000003e5789e0 1 1 R--rw- \Device\HarddiskVolume1\Users\Cookie\Desktop
0x000000003e57a580 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e57b880 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Printer Shortcuts
0x000000003e58a1b0 1 1 -W-rw- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Temp\FXSAPIDebugLogFile.txt
0x000000003e58f8d0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e592b28 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e5cd810 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003e5f1038 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Recent\desktop.ini
0x000000003e5f1668 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\Desktop
0x000000003e5fcbd0 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Libraries
0x000000003e610768 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e610a30 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003e6685b0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003e669dc0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e66a038 2 2 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e66a228 1 1 RW-rw- \Device\HarddiskVolume1\Users\Cookie\Desktop\WIN-I0396FOVLRF-20200211-121148.raw
0x000000003e66a698 3 0 R--r-- \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Themes\TranscodedWallpaper.jpg
0x000000003e671d28 8 0 R--r-d \Device\HarddiskVolume1\Users\Cookie\Desktop\DumpIt.exe
0x000000003e685038 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003e685688 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Libraries\Documents.library-ms
0x000000003e687038 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e6873c0 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Contacts\desktop.ini
0x000000003e69caf0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e69ecd0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003e6bb828 8 0 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003e6d94e8 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\desktop.ini
0x000000003e6fd988 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Libraries\desktop.ini
0x000000003e6ff820 1 0 R--r-- \Device\HarddiskVolume1\Users\Cookie\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F0ACCF77CDCBFF39F6191887F6D2D357
0x000000003e6ff950 8 0 R--r-d \Device\HarddiskVolume1\Users\Cookie\Desktop\DumpIt.exe
0x000000003e70c8c0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003e713b70 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\ntuser.dat.LOG1
0x000000003e7145c0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e73af80 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Maintenance\Desktop.ini
