IdekCTF 2023 Forensics - 2
其余题目
Pretty Good Prank
Author: Bquanman #1805 Giang, a colleague sitting next to me at work, made a prank on my laptop while I was on the toilet. He said that only he can decrypt my file but I don't believe it because I know you can. https://mega.nz/file/Ssd0yLyJ#ChmfKbQJYGutvP39o3fi88Jn-nAzmRZFfgi47e7M_ck
附件下载下来发现是linux内存镜像查找对应的Version信息,制作对应的profile。
# strings PrettyGoodPrank.bin | grep 'Linux version'
Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)
Linux version 5.4.0-107-generic (buildd@lcy02-amd64-070) (gcc version 7.5.0 (Ubuntu 7.5.0-3ubuntu1~18.04)) #121~18.04.1-Ubuntu SMP Thu Mar 24 17:21:33 UTC 2022 (Ubuntu 5.4.0-107.121~18.04.1-generic 5.4.174)查看bash_history
# vol -f PrettyGoodPrank.bin --profile=LinuxUbuntu-5_4_0-107x64 linux_bash
Volatility Foundation Volatility Framework 2.6.1
Pid Name Command Time Command
-------- -------------------- ------------------------------ -------
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -er hackerlor Cirt.pdf
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 rm -rf Cirt.pdf
4895 bash 2023-01-12 04:00:25 UTC+0000 uname -r
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --export-secret-key -a "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 @C?E?U
4895 bash 2023-01-12 04:00:25 UTC+0000 H??
4895 bash 2023-01-12 04:00:25 UTC+0000 ls
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -k
4895 bash 2023-01-12 04:00:25 UTC+0000 ??????
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --quick-gen-key hackerlor
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --delete-secret-key --yes "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg --delete-key "hackerlor"
4895 bash 2023-01-12 04:00:25 UTC+0000 gpg -k
4895 bash 2023-01-12 04:00:25 UTC+0000 ??jm?U
4895 bash 2023-01-12 04:00:25 UTC+0000 sudo chmod 777 chall.bin
4895 bash 2023-01-12 04:00:25 UTC+0000 cd Documents/
4895 bash 2023-01-12 04:00:25 UTC+0000 echo "Noob bquanman"
4895 bash 2023-01-12 04:00:25 UTC+0000 sudo ./avml chall.bin
4895 bash 2023-01-12 04:00:25 UTC+0000 exit
4895 bash 2023-01-12 04:00:25 UTC+0000 echo "Hacked by Giang"
4895 bash 2023-01-12 04:00:25 UTC+0000 rm ~/.bash_history
4895 bash 2023-01-12 04:00:30 UTC+0000 sudo ./avml chall.bin可以看出来先gpg加密了Cirt.pdf然后删除了原pdf文件,在文件中找加密后的pdf文件。
# vol -f PrettyGoodPrank.bin --profile=LinuxUbuntu-5_4_0-107x64 linux_find_file -F "*.pdf.gpg"
Volatility Foundation Volatility Framework 2.6.1
# vol -f PrettyGoodPrank.bin --profile=LinuxUbuntu-5_4_0-107x64 linux_find_file -F "Cirt.pdf.gpg"
Volatility Foundation Volatility Framework 2.6.1
# strings PrettyGoodPrank.bin | grep "Cirt.pdf"
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Cirt.pdf.gpg
https://ufile.io/fetnsp24Upload files for free - Cirt.pdf.gpg - ufile.iooi.elifu.
.Download Cirt.pdf.gpg for free from ufile.io instantly, no signup required and no popup adshttps://ufile.io/assets/img/stats.jpg
https://ufile.io/fetnsp24#!/ZG5e5oHSDUpload files for free - Cirt.pdf.gpg - ufile.iooi.elifu.d
https://ufile.io/fetnsp24Upload files for free - Cirt.pdf.gpg - ufile.iooi.elifu.
