Hack.lu CTF 2021 - MISC - Emergency Operations(Mid)
emergency-operations_d913c34502f15d39f7b8417f42f904d0.zip
Dave is a notoriously bored system administrator at RipOffMobileNetworks. During the GME frenzy, Dave really got into /r/wallstreetbets, and wants to share some insider knowledge with his fellow traders. Since Dave likes his Job, and doesn’t want the SEC to get involved, he decided to not post his info on reddit, but use the tools he has at hand to distribute his message. Unfortuneatly, Dave wasn’t particularly stealthy in his attempt, and got caught misusing mobile network infrastructure. He even tried to spread his news via the network.All that we could find so far is a traffic dump and a mysterious note he posted online, saying “DLT=149”.
Can you figure out what action Dave wants his folks to take?
Note: Flag format is non-standard. It is not wrapped in flag{}.
附件就一个流量包,直接打开如图
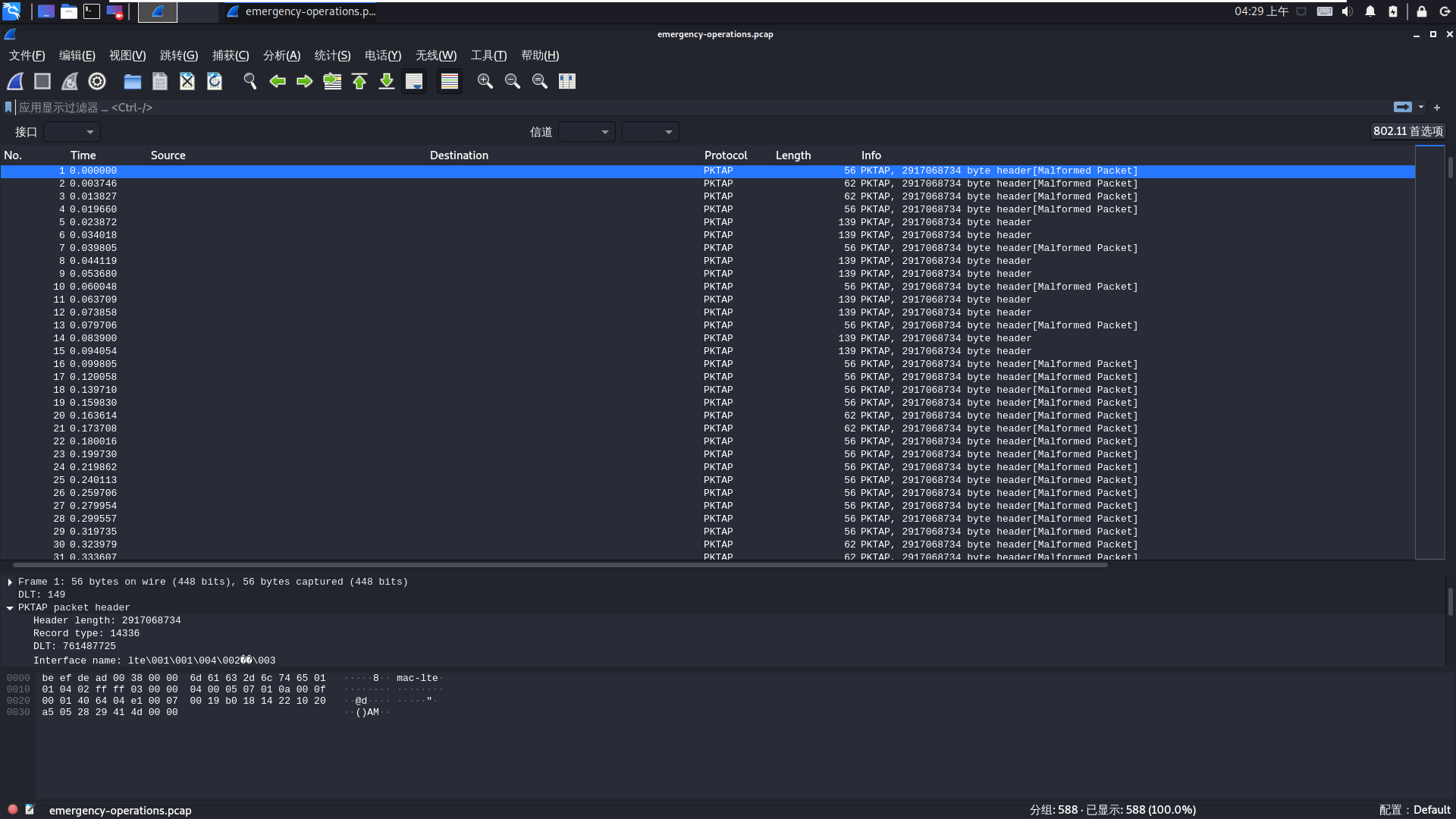
这就是第一个考点了,根据题目描述Dave使用的协议大概率是个移动设备的协议,同时wireshark直接识别出为PKTAP,貌似很符合题意,但是通过分析PKTAP协议的相关标识符,发现其在后部有无法解释的部分。且赛后看选手们交流才发现,每条流量的头部都是0xbeefdead开头,这同时印证了为什么PKTAP为什么不对(毕竟不可能header length高达2917068734)。