0x000000003e755260 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003e75bd90 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Burn
0x000000003e75be48 1 0 R--rw- \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\Internet Explorer.lnk
0x000000003e77aed0 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\WER\ERC
0x000000003e7822b0 1 0 R--r-- \Device\HarddiskVolume1\Users\Cookie\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94308059B57B3142E455B38A6EB92015
0x000000003e7f2c08 2 1 RW-rw- \Device\clfs\Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat{5b0156fa-4cb4-11ea-88d3-b808cfa87f45}.TM
0x000000003e8ba690 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003e8f6bb8 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Videos\desktop.ini
0x000000003e902d30 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\desktop.ini
0x000000003e9041e0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003e90e718 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\System Tools\Desktop.ini
0x000000003e919910 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Accessories\Desktop.ini
0x000000003e9199c8 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\desktop.ini
0x000000003e91b3c0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_idx.db
0x000000003e91da08 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu
0x000000003e9206e0 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu
0x000000003e93e4b8 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned
0x000000003e9416d0 2 2 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e957c80 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_1024.db
0x000000003e958770 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\desktop.ini
0x000000003e969be0 2 0 RW-rw- \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Recent\Cookie.lnk
0x000000003e96c190 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Favorites\Links for 中国\desktop.ini
0x000000003e96fb18 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\Links\desktop.ini
0x000000003e9af120 3 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu
0x000000003e9b4480 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db
0x000000003e9e0cc0 1 0 R--rw- \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Internet Explorer\Quick Launch\User Pinned\TaskBar\Windows Explorer.lnk
0x000000003eb33bc8 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\Desktop
0x000000003f345eb8 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003f34ee40 2 1 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Burn
0x000000003f36c038 2 0 RW---- \Device\HarddiskVolume1\Users\Cookie\cookie\Cookies.db