.Download Cirt.pdf.gpg for free from ufile.io instantly, no signup required and no popup adshttps://ufile.io/assets/img/stats.jpg
file:///home/ubuntu/Documents/Cirt.pdf.gpg
https://www.google-analytics.com/j/collect?v=1&_v=j98&a=372898305&t=pageview&_s=1&dl=https%3A%2F%2Fufile.io%2Ffetnsp24&ul=en-us&de=UTF-8&dt=Upload%20files%20for%20free%20-%20Cirt.pdf.gpg%20-%20ufile.io&sd=24-bit&sr=1176x885&vp=1097x756&je=0&_u=AACAAEABAAAAACAAI~&jid=251787228&gjid=2045659215&cid=152952070.1673495864&tid=UA-73416834-1&_gid=124608272.1673495864&_r=1&_slc=1&z=179350732
file:///home/ubuntu/Documents/Cirt.pdf.gpg
gpg -er hackerlor Cirt.pdf
rm -rf Cirt.pdf
home/ubuntu/Documents/Cirt.pdf.gpg
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
home/ubuntu/Documents/Cirt.pdf.gpg
https%3A%2F%2Fufile.io%2Ffetnsp24&data%5Bname%5D=Cirt.pdf.gpg&data%5Bfilename%5D=fetnsp24-cirt.pdf.gpg&data%5Bslug%5D=fetnsp24&data%5Bsize%5D=601.2+KB&data%5Btype%5D=other&data%5Bexpiry%5D=4+Weeks&data%5Blocation%5D=23&type=uploadqI25Nq3AXDEzuH5i03D8DRj6K2-qWa4W+5Ke1zv7eFIps6PMXRmCTmfh+qIs7i+2Ahg7L2PkKjFW0sTHW9Ae9HPnRlmMencVsN1QkOXpNBSqFv1eNaBzYpIwfzX9H-hn+KihT8za3vJs6e9skrWmIj-Ym6q65a-Oqv1atq+yfZag-xk59lQySl25MeC7ENQsQLgS3y0l3MNRxS5fx5EYttaNwCdiq5rzMIxGtfc3RpicPdzlBDFZjfrag5e$Xro9jkPJ9uRWuRYzfqIzaBDm+L9zPe-Cr6D3lzKIJd+ltIEZIcSB9DDf15kpYfXAasOdX3jOECV+hq8jtApimgX1q0ma2S7YVcOMTlAfjv9pVat2bAMSuKmVDOScNQbuvm27MmaROaVwwPwJ+5DkeuglW2N7+BVIPWl$ajb8FIwaWmTPGxFSi4Inn51G2kx+GI5VF3lD7F9VnAnV2GiaFiJ+OF9hc+Egfenxm9ppiOrFevwCEjNsn25FQc7iEPvO2Bfq5l+nxN8stdtsCoWl0jL+CsqSH0wHE2V40DmZAc54$BaTWqqbpO+45TtOFIcMblK3bs$mL1u6Mh3NiEWwu+3XnDfaw5KlfTMvgCI8ubaAQDK0LqLzQOC8fXXSuiGGXdsMJ2L8wQ1B0zW+1$TxvlWp0GABVAcJt749+8xXRFBrXn1E5+grlg3IVvarxZX3qMRmOouxnN6sMFJI1tgSuBJ7nJH+xOTuQaYangdqqZquWTsyIpunfaeqTPM610ZA366biHrIIw4nErzjYHLJZk5LD27$F14ZeMmtOHrmrnAMq6Q2AWSKIXukMdP1+fQ0SFV5vMs1j2bSMeKAtp7MQZSdlw$537EjNnkDM3lzI16pCEAMRNgGdICCdDnC4pR1kL+pDcncwkCkyuNDh3RqXJO5apeWQ-75fOquMCV$f9cWcyDigQRt8Ef6NrSqgWM6EWQg37TR-t6lJancN-32K16WQ1Pu-Wq5uFhGJ6n09QTIRqGB0ogkWVucbw4SPZiRGf-mGWHlFSyZcKL+IC$ue24nXRH5Ppel1a6F1VtCMqKSha6qGbKEF80cH4pcDipmxCKAl$kCPBmMbtS8yNtsnn0SR$ty+ufNFkcHz8w+HGVF51KTOZ+GHomgaragX+q7vdM5Z6Rk3tFoFwXHTNrl0TznaqF4hBh62Tc5NOHJvNNzEDEPME-J6d0RktoC0mKaHogzc$vtQ8j$zDcZKcgjQbt07B3e4VDE3cX5sN6PXJr3c80pX3jegIjh7XTSWc1Wt1jap+ZVeHlwvXyE7rKeHgERJf6qGtBzngScr2JCg4r2fHBq9GuECB2FO2DrEBc-NmDxBnyafA-p$bGmzchuEpRCpwjYwtA3Fk$atiYXDPL-NDamjDMJd0S$Ox$wZWDuxfG6DiyZLBI0AkI2qF9ks+$FMh0a3RfW+nSK-wgRbcdXxcO795d$5vOIJP12iDncpOF+08DqFXxE4suuFh69OZBW13OH+i2cb8XLB7a7LHsHb8tL41-oKDwjRZ$OrpGjiOu-pXYeFo7nxxe-OWJJzWkr1mghja-8pYs0qSJCHe5GyqISovPK$oNW0KzRJX5DgKAyel2BKCNWKjcnXDtN3qmQGvamk$jY5SEJfGHQJfYNKkAlnXVQTS84yWTKb5$S1nSJ9efKI8BTuYynsxoZJdXcPJKuK-FQqt5RJL0YPQaAHNdLRYXh0YsYg+$y0gtFvO3$aE0$Sch6h9va3$D$aowz3V78va721q0qQKvOjydOnGvzg31c2+5BV87yce3+lb7OzHhOT75EdN$XecjE2Ou+tiQl$O6XiaaOiXFOIXIOukCCRED9Vyt1+OFDt7A51G-ai7IY5X8brax7uXu+0$7bd3qN+E+Ox$D4d33x1ci$eT7E7lV+OcT7TcNDCHC3STCc8p$OaO8M+Oinp5s6IOo6xfnpp7IOO8+q1M+OIyoiD+79gcIO67x66nTkDsSj56T+tn63$XzXSNeNnqhzac+Om+gnun67l5ino+blgyu+v563as1GRnT5NnHXalF5zC57H7Qnm59l8cpGDyicNca$57hn6EuraE66qNg5AI366AAFSFdEo8$E8+RY1b7l1Ei2gR86eSCyDc8m0ipRoR8zRa9+$Y0+lhuISyN1va$b$8AOnB76obDlAr$HvOac5BD$1M5B7v5YD4ChHpRMgpnEeceZ3xcRjfgGvjQmC0t+N6e$Cnm60E+hHO-K8AajOo+ujOwji+wSql8MgxhYSce6A8RGa++cvoR+qJbX5yv2bBq5wJg-vaevHht-t8sKvO$Ba72v6Ed+rXbOj5D+aXN21s29Qi6fF2vfurwggf9+nfunDfR+$Bclufmfzf6bACAm$iHf8fOwl8u+rL5ixwofON2cR8OB$fb3AwTfIfOwihFh6txtuwIletmyHDhM+f698t6mdNqlItiXAt9wOwF4whF+e9x+aMutIlDMNt8E7VR72OwtIpq9TwVcuIeczmSThDHBe3rZ$iOeQl-r5Ga5ag8YhhtY+Eg5wc2DIRHOpg9JnjSL0Kh2sgx3wSb3$XjF55RYRS5thW-aFCjDlDxy7WFZSK8jxqDCwyn4j5a5wu1l3$AE3nc5cTni6ls+jy2kw7biF267dWNya60Fu2m297a18hHxQS$OeldnAEAERZeajKTLQpA1ofwQhtD4RX1MhHHEwHonj+a$QT-aNHHchETlr1x1ievL6NcLx1TXqlwrcVAO3rDLNEafF+wfj+drhq9q9+2qxYsLugxqRHml$+Sb1zA+$tlQiQHHiXhq8Q9cAvIlSzpHx1zcuDomsNj1H18qHDOJDHhkRqOlOE+EjVnBRMb-5HHTCr$7N8vmClz1zqD+RXAC0klFbEwyqCai6QTN$g1i0kjazHxrxXdrmYt9ugvOwSSri9l7SrokFSrZqp773mrvSK2pcz8ziXa-gziedpaS1OVzTG3rni0zjzbz9ervHj-f9zlzxzxrAOAp3+rzxGOGFQAOnjjsnX2s$OwGuzu8S3b8nY3x0ATG6PnF1M5ViA9TwXeOjO2VF0rVTORMsVohIKFVlAFG8N9Gg+7NFNuAoZvp6ZSFaraEepAAuNTGi8tBHzHNlKb9uVFBiANvmfxNNBmGdsv2gzNEei+Ydzxqq3Nc0OgZvGlz6juIefQGF+Rte2Qu1tgzuNn6AGzven87axix6ya6gkpugzH9aF8XS8n0zv29AQpIS+8R+x6ZOtt0iK73myoxHZo6bXC3zBHZi+-ycwlR0lDZzh$1mc2RFBe+nEjXrSlDgSRGqlS6sBsZNSuk2sDioSlCxyAgTiAOAPpS8tquw0pCz0Ffjzzum25jwum2pvaPFf7VC0lzH9n1cl-32saFIfrSHNQTpC6bw+7dzxHPO8j7pl6SmBOZO8rIwZ1Lc4rSN6R62CgdTdFgTCOOrSx71zq0eieSOO$3SsIZAsFsFPTdOAddQTH9dnqfDIeeawFZzdSZHsIAV+3+SYpm+raxlPox9LV6v6rzb4mk7VaKd4iZs+ew+xOdxdiaDzoVxVoelz6-83FBj+axH-Fsw+jOgeiKax9LSiOmmi3Kt+Rm66nsQTiZxlrB6bRS7qu2bxHKzNijgz8JzK83O0OxO0F43+rJ6EAdD3mzlzzszBzszJOy3f3+adbxF5npe$0JltbrOBz8+GrB8k8baXd-FO1TH3lzIBudi8+xFz8ozITb8$zveAbxx
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
rm -rf Cirt.pdf
Cirt.pdf.gpg
UYuHB8","s":7382,"d":819,"i":"iframe","p":"h2","rs":0,"re":0,"fs":7382,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":8201,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://accounts.google.com/ServiceLogin?passive=true&continue=https%3A%2F%2Fwww.google.com%2Ffavicon.ico&uilel=3&hl=en&service=mail","s":7494,"d":2418,"i":"img","p":"h2","rs":0,"re":0,"fs":8582,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9912,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://accounts.google.com/ServiceLogin?passive=true&continue=https%3A%2F%2Fwww.youtube.com%2Ffavicon.ico&uilel=3&hl=en&service=youtube","s":7495,"d":1867,"i":"img","p":"h2","rs":0,"re":0,"fs":8581,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9362,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://www.google-analytics.com/analytics.js","s":8353,"d":1244,"i":"script","p":"h2","rs":0,"re":0,"fs":8353,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9597,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://partner.googleadservices.com/gampad/cookie.js?domain=ufile.io&callback=_gfp_s_&client=ca-pub-8453236626207385&cookie=ID%3D6c3c38214c3d11e0-221667613cd90034%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MaavfebTbcV0fvUCrQh84iOMKlixg&gpic=UID%3D000009073137e031%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MapNlemtyKc2whoJwyxawxHlNycXg&gpid_exp=1","s":10526,"d":246,"i":"script","p":"h2","rs":0,"re":0,"fs":10526,"ds":10526,"de":10526,"cs":10526,"ce":10526,"qs":10705,"ps":10770,"pe":10772,"ws":0,"ss":0,"ts":693,"ec":32,"dc":12},{"n":"https://adservice.google.com.vn/adsid/integrator.js?domain=ufile.io","s":10647,"d":896,"i":"script","p":"h2","rs":0,"re":0,"fs":10647,"ds":10647,"de":10647,"cs":10647,"ce":10647,"qs":11486,"ps":11543,"pe":11543,"ws":0,"ss":0,"ts":1103,"ec":100,"dc":107},{"n":"https://adservice.google.com/adsid/integrator.js?domain=ufile.io","s":10650,"d":1093,"i":"script","p":"h2","rs":0,"re":0,"fs":10650,"ds":10650,"de":10650,"cs":10650,"ce":10650,"qs":11648,"ps":11743,"pe":11743,"ws":0,"ss":0,