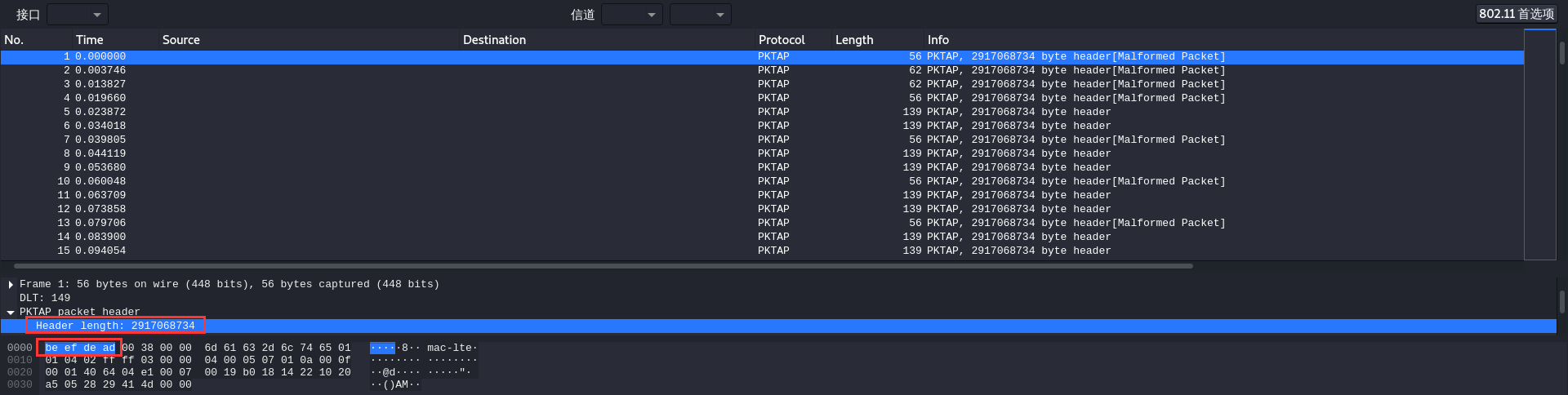
回想到题目中强调了一个"DLT=149",网上冲浪发现这个参数是指DLT_USER=2,且在wireshark中可以设置该参数。(编辑→首选项→Protocols→DLT_USER→Edit→添加一个User2,这时候协议无法识别了,是因为没有设置后边的Payload protocol。
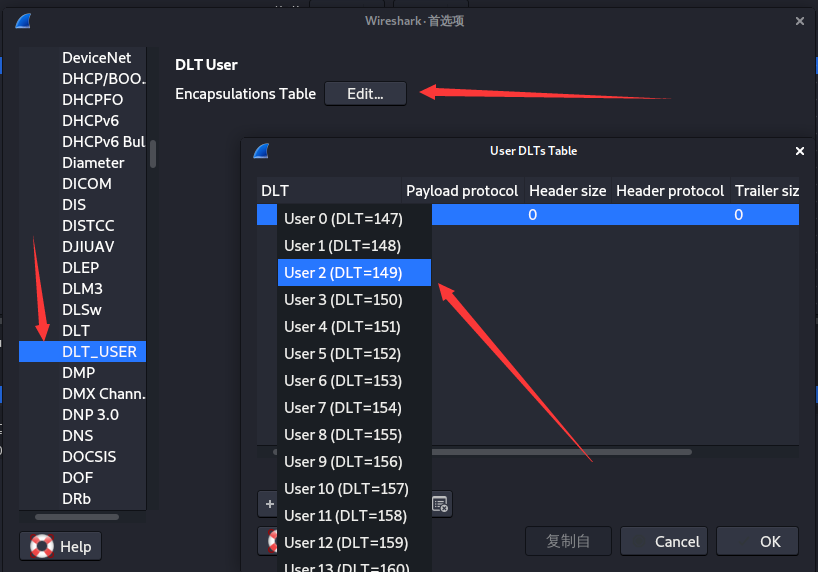
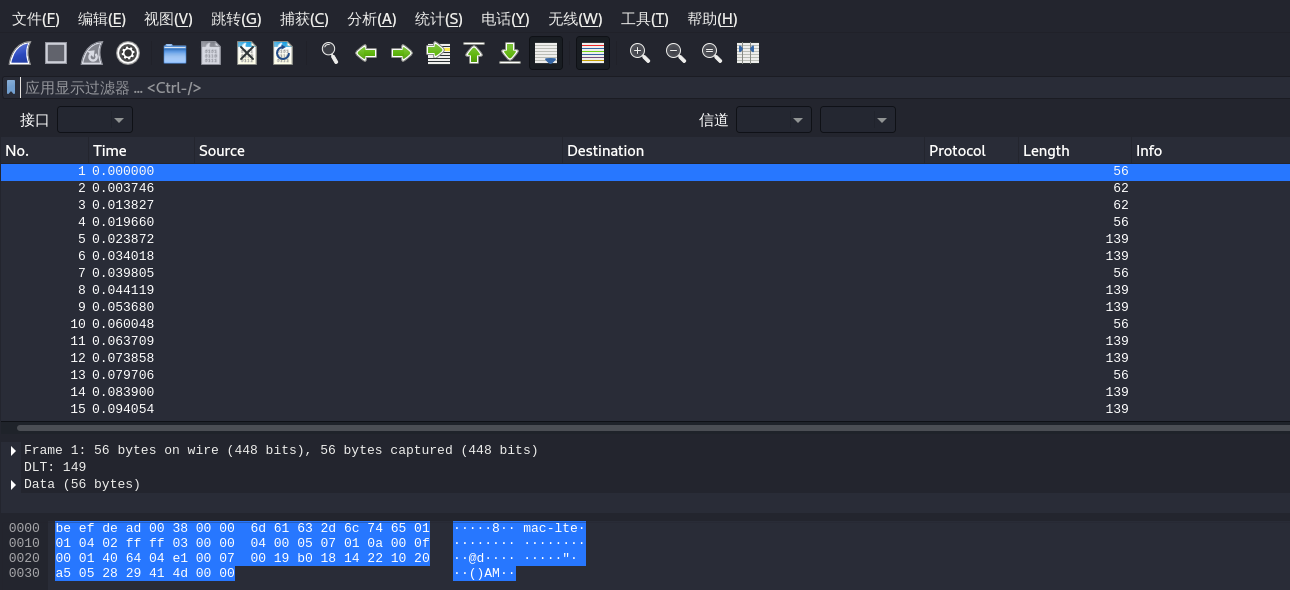
结合DLT=149以及流量中最明显的字样mac-lte,发现某项目中的一段对wireshark设置方法的描述。
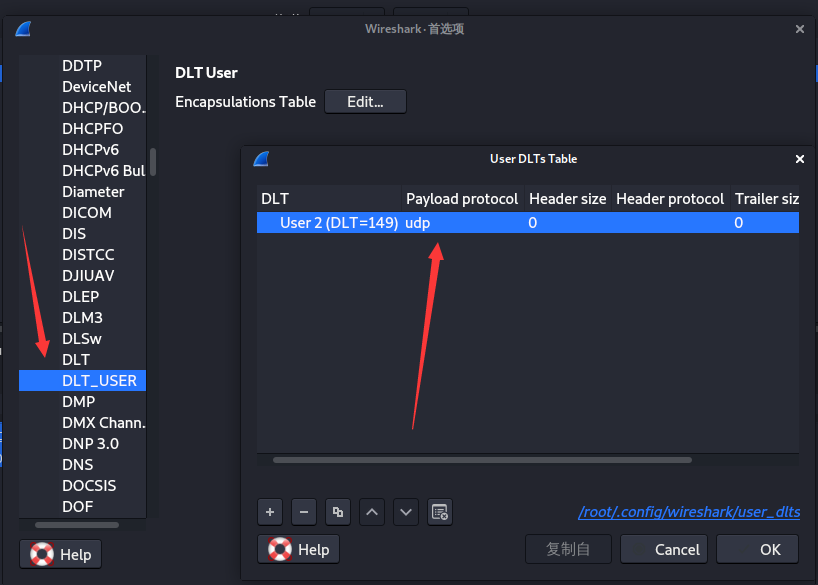