0x000000003f36c7f8 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003f36d750 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Administrative Tools\desktop.ini
0x000000003f39bbf0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003f3a0e38 2 2 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003f3ae898 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_256.db
0x000000003f3d8c10 1 0 R--rw- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\2052\StructuredQuerySchema.bin
0x000000003f3eecf8 8 0 RW-r-- \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\1b4dd67f29cb1962.automaticDestinations-ms
0x000000003f988c70 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_96.db
0x000000003fc813e8 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat.LOG2
0x000000003fc818c8 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat
0x000000003fca7630 1 0 R--rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Roaming\Microsoft\Windows\SendTo\Desktop.ini
0x000000003fca9bf8 8 0 RW-rw- \Device\HarddiskVolume1\Windows\ServiceProfiles\LocalService\AppData\Roaming\Microsoft\Windows\Cookies\index.dat
0x000000003ff2a8e8 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_sr.db
0x000000003ff2ce48 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\NTUSER.DAT
0x000000003ff2eb88 1 1 RW---- \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\UsrClass.dat.LOG1
0x000000003ffa0cb0 1 1 RW-rwd \Device\HarddiskVolume1\Users\Cookie\AppData\Local\Microsoft\Windows\Explorer\thumbcache_32.db一大堆文件中只有一个Cookies.db的数据库文件引人注目,dump下来查看内容
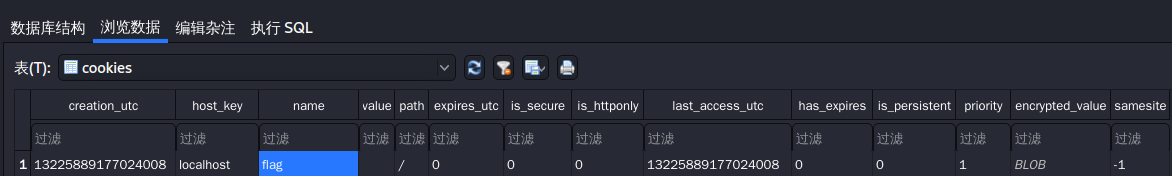
发现有name字段是flag,这说明flag一定是被set为Cookie值了,那就查一下有网络连接的进程都有哪些
┌──(root@kali)-[~]
└─# volatility -f Cookie.raw --profile=Win7SP1x86_23418 netscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Proto Local Address Foreign Address State Pid Owner Created
0x3e447530 UDPv6 ::1:56818 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e6015e8 UDPv4 0.0.0.0:5355 *:* 1132 svchost.exe 2020-02-11 12:01:01 UTC+0000
0x3e6015e8 UDPv6 :::5355 *:* 1132 svchost.exe 2020-02-11 12:01:01 UTC+0000
0x3e609008 UDPv4 192.168.171.130:137 *:* 4 System 2020-02-11 12:00:58 UTC+0000
0x3e60b808 UDPv4 192.168.171.130:138 *:* 4 System 2020-02-11 12:00:58 UTC+0000
0x3e700dd0 UDPv4 0.0.0.0:0 *:* 1132 svchost.exe 2020-02-11 12:00:58 UTC+0000
0x3e700dd0 UDPv6 :::0 *:* 1132 svchost.exe 2020-02-11 12:00:58 UTC+0000