"ts":778,"ec":100,"dc":107},{"n":"https://www.google-analytics.com/j/collect?v=1&_v=j98&a=372898305&t=pageview&_s=1&dl=https%3A%2F%2Fufile.io%2Ffetnsp24&ul=en-us&de=UTF-8&dt=Upload%20files%20for%20free%20-%20Cirt.pdf.gpg%20-%20ufile.io&sd=24-bit&sr=1176x885&vp=1097x756&je=0&_u=AACAAEABAAAAACAAI~&jid=251787228&gjid=2045659215&cid=152952070.1673495864&tid=UA-73416834-1&_gid=124608272.1673495864&_r=1&_slc=1&z=179350732","s":10745,"d":888,"i":"xmlhttprequest","p":"h2","rs":0,"re":0,"fs":10745,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":11633,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://googleads.g.doubleclick.net/pagead/ads?client=ca-pub-8453236626207385&output=html&adk=1812271804&adf=3025194257&lmt=1673495984&plat=3%3A65536%2C4%3A65536%2C9%3A32776%2C16%3A8388608%2C17%3A32%2C24%3A32%2C25%3A32%2C30%3A1048576%2C32%3A32%2C41%3A32&format=0x0&url=https%3A%2F%2Fufile.io%2Ffetnsp24&ea=0&pra=5&wgl=1&dt=1673495979418&bpp=146&bdt=3957&idt=3565&shv=r20230110&mjsv=m202212050101&ptt=9&saldr=aa&abxe=1&cookie=ID%3D6c3c38214c3d11e0-221667613cd90034%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MaavfebTbcV0fvUCrQh84iOMKlixg&gpic=UID%3D000009073137e031%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MapNlemtyKc2whoJwyxawxHlNycXg&nras=1&correlator=2014484782430&frm=20&pv=2&ga_vid=152952070.1673495864&ga_sid=1673495985&ga_hid=372898305&ga_fc=1&u_tz=-300&u_his=4&u_h=885&u_w=1176&u_ah=858&u_aw=1109&u_cd=24&u_sd=1&adx=-12245933&ady=-12245933&biw=1097&bih=756&scr_x=0&scr_y=0&eid=44759875%2C44759926%2C44759842%2C44773810%2C31071399%2C31071264&oid=2&pvsid=757429025989270&tmod=2026707715&nvt=1&eae=2&fc=1920&brdim=67%2C27%2C67%2C27%2C1109%2C27%2C1109%2C830%2C1109%2C756&vis=1&rsz=%7C%7Cs%7C&abl=NS&fu=32768&bc=31&ifi=1&uci=a!1&fsb=1&dtd=5163","s":12004,"d":891,"i":"iframe","p":"h2","rs":0,"re":0,"fs":12004,"ds":12004,"de":12004,"cs":12004,"ce":12004,"qs":12425,"ps":12892,"pe":12895,"ws":0,"ss":0,"ts":6000,"ec":5157,"dc":18704},{"n":"https://adservice.google.com.vn/adsid/integrator.js?domain=ufile.io","s":12540,"d":81,"i":"script","p":"h2","rs":0,"re":0,"fs":12540,"ds":12544,"de":12553,"cs":12553,"ce":12553,"
Cirt.pdf.gpg
https://www.google-analytics.com/j/collect?v=1&_v=j98&a=372898305&t=pageview&_s=1&dl=https%3A%2F%2Fufile.io%2Ffetnsp24&ul=en-us&de=UTF-8&dt=Upload%20files%20for%20free%20-%20Cirt.pdf.gpg%20-%20ufile.io&sd=24-bit&sr=1176x885&vp=1097x756&je=0&_u=AACAAEABAAAAACAAI~&jid=251787228&gjid=2045659215&cid=152952070.1673495864&tid=UA-73416834-1&_gid=124608272.1673495864&_r=1&_slc=1&z=179350732
CCC129/pogothere.xyz/asd100.bin","s":7330,"d":1835,"i":"fetch","p":"h2","rs":0,"re":0,"fs":7330,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9165,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://pogothere.xyz/","s":7332,"d":1226,"i":"fetch","p":"h2","rs":0,"re":0,"fs":7332,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":8558,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://eoseurlingeringont.com.ua/utx?cb=nVmik3mn9vWg&top=ufile.io&tid=963260","s":7336,"d":865,"i":"xmlhttprequest","p":"h2","rs":0,"re":0,"fs":7336,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":8201,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://itwasbrghttohi.com.ua/RVNISDFqbCs7DCEWICVoEh0KLXcPCR94SWBhDh1dEzIcEAQUBg4BFzE6LHUIc2B6fgFjIyEsDHR1OzxQMSY7dQBjOiYuXnh1PnUAa2B8ZgJ0fXpuRHhibjxBJDR1eRc1JzwkDHRlf3sFfGZxfwh8Zns","s":7353,"d":814,"i":"img","p":"h2","rs":0,"re":0,"fs":7353,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":8167,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://www.facebook.com/login.php?next=https%3A%2F%2Fwww.facebook.com%2Ffavicon.ico%3F_rdr%3Dp","s":7354,"d":5438,"i":"img","p":"h2","rs":0,"re":0,"fs":7354,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":12792,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://eoseurlingeringont.com.ua/ZzRCVEoGViE5dQYJIHI/FVh/cXghEXASLlRCNWA/AlwtPHhUXDp6KQtbNzAsFVssIGQJUTZxeCFlEBAuFWYHYCQwdRc9KTN2JxB5CwchMxg9VyxhIz9mJSYDI2UJEwlWBwkBfwN/OzN4ME0PBisjdgwQeQteIQYPL34RFSAkX3I8AyRXCQMnLkILEhwwVwUzPTVDEyIpHWIkEzAEDAw4fgF4ODwjNlMyYQMeQAwVIwBdCAYAPXUsIDslBHdmLApMEgMkMUYmZxwoUCxgMjFmdiUFDXERAws9RiYzKS94ERUyMwR3ZiwNQxIMGBMAIRYAPnYvIHglTG8/MwYHJmYfVGIlMAhSeyY6fg1hJTM8LmMHEgY/bmdmCANlJjYuPwFzESYLBAkXeyFwKx0iN3YIDgsJbnMTHBNdDWchIBIoJyUJRH8nI15ZO2IlAUYuHB8","s":7382,"d":819,"i":"iframe","p":"h2","rs":0,"re":0,"fs":7382,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":8201,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://accounts.google.com/ServiceLogin?passive=true&continue=https%3A%2F%2Fwww.google.com%2Ffavicon.ico&uilel=3&hl=en&service=mail","s":7494,"d":2418,"i":"img","p":"h2","rs":0,"re":0,"fs":8582,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9912,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://accounts.google.com/ServiceLogin?passive=true&continue=https%3A%2F%2Fwww.youtube.com%2Ffavicon.ico&uilel=3&hl=en&service=youtube","s":7495,"d":1867,"i":"img","p":"h2","rs":0,"re":0,"fs":8581,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9362,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://www.google-analytics.com/analytics.js","s":8353,"d":1244,"i":"script","p":"h2","rs":0,"re":0,"fs":8353,"ds":0,"de":0,"cs":0,"ce":0,"qs":0,"ps":0,"pe":9597,"ws":0,"ss":0,"ts":0,"ec":0,"dc":0},{"n":"https://partner.googleadservices.com/gampad/cookie.js?domain=ufile.io&callback=_gfp_s_&client=ca-pub-8453236626207385&cookie=ID%3D6c3c38214c3d11e0-221667613cd90034%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MaavfebTbcV0fvUCrQh84iOMKlixg&gpic=UID%3D000009073137e031%3AT%3D1673495866%3ART%3D1673495866%3AS%3DALNI_MapNlemtyKc2whoJwyxawxHlNycXg&gpid_exp=1","s":10526,"d":246,"i":"script","p":"h2","rs":0,"re":0,"fs":10526,"ds":10526,"de":10526,"cs":10526,"ce":10526,"qs":10705,"ps":10770,"pe":10772,"ws":0,"ss":0,"ts":693,"ec":32,"dc":12},{"n":"https://adservice.google.com.vn/adsid/integrator.js?domain=ufile.io","s":10647,"d":896,"i":"script","p":"h2","rs":0,"re":0,"fs":10647,"ds":10647,"de":10647,"cs":10647,"ce":10647,"qs":11486,"ps":11543,"pe":11543,"ws":0,"ss":0,"ts":1103,"ec":100,"dc":107},{"n":"https://adservice.google.com/adsid/integrator.js?domain=ufile.io","s":10650,"d":1093,"i":"script","p":"h2","rs":0,"re":0,"fs":10650,"ds":10650,"de":10650,"cs":10650,"ce":10650,"qs":11648,"ps":11743,"pe":11743,"ws":0,"ss":0,"ts":778,"ec":100,"dc":107},{"n":"https://www.google-analytics.com/j/collect?v=1&_v=j98&a=372898305&t=pageview&_s=1&dl=https%3A%2F%2Fufile.io%2Ffetnsp24&ul=en-us&de=UTF-8&dt=Upload%20files%20for%20free%20-%20Cirt.pdf.gpg%20-%20ufile.io&sd=24-bit&sr=1176x885&vp=1097x756&je=0&_u=AACAAEABAAAAACAAI~&jid=251787228&gjid=2045659215&cid=152952070.1673495864&tid=UA-73416834-1&_gid=124608272.1673495864&_r=1&_slc=1&z=179350732","s":10745,"d":888,"i":
https://ufile.io/fetnsp24Upload files for free - Cirt.pdf.gpg - ufile.iooi.elifu.