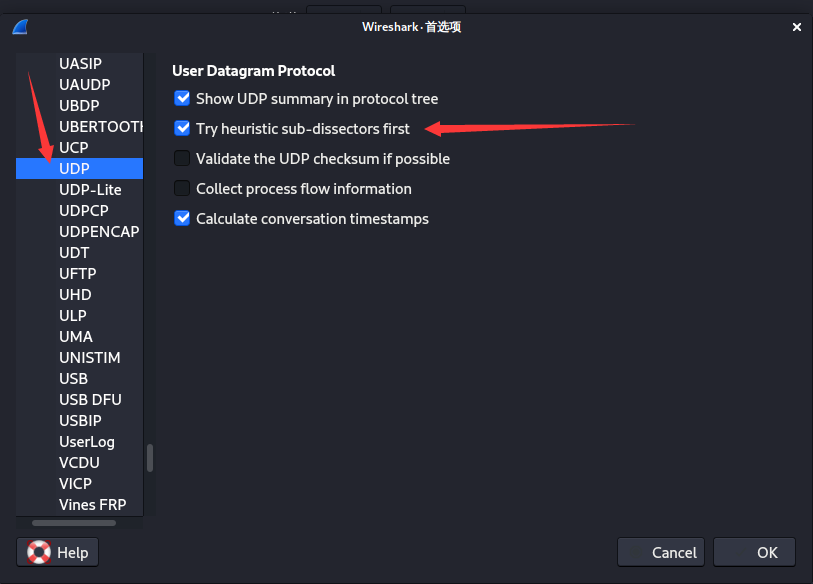
这里有一个wireshark解析顺序设置的考点,你需要先在分析→启用的协议单独开启DLT-USER,UDP,MAC-LTE,mac_lte_udp,MAC-NR,mac-nr-udp这几个协议,让他先解析一次,然后再去启用的协议全部开启,才能正常解析该流量。
解析后协议出现了我们可看见的明文NothingToSeeHere,但是我们不难发现最前面有个乱码字符。
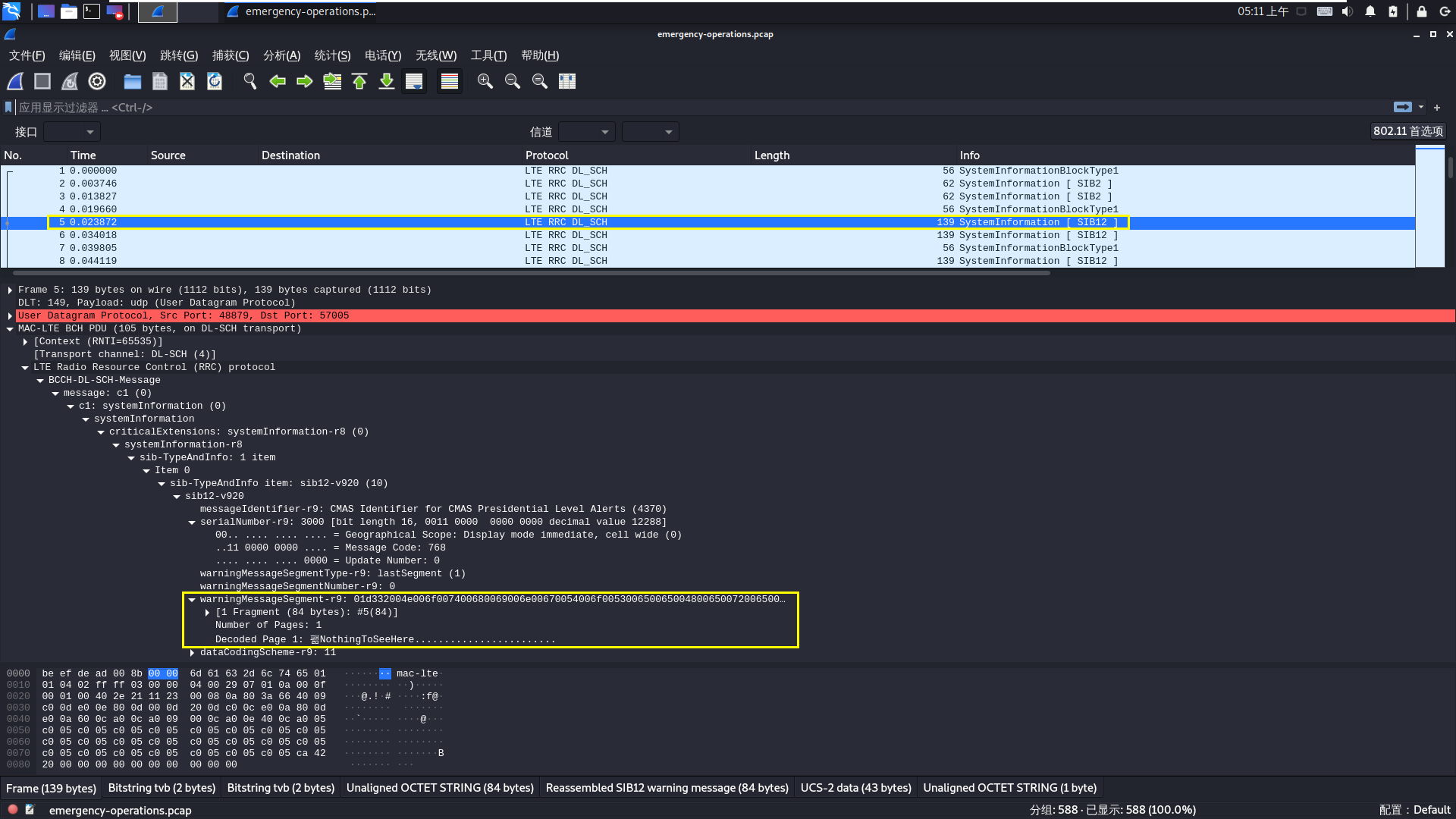
打开该条流量剩下部分,看到Language:UCS2

持续发挥网上冲浪的传统艺能,看到这些
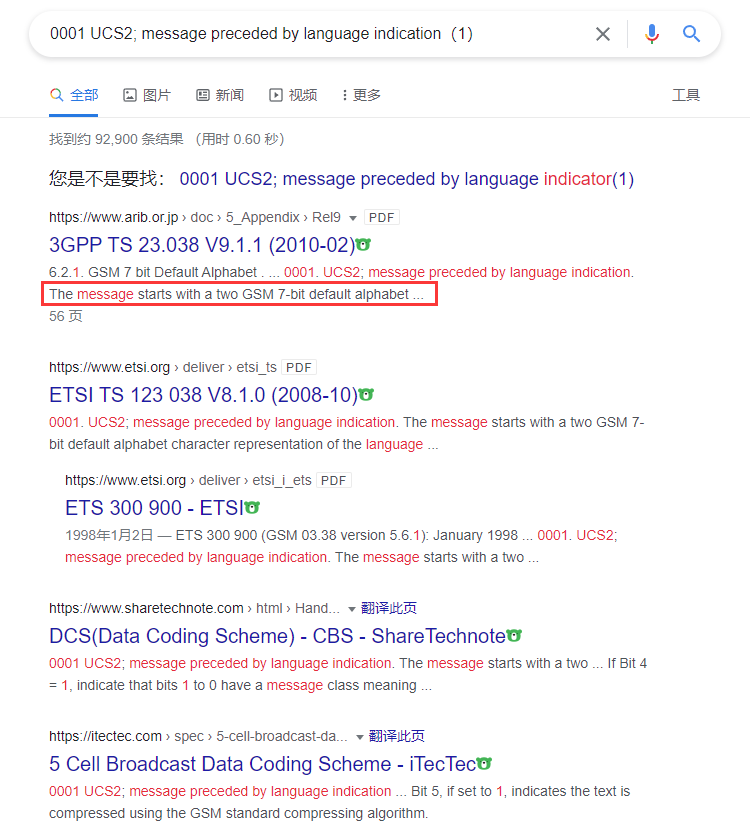
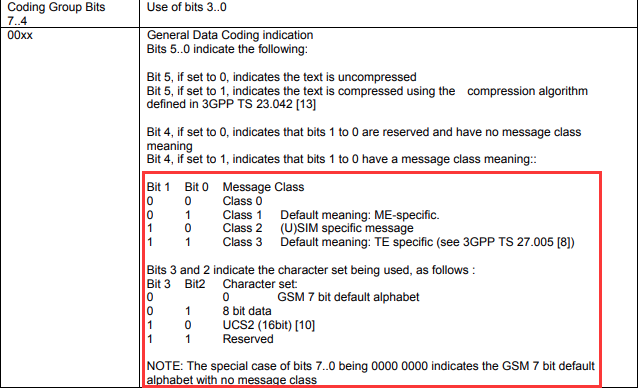