0x3e723908 UDPv4 127.0.0.1:56819 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e7314c0 UDPv4 127.0.0.1:1900 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e731f50 UDPv4 192.168.171.130:1900 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e735e38 UDPv6 ::1:1900 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e738250 UDPv6 fe80::b5ea:cf3f:767d:751d:1900 *:* 3224 svchost.exe 2020-02-11 12:03:00 UTC+0000
0x3e7701e8 UDPv4 0.0.0.0:5355 *:* 1132 svchost.exe 2020-02-11 12:01:01 UTC+0000
0x3e66e420 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 876 svchost.exe
0x3e66ff60 TCPv4 0.0.0.0:49154 0.0.0.0:0 LISTENING 876 svchost.exe
0x3e66ff60 TCPv6 :::49154 :::0 LISTENING 876 svchost.exe
0x3e709238 TCPv4 192.168.171.130:139 0.0.0.0:0 LISTENING 4 System
0x3e76fbe0 TCPv4 0.0.0.0:445 0.0.0.0:0 LISTENING 4 System
0x3e76fbe0 TCPv6 :::445 :::0 LISTENING 4 System
0x3e77fae0 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 520 services.exe
0x3e77fae0 TCPv6 :::49155 :::0 LISTENING 520 services.exe
0x3e781608 TCPv4 0.0.0.0:49155 0.0.0.0:0 LISTENING 520 services.exe
0x3e7fc0e8 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 528 lsass.exe
0x3e7fc0e8 TCPv6 :::49156 :::0 LISTENING 528 lsass.exe
0x3e7fc708 TCPv4 0.0.0.0:49156 0.0.0.0:0 LISTENING 528 lsass.exe
0x3e4fc5a0 TCPv4 192.168.171.130:49157 192.168.171.2:80 CLOSED 1132 svchost.exe
0x3e99a248 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 716 svchost.exe
0x3e99a248 TCPv6 :::135 :::0 LISTENING 716 svchost.exe
0x3e99a6d0 TCPv4 0.0.0.0:135 0.0.0.0:0 LISTENING 716 svchost.exe
0x3e9a0560 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 412 wininit.exe
0x3e9a6b90 TCPv4 0.0.0.0:49152 0.0.0.0:0 LISTENING 412 wininit.exe
0x3e9a6b90 TCPv6 :::49152 :::0 LISTENING 412 wininit.exe
0x3e9c40c0 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 808 svchost.exe
0x3e9c5980 TCPv4 0.0.0.0:49153 0.0.0.0:0 LISTENING 808 svchost.exe
0x3e9c5980 TCPv6 :::49153 :::0 LISTENING 808 svchost.exe从上边看没什么特殊的进程,都是很正常的链接,但是仔细看时间就发现12:03:00之后的就不显示了,这就点奇怪,折回去看进程
┌──(root@kali)-[~]
└─# volatility -f Cookie.raw --profile=Win7SP1x86_23418 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
-------------------------------------------------------------------------------------------------------------------
0x8654b7e0 System 4 0 103 486 ------ 0 2020-02-11 12:00:41 UTC+0000
0x871f3298 smss.exe 272 4 2 32 ------ 0 2020-02-11 12:00:41 UTC+0000
0x871fb558 csrss.exe 360 340 9 457 0 0 2020-02-11 12:00:44 UTC+0000
0x87ab9d40 wininit.exe 412 340 3 82 0 0 2020-02-11 12:00:45 UTC+0000
0x87ab9458 csrss.exe 420 404 12 206 1 0 2020-02-11 12:00:45 UTC+0000
0x87269d40 winlogon.exe 480 404 5 124 1 0 2020-02-11 12:00:46 UTC+0000
0x87b1f030 services.exe 520 412 6 213 0 0 2020-02-11 12:00:46 UTC+0000
0x87b222e8 lsass.exe 528 412 9 572 0 0 2020-02-11 12:00:46 UTC+0000