.Download Cirt.pdf.gpg for free from ufile.io instantly, no signup required and no popup adshttps://ufile.io/assets/img/stats.jpg
https://ufile.io/fetnsp24#!/ZG5e5oHSDUpload files for free - Cirt.pdf.gpg - ufile.iooi.elifu.d
Cirt.pdf.gpg
Cirt.pdf.gpg
gpg -er hackerlor Cirt.pdf
gpg -er hackerlor Cirt.pdf
rm -rf Cirt.pdf
Upload files for free - Cirt.pdf.gpg - ufile.io
Cirt.pdfX[K
Cirt.pdf.gpg
Cirt.pdf.gpg
Upload files for free - Cirt.pdf.gpg - ufile.io
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
Cirt.pdf.gpg
Cirt.pdf.gpg
Upload files for free - Cirt.pdf.gpg - ufile.io - Mozilla Firefox
file:///home/ubuntu/Documents/Cirt.pdf.gpg
Cirt.pdf.gpg
uments/Cirt.pdf.gpg细细阅读发现加密后文件发送到了https://ufile.io/fetnsp24,下载下来即可。密钥找了半天找不到,搜索字符串可以在内存中看到,密钥就在内存里。
# strings PrettyGoodPrank.bin | grep "PGP PRIVATE KEY"
-----BEGIN PGP PRIVATE KEY BLOCK-----
-----END PGP PRIVATE KEY BLOCK-----
私钥dump下来,有密文,有私钥,缺密码,pgp2john结合hashcat打
-----BEGIN PGP PRIVATE KEY BLOCK-----
lQWGBGO/g7oBDADnJpOQBh/cd7ZltYKfibHHhxesviCVske49oVIBxJjjDUrdqlj
1NqBNgEu7xVKY5lW3KMYIXgz099zoLedIDvlV9+nwQ+ig92wLyrs51jLsKUfrn/o
tnVkwpRgnaxFtIT5S/qozlQoGTXW4l2BKeDH2OIuAhhHeiJ1C61EO8rBvoF7VRIs
Y4Rx5/nByWpukZKhHfE6zcjfVVj5vPElA6eeVwd71NhdIgCpOyXoauVHtLYwe8pv
M3RqZiJ6eTVxDSYc587fJfZhYbMmeYpyggEOeI5scn3POFhiugv3AnntU2XsZiQc
SzK5ME086SPTU0s2AlBb/8siWz4+6GTHb2kalYRWFJeTeMHS0BQ1aP1XZU0wHZPj
USQA/joEFHrGUayRbzzv7OpHV1wjXDJsa9TOvAa1ptkyAmM5k70Pd1A4hpxJY/Ea
ETICxpe8PHKRg5BhP6OKDvJ1sJX8yVvDAkuY1VEXZTGVNswkeYzxTzQ8tdFlMDO+
kmHSYIzTyxGcwTkAEQEAAf4HAwJDGB4Fj5nQAf+sco/FgdiZoBLgCauNWsbdpiTC
utWp5GvvOuzkmmw/Rk8zwPVzcvBNL3YP/pL/ImrRmjX9PSaIwV6WdYiDxxo1LaPM
8JDcwsiuxTRGjIollnE7SPR62iE1scIyhmu6ia5QT2ioky1M5yxgIoBjqI0Zp3t7
/RPe2Ql0/HUMuvEg+guRry2MsEyDXwkroQqMjlE7ZCXwS4kjkyOlNWgKSkbGo1b4
oZrjai+cgfilkvyxgdBLSP8R7GDezhh8dr3hMaqfe3JhanRMMJHLsHkRErwkOip8
Fxl7p/Awpg27NnlSiz5WoJ6PnJ2t4155Wl1VjAfUp5ZSjIgqsSfz5AbMT5y6mmRq
u/ULM2yf1KKcfuYwub1B3rdC9M+FPmuojFdjVL7MNwWpKMn7+yYSLdxmUim+4K+X
c/ueiqBuMfTl+isQkbetm6CAwLtXf35fQEjTgDAZ2Hp1N3NmC1153KUFXBfJIX7k
o/rtHQ/pA1SO8aDf6XenHr9tCxBD8oSPGX808q2Rtg16Tm8OdgIGaSy2k3/mF84f
Ep5O/Iak4b28Xv9bWQpuXYHjZYEOiKVw0kz1B9osckkQAwS1kunmpbNnHP78Iqs0
B+9fjNmhPmG/cM+5hdXbUxmbUK7CgWPQk745q/uc6kDTabTAGQLsYB1v05AFTKzr
xIi3uEuyTaEcah8hK7m5EWqIkiAZjcGjVPjychaipjp+oQCDkbb9W+cJ9ySFAqqS
kKmk7X3DdVejbZeVdYDRfVDLbhGGpwW8ADHtPf13VeBdClOjFpFZk8CT+HShKPR0
csKdQTMVvakHiUEFlkKYiImrFEJaueOh1XygodaLTYMyi7sC37+RM/mBm5WwCHaN
MkDSfhpnIeHQgFSlXyiGrht+FYly1F4CkpBvcBDldRCz4EslOaz19orhdBEe2qbs
o/7E+WGeuFY8DwMojVc3SMe/2G5eTGCbeUJwFRlvIl9IKWFpeUJINlJRUe8kIXH7