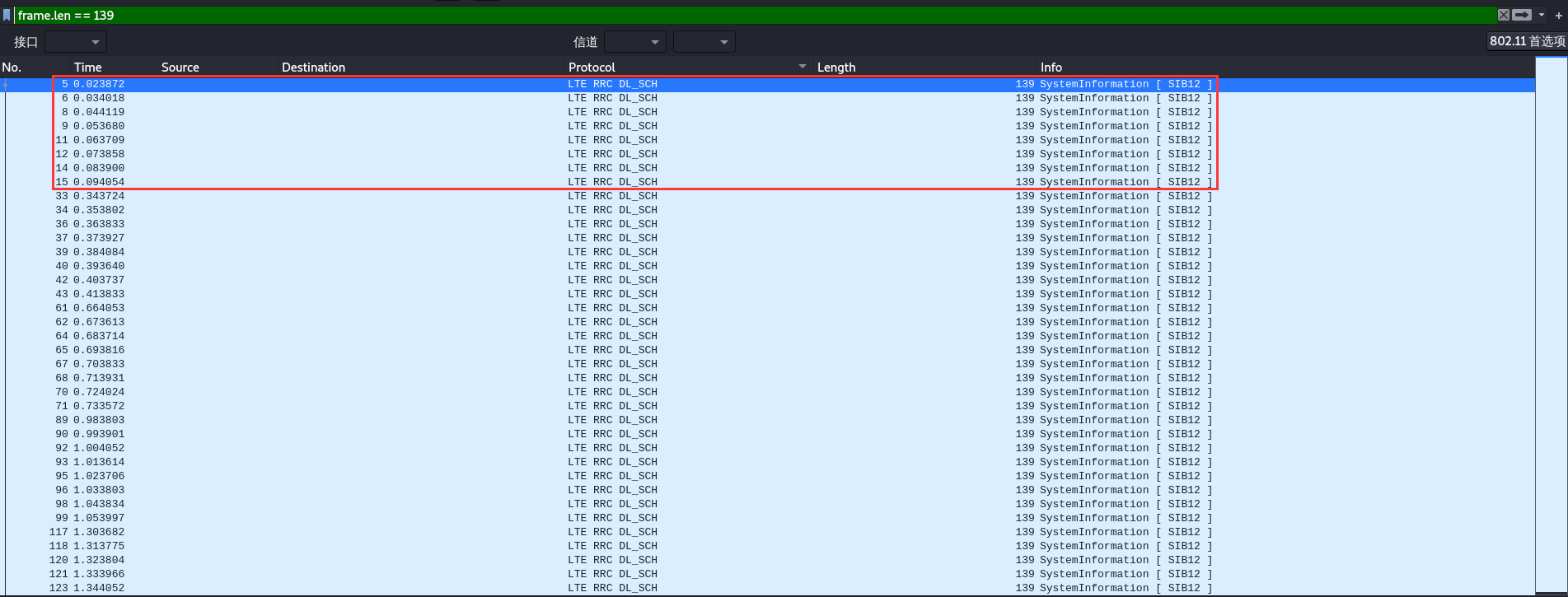
得知每条消息的Bit2Bit3是GSM7编码,且是小端序,根据这条线索看流量长度为139(frame.len == 139)的即是出现message的流量,且每两条为一组交互,每8条就重复一组。
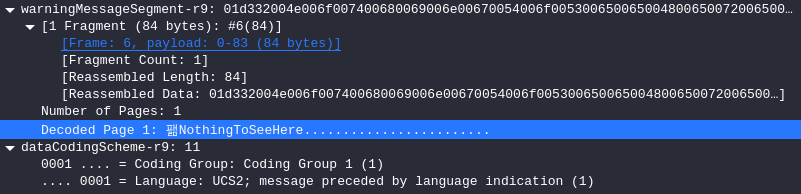
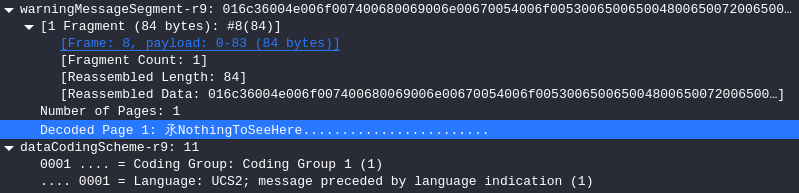
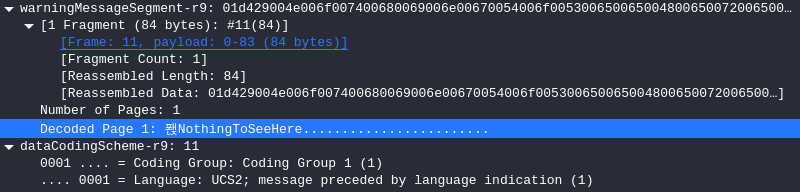

提出数据为d332 6c36 d429 cc20,解密得到SellTSLA,即为flag
# -*- coding: utf-8 -*-
# @Project: ctf-exp
# @File : tmp
# @Author : Tr0jAn <tr0jan@birkenwald.cn>
# @Date : 2021-11-02
def gsm7decode(f):
f = ''.join(["{0:08b}".format(int(f[i:i + 2], 16))for i in range(0, len(f), 2)][::-1])
return ''.join([chr(int(f[::-1][i:i + 7][::-1], 2))for i in range(0, len(f), 7)])
cipher =['d332', '6c36', 'd429', 'cc20']
for c in cipher:
print(gsm7decode(c).replace("\x00", ""), end="")
# SellTSLA


OωO~Misc KING