0x87b23a60 lsm.exe 536 412 10 140 0 0 2020-02-11 12:00:46 UTC+0000
0x87b7e968 svchost.exe 636 520 13 374 0 0 2020-02-11 12:00:51 UTC+0000
0x87b8bd40 svchost.exe 716 520 9 298 0 0 2020-02-11 12:00:52 UTC+0000
0x87bae410 svchost.exe 808 520 21 475 0 0 2020-02-11 12:00:52 UTC+0000
0x87bc5438 svchost.exe 844 520 16 396 0 0 2020-02-11 12:00:52 UTC+0000
0x87bca648 svchost.exe 876 520 35 1015 0 0 2020-02-11 12:00:52 UTC+0000
0x87bdfd40 audiodg.exe 956 808 6 138 0 0 2020-02-11 12:00:53 UTC+0000
0x8666cd40 svchost.exe 1036 520 12 580 0 0 2020-02-11 12:00:53 UTC+0000
0x87c1b030 svchost.exe 1132 520 16 377 0 0 2020-02-11 12:00:53 UTC+0000
0x87c7c890 spoolsv.exe 1280 520 14 287 0 0 2020-02-11 12:00:54 UTC+0000
0x87c99450 svchost.exe 1376 520 20 311 0 0 2020-02-11 12:00:55 UTC+0000
0x87d2a0f0 VGAuthService. 1560 520 4 98 0 0 2020-02-11 12:00:56 UTC+0000
0x87d3d030 vmtoolsd.exe 1584 520 11 278 0 0 2020-02-11 12:00:57 UTC+0000
0x87d91880 svchost.exe 1824 520 6 93 0 0 2020-02-11 12:00:59 UTC+0000
0x8666fb90 dllhost.exe 128 520 15 209 0 0 2020-02-11 12:01:01 UTC+0000
0x87cc9d40 msdtc.exe 596 520 14 158 0 0 2020-02-11 12:01:02 UTC+0000
0x87e1e030 WmiPrvSE.exe 920 636 11 217 0 0 2020-02-11 12:01:02 UTC+0000
0x87e8a030 taskhost.exe 2096 520 9 213 1 0 2020-02-11 12:01:06 UTC+0000
0x87ea8990 dwm.exe 2188 844 5 138 1 0 2020-02-11 12:01:06 UTC+0000
0x865edbb0 explorer.exe 2216 2164 38 970 1 0 2020-02-11 12:01:07 UTC+0000
0x87f201d8 vm3dservice.ex 2404 2216 2 50 1 0 2020-02-11 12:01:10 UTC+0000
0x87f28850 vmtoolsd.exe 2412 2216 10 199 1 0 2020-02-11 12:01:10 UTC+0000
0x87c65578 SearchIndexer. 2584 520 12 667 0 0 2020-02-11 12:01:16 UTC+0000
0x87f92350 WmiPrvSE.exe 2764 636 10 224 0 0 2020-02-11 12:01:20 UTC+0000
0x87e969b8 svchost.exe 3224 520 10 145 0 0 2020-02-11 12:02:59 UTC+0000
0x87da3d40 sppsvc.exe 3272 520 4 159 0 0 2020-02-11 12:03:00 UTC+0000
0x87cdbd40 svchost.exe 3344 520 9 310 0 0 2020-02-11 12:03:00 UTC+0000
0x87d65030 taskhost.exe 2924 520 8 181 0 0 2020-02-11 12:09:55 UTC+0000
0x87f2a550 SearchProtocol 3520 2584 7 320 0 0 2020-02-11 12:10:35 UTC+0000
0x87e6a030 SearchFilterHo 2692 2584 6 101 0 0 2020-02-11 12:10:35 UTC+0000
0x87fbcd40 DumpIt.exe 3632 2216 1 18 1 0 2020-02-11 12:11:48 UTC+0000
0x8655fcb0 conhost.exe 1684 420 2 60 1 0 2020-02-11 12:11:48 UTC+0000
0x87ffc0c8 dllhost.exe 3552 636 6 0 ------ 0 2020-02-11 12:11:52 UTC+0000明显12:03-12:09这段时间空白了,百度查了查这些进程都是系统进程,都是系统进程,没思路,就直接dump出来这个两个进程看看都有啥
┌──(root@kali)-[~]
└─# volatility -f Cookie.raw --profile=Win7SP1x86_23418 memdump -p 3344 -D ./
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing svchost.exe [ 3344] to 3344.dmp