Dq7mm/qrWRpl+P7+SDhPTUXPwjeQ0QvKWRxgNl8MMy/z6/YPvsSA9kUj1vXsZwi1
j1TOFZq7JskpKSACiF5MIPW9/nNGwBsen5ZnRpM394lzu/BRm81dAV7rtRksWV9K
nDnScU86Ine/o3yz5M45Nsn15vwZS4WajA11PAByg5ugrwPNweD0gZX5rcnZAHjP
Yce0IH0zHDUCaw/wf3/QfKuAb/Tn3eSvxvnc0AkUXExsWtc2WqKFC9xeYysZNlRp
6Nc9GybJ6XREFfapMMxiSlgQLe9q15yee1w3SADivv5LJBlnAWt5yJPe/PbECZ0Z
kH3JLLp4aP4MNC7OmmkKuC4jsfpw4V1Z0rQJaGFja2VybG9yiQHUBBMBCgA+FiEE
WCU6oOfem6XMQDKgzzn264IIJIkFAmO/g7oCGwMFCQPCZwAFCwkIBwIGFQoJCAsC
BBYCAwECHgECF4AACgkQzzn264IIJIkmdQwA4B6ZiMXbjmyr5geoDQvzrwTNbD7v
N+FFYEqZbg8TAJKjnHcXA0QSPLk/rwLczn+vSatG6YltzMmKb+OOknuvJWahwrTi
KG+7f9LZr0fpwpyjrzOiwJPDahxOnoYx1j0oeCWIcygGYnvMmCvvRvVBiEEEhONS
Bqx3AlRtEpreKsCFEX5eOsFc9jmI+FMalLyhxOxLZbU5qsiFOJZTQmbRXAAj6lta
fIC4tS+Vv1xRZRzxkOUR4msDKc+KszK3LgWByOr9n3h0n6C4/KO6aARsMDh3jeZ6
fKXtV368kKTvQE2fri6l7F7paZ4uOvKa1CPlXq3todEaRy3L7uDfHr7L5TCwILCq
5e5a8wfxz/zVjaBHZnYvohbN7+dTxvYBxe6AwZQ5YxbUbPqKh9FidjzVp4JNwUf8
4FeRSqYIvUNS3o4f8h0+lReFdCU1lM59DVjFUzUXv6N6nWcPvrYYA/bvRoJ6DZDE
yaMydilFbFTv7NSml21cDo/fZfaoZPwYuHp7nQWGBGO/g7oBDADH36kj+37wJtO7
6p/JDkPdA9d8DQ4nTJiPGq++F1sySlGjCc6MGnCZ+M72OGAarkfikscfMgQdnvEx
K0lcsXMp7yocZ6v/d7tSlXKjcghclngdDCuo5YDuQCgmVDG4UVEW8lZ+NZU+2Ve4
VDnl3NPt9H6wETw1gUMoWRuT8LXnXPEfY0VhPuQ3QniT7K+5h3k+OF7GsVDxwCVH
M/k/XH/v3Xp0p9nm7JtXd82C7J5M2vBnNJYRNDttUoEjRIO3wGb6FPLqK8Pet1FJ
rYrJYs/+F/C33ushfLW/eds37D8IIbA2UvPg8ZNiqMb53lYLJghtlduoEHK4r1R8
y0L9b4V8FP9tPzQDh33gl58ScJXgQxlYfeq+viUecAbcICem1Izg3Cgb8KynoQWc
yw602vYDmvX+go6gvCgNHsmwkYkEnqCnAqvIMrG4Pd7/1DT4xmhrrBGCYPZID5MG
I4BtS0Bnz1rIoG4rNI6SLJP2OioLzJTFmDhU6DeHsNHqYMWo0mcAEQEAAf4HAwIe
ObV7an3Dqv8ry4hI4DgQ1OJxppXD4Uce5+hzLZnEZ1qbxN4prLc/TLkc3tHbGYMo
4cl/GiEHOblbgpijUFJ6ATlen7UCx3MQKS2wXjESJpiSVbWofgOOuDILwN83TgHl
KQXzJSG5CkiZJ7qJXpMC0Xb2H9ZQF4+lbbhV3GsKDU0DtJJVI24GBEOaKio2mt+9
NczNpUt4J29ERZaTjxGWCMq81UNa3wNFfmgTdwZJFSaCAO6Oc5RJv0zvjJC3S0+k
g6aGRRN/ITMazTxcbYxW8b0qs7EBR6kHlV9b5AXL0KD/f9SLQOEpyJ11ri9uuepc
j155oMjniUjYhOLkOQstqRk6lklu1wIOPoKXMDD5MIZ+BorNKc9+3vnIQQ7jR9Xl
AJkPclhNoDaDHfsOfra2IaYnX0Q985bhlGqxOERisYI0Nol0WL2DZXwnm2ctmcyT
pIlNsLlL0NFtlDwn1IlO8fYLzKqqfR6qyhfWM/Y8craEnRGRYXL/yEAmFy6OrTDZ
KHz9g19nGjn2rJi3nJPIL3uLbWqmZCkf+CvDXqD+tlthvYEgeIvxEf3UDcllAhxF
myZ8SpNVnpxoIf/jw6Ve7wciocqdg97843iEdPp7OtkKmRRkkDrgssd8pv63RsjJ
jHzGQv2pLlyXmFN9sphaTcTHf90cTf6q9YYOAXvTFLhp5BSaZ+7CBqFRh39vuDyz
4u8JMM6/CFOlBBHemvt6QQvu1iAGHmBXIWFQjE62YXX8UEcDXXHjw+8QQ1G/en+4
DwzupiSkwdUt2jkHUPSaUEdbME3a7zqbJ4yDJAil1AfTBMED7McF8HZgkp6N2bVM
Tyzmb+vT7b+FQHRE8EI3hts83g6uCmKT0DCcgeDoDZktrzDLnChbiMYZO3fib8HX