┌──(root@kali)-[~]
└─# volatility -f Cookie.raw --profile=Win7SP1x86_23418 memdump -p 2924 -D ./
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing taskhost.exe [ 2924] to 2924.dmp
┌──(root@kali)-[~]
└─# strings 3344.dmp | grep "Cookie\|cookie\|Cookies\|cookies\|flag\|ctf\|CTF" > 3344.txt
┌──(root@kali)-[~]
└─# strings 2924.dmp | grep "Cookie\|cookie\|Cookies\|cookies\|flag\|ctf\|CTF" > 2924.txt最终在两个文件里都发现了一个$value,这儿猜测出题人是想隐藏操作痕迹,然后让我们通过这种dump进程的方式来找到有用的关键信息。
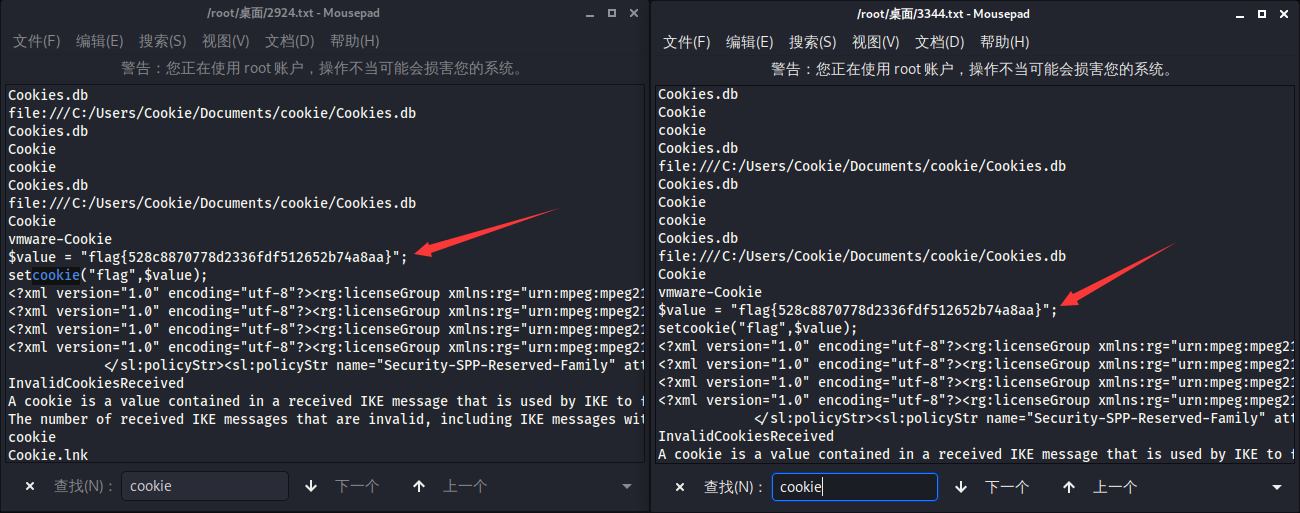
flag{528c8870778d2336fdf512652b74a8aa}
Memory-4
这个是国荣学长出的题,题目体验不错,题目包含了一个内存文件forensics.raw和一个pcap.pcapng流量包
先常规看看内存文件都有什么值得注意的地方
┌──(root@kali)-[~]
└─# volatility -f forensics.raw --profile=WinXPSP2x86 pslist
Volatility Foundation Volatility Framework 2.6
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit
-------------------------------------------------------------------------------------------------------------------
0x821bb830 System 4 0 52 279 ------ 0
0x81fcfda0 smss.exe 540 4 3 19 ------ 0 2020-04-17 15:44:10 UTC+0000
0x81f82920 csrss.exe 596 540 9 300 0 0 2020-04-17 15:44:11 UTC+0000
0x81f6e488 winlogon.exe 616 540 14 212 0 0 2020-04-17 15:44:13 UTC+0000
0x81f85b98 services.exe 660 616 15 252 0 0 2020-04-17 15:44:15 UTC+0000
0x81f2dda0 lsass.exe 672 616 26 336 0 0 2020-04-17 15:44:15 UTC+0000
0x81f0b310 vmacthlp.exe 868 660 1 24 0 0 2020-04-17 15:44:16 UTC+0000
0x81f02880 svchost.exe 900 660 6 104 0 0 2020-04-17 15:44:16 UTC+0000
0x81f15b28 svchost.exe 968 660 10 221 0 0 2020-04-17 15:44:16 UTC+0000
0x81ef9900 svchost.exe 1076 660 39 730 0 0 2020-04-17 15:44:17 UTC+0000
0x81edd020 svchost.exe 1096 660 5 57 0 0 2020-04-17 15:44:17 UTC+0000
0x81ec0020 explorer.exe 1264 1188 15 406 0 0 2020-04-17 15:44:17 UTC+0000
0x81ea21d0 vmtoolsd.exe 1428 1264 7 167 0 0 2020-04-17 15:44:19 UTC+0000
0x81eb8b88 ctfmon.exe 1440 1264 1 36 0 0 2020-04-17 15:44:19 UTC+0000
0x81e93da0 VGAuthService.e 1612 660 2 61 0 0 2020-04-17 15:44:35 UTC+0000
0x81e924c0 vmtoolsd.exe 1680 660 8 242 0 0 2020-04-17 15:44:35 UTC+0000
0x81e80da0 svchost.exe 2016 660 10 148 0 0 2020-04-17 15:45:06 UTC+0000
0x81ed2da0 wmiprvse.exe 300 900 11 228 0 0 2020-04-17 15:45:07 UTC+0000
0x81e7e020 conime.exe 1004 172 1 26 0 0 2020-04-17 15:53:37 UTC+0000
0x81f27020 cmd.exe 1908 1264 1 28 0 0 2020-04-18 12:01:51 UTC+0000
0x81f873f8 TrueCrypt.exe 1904 1264 7 142 0 0 2020-04-18 12:02:27 UTC+0000
0x81d77020 DumpIt.exe 220 1264 1 15 0 0 2020-04-18 12:05:10 UTC+0000 看了看进程,只有cmd和TrueCrypt,值得关注,结合流量包,再捎带手看看网络连接,但是由于镜像是WinXP,无法查看netscan,所以先看看另外俩进程都有啥
┌──(root@kali)-[~]
└─# volatility -f forensics.raw --profile=WinXPSP2x86 cmdline
Volatility Foundation Volatility Framework 2.6
************************************************************************
System pid: 4
************************************************************************
smss.exe pid: 540
Command line : \SystemRoot\System32\smss.exe
************************************************************************
csrss.exe pid: 596
Command line : C:\WINDOWS\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,3072,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ProfileControl=Off MaxRequestThreads=16
************************************************************************
winlogon.exe pid: 616
Command line : winlogon.exe
************************************************************************
services.exe pid: 660
Command line : C:\WINDOWS\system32\services.exe
************************************************************************
lsass.exe pid: 672
Command line : C:\WINDOWS\system32\lsass.exe
************************************************************************
vmacthlp.exe pid: 868
Command line : "C:\Program Files\VMware\VMware Tools\vmacthlp.exe"
************************************************************************
svchost.exe pid: 900
Command line : C:\WINDOWS\system32\svchost -k DcomLaunch
************************************************************************
svchost.exe pid: 968
Command line : C:\WINDOWS\system32\svchost -k rpcss
************************************************************************
svchost.exe pid: 1076
Command line : C:\WINDOWS\system32\svchost.exe -k netsvcs
************************************************************************
svchost.exe pid: 1096
Command line : C:\WINDOWS\system32\svchost.exe -k NetworkService
************************************************************************
explorer.exe pid: 1264
Command line : C:\WINDOWS\Explorer.EXE
************************************************************************
vmtoolsd.exe pid: 1428
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe" -n vmusr
************************************************************************
ctfmon.exe pid: 1440
Command line : "C:\WINDOWS\system32\CTFMON.EXE"
************************************************************************
VGAuthService.e pid: 1612
Command line : "C:\Program Files\VMware\VMware Tools\VMware VGAuth\VGAuthService.exe"
************************************************************************
vmtoolsd.exe pid: 1680
Command line : "C:\Program Files\VMware\VMware Tools\vmtoolsd.exe"
************************************************************************
svchost.exe pid: 2016
Command line : C:\WINDOWS\system32\svchost.exe -k LocalService
************************************************************************
wmiprvse.exe pid: 300
Command line : C:\WINDOWS\system32\wbem\wmiprvse.exe
************************************************************************
conime.exe pid: 1004
Command line : C:\WINDOWS\system32\conime.exe
************************************************************************
cmd.exe pid: 1908
Command line : "C:\WINDOWS\system32\cmd.exe"
************************************************************************
TrueCrypt.exe pid: 1904
Command line : "C:\Program Files\TrueCrypt(jb51.net)\TrueCrypt.exe"
************************************************************************
DumpIt.exe pid: 220
Command line : "C:\Documents and Settings\Administrator\桌面\DumpIt.exe"
┌──(root@kali)-[~]
└─# volatility -f forensics.raw --profile=WinXPSP2x86 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: csrss.exe Pid: 596
CommandHistory: 0x526bb8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 3 LastAdded: 2 LastDisplayed: 2
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x3d4
Cmd #0 @ 0x36cc7d8: flag{7h1s_1s_noT_fl@g}
Cmd #1 @ 0x52ae78: 23333333
Cmd #2 @ 0x5224b8: :)
**************************************************
CommandProcess: csrss.exe Pid: 596
CommandHistory: 0x52a0e8 Application: DumpIt.exe Flags: Allocated
CommandCount: 0 LastAdded: -1 LastDisplayed: -1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x2d8还有一个fakeflag真是太坏了。。。那就只能是TrueCrypt了,联想到之前做的V&N公开赛的内存取证,可以利用Elcomsoft Forensic Disk Decryptor工具破解TrueCrypt,先dump出来进程文件备用。
┌──(root@kali)-[~]
└─# volatility -f forensics.raw --profile=WinXPSP2x86 memdump -p 1904 -D ./ 130 ⨯
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing TrueCrypt.exe [ 1904] to 1904.dmp在内存中filescan也没找到内存镜像文件,回过头去看流量包,发现有FTP-DATA传输的zip文件
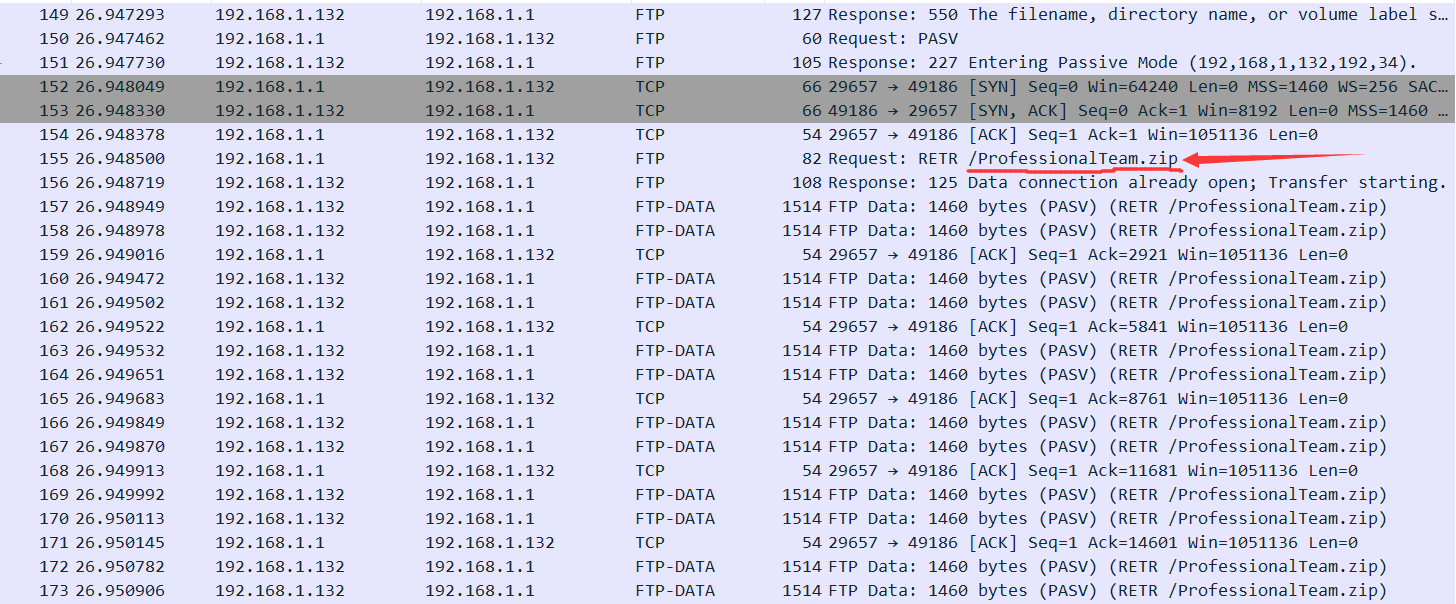

追踪流得到zip全数据,保存为zip文件可以正常解压,基本可以确定是内存镜像文件了
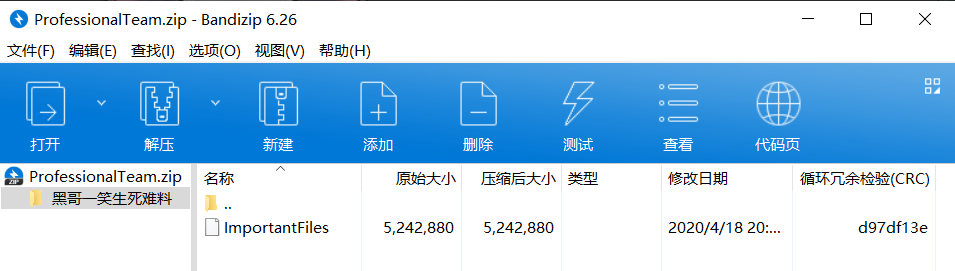
利用软件破解该内存镜像

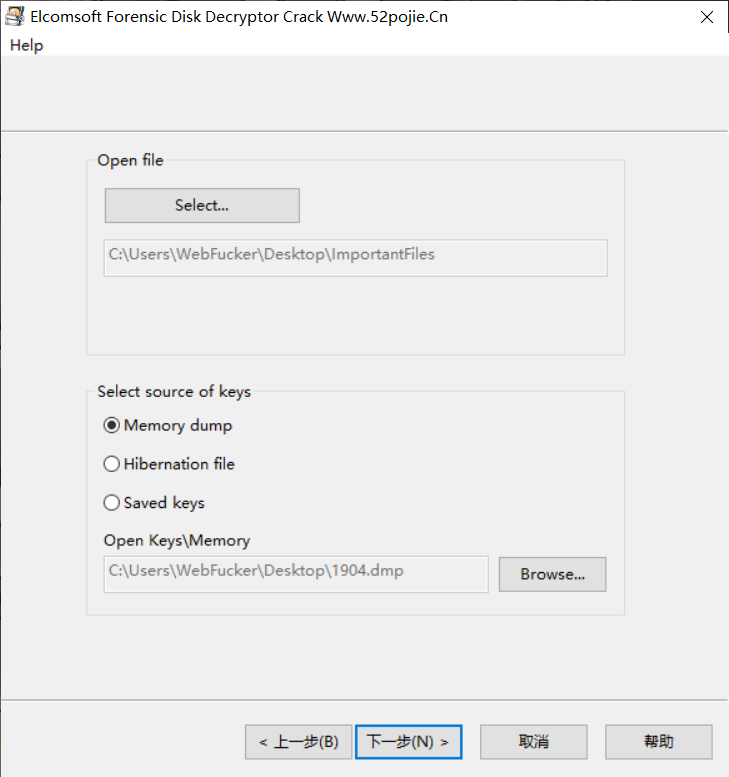
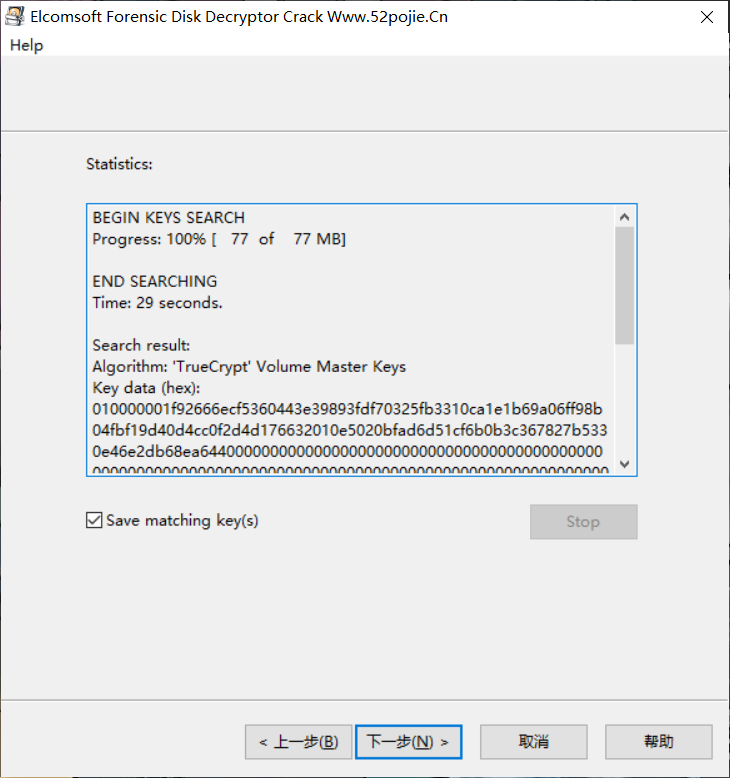
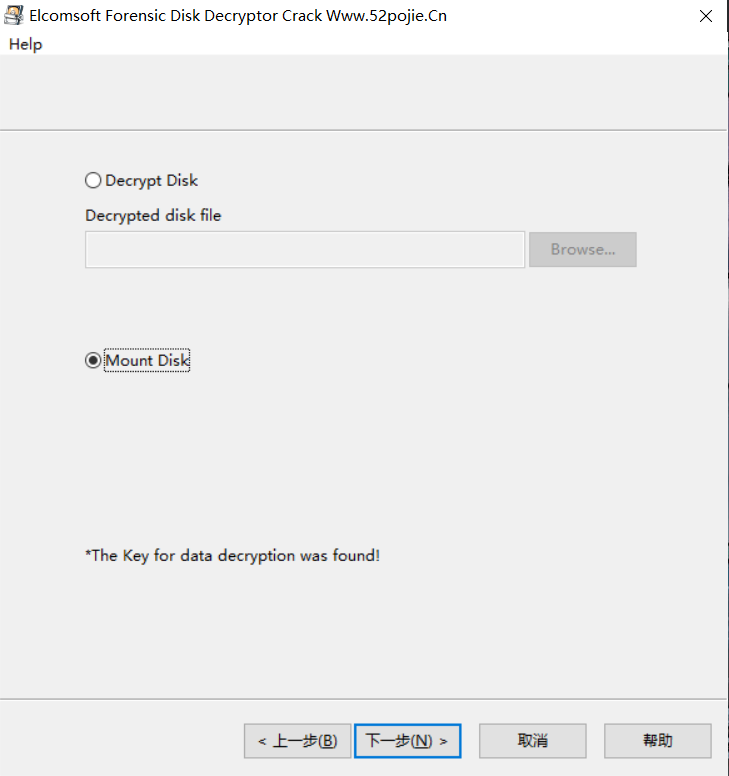
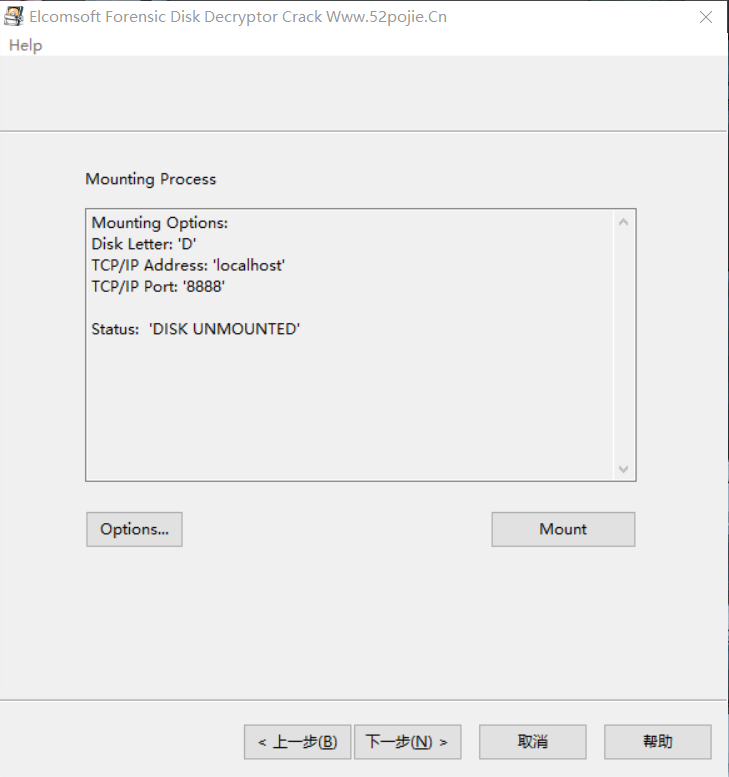
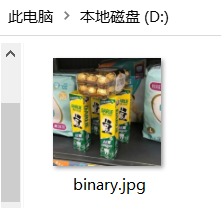
Mount该磁盘,就可以将其挂载出来,查看文件,此处得到一张图
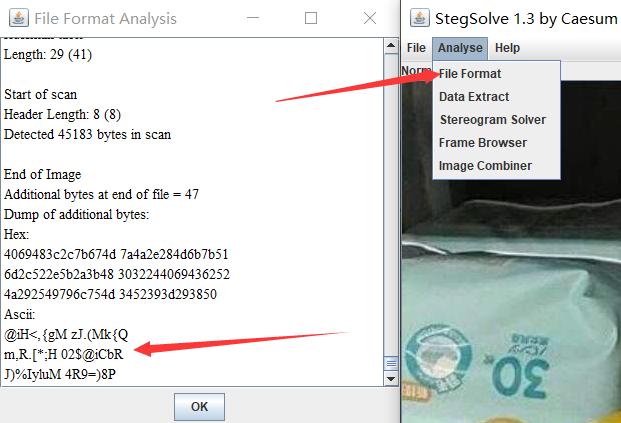
Stegslove查看最低位没有东西,看数据分析发现一段ascii码字符串@iH<,{gMzJ.(Mk{Qm,R.[*;H02$@iCbRJ)%IyluM4R9=)8P
被密码难哭,卡在儿好久,最后才想起来跑脚本测试,是base91加密。
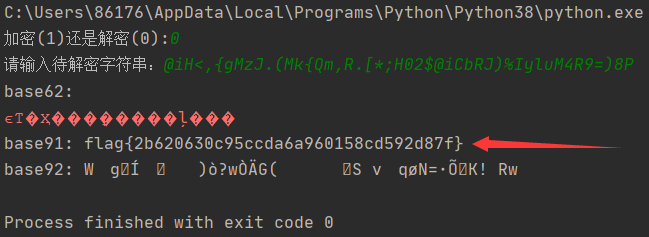
flag{2b620630c95ccda6a960158cd592d87f}



《超银河传说外传:赛罗奥特曼vs黑暗独眼巨人赛罗》科幻片高清在线免费观看:https://www.jgz518.com/xingkong/6740.html
哈哈哈,写的太好了https://www.cscnn.com/
兄弟写的非常好 https://www.cscnn.com/
想想你的文章写的特别好https://www.ea55.com/
叼茂SEO.bfbikes.com
博主真是太厉害了!!!