pl/qMrh1xzfvrbV2L2RSpY0JcZxxAJS+L/GYRwVwr55OA/ZTnFhVthMcmaz5/NuY
KIZdb34sBBunllNYWona9YcM0J7M3/p+GR/EEee901xwAU7Z5lWbE+J3jp4MOWRd
g7+Wu4l5MgeF+mTfiKYWAPdjeg8ZLpYgEsTr2OCFuAAHHOFM5xDZuo8XbMg3J3jg
EpyWYdEHOXrqFbwsXhivYL0dpavtdXNaI8AC6m2GNtOso0ghgw53D7CwefUh0FhS
iTDhsmRryV1LvuH1txJZq3bOJk/cW6JBeMLQw2Q/5S2orvfj1SoboMtSW1mDWSh/
y855KSruCg8AzgDiflXumPK5vL0i8gI6PsQJ/xxUZpEjKJ2VwZyObSEt9JlsCmij
lmqXCEHs998TwL8uuxLmTnXH2yTepbj+iItAL14mbcd1JLtednvUt9EttY5xm6hW
kv6XVIkBtgQYAQoAIBYhBFglOqDn3pulzEAyoM859uuCCCSJBQJjv4O6AhsMAAoJ
EM859uuCCCSJWDgL/2a8nMhxLpCKew3Ht5/OMNeolypBY6w/hXnM5uAlFyLvccrV
X6D0f8E9OElfkpOTGzoS6ZIzpSERTj8xM4jIhMjTWtdVoldHZ4UCb7J8wPPMm+u+
WxP1yjR1VuLr9YUOaKCOGhT9BzseOYu8Uto/NrGXplDiyRse9rMJ/XI8Sh0tADVx
FSu9Dd5h/9Yi1JkHolva1ld2LUO1ILstJ79ohJvisBI/kuSXOya/p63hDknVQ4bw
xJ1ynbMRXIDCWxcIt3Wk0Aiow9l/2nLyxvrI0RvR8EsOeyl6ut2Os5lVesvTBRvd
jTeank8dBokiMF8Q4b+B+r+zWcSlxwyO2AagoJ3TJBuxWLXKEGsXDrwwEHLbrIg+
AfHcpCgs8i27iS/3lHxSzgZbZB5NiaOJCKuq7Zerg9ULtyONhchx8Es8SLU3nY0/
00noUIbWcpb4JRNG4tz0FrfLj3nnnvgwmbzXLugpBRmV275zGx+3yFYzN3xpx0NO
IDcufsWUUAptvV8PmQ==
=LIOj
-----END PGP PRIVATE KEY BLOCK-----在线网站或者本地运行gpg2john获得hashcat可用文件
# hashcat -m 17010 result.txt -a 0 /usr/share/wordlists/rockyou.txt --force
hashcat (v6.2.6) starting
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 3.0 PoCL 3.0+debian Linux, None+Asserts, RELOC, LLVM 14.0.6, SLEEF, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================
* Device #1: pthread-0x000, 2912/5889 MB (1024 MB allocatable), 4MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Single-Hash
* Single-Salt
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Host memory required for this attack: 1 MB
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$gpg$*1*988*3072*a624c2bad5a9e46bef3aece49a6c3f464f33c0f57372f04d2f760ffe92ff226ad19a35fd3d2688c15e96758883c71a352da3ccf090dcc2c8aec534468c8a2596713b48f47ada2135b1c232866bba89ae504f68a8932d4ce72c60228063a88d19a77b7bfd13ded90974fc750cbaf120fa0b91af2d8cb04c835f092ba10a8c8e513b6425f04b89239323a535680a4a46c6a356f8a19ae36a2f9c81f8a592fcb181d04b48ff11ec60dece187c76bde131aa9f7b72616a744c3091cbb0791112bc243a2a7c17197ba7f030a60dbb3679528b3e56a09e8f9c9dade35e795a5d558c07d4a796528c882ab127f3e406cc4f9cba9a646abbf50b336c9fd4a29c7ee630b9bd41deb742f4cf853e6ba88c576354becc3705a928c9fbfb26122ddc665229bee0af9773fb9e8aa06e31f4e5fa2b1091b7ad9ba080c0bb577f7e5f4048d3803019d87a753773660b5d79dca5055c17c9217ee4a3faed1d0fe903548ef1a0dfe977a71ebf6d0b1043f2848f197f34f2ad91b60d7a4e6f0e760206692cb6937fe617ce1f129e4efc86a4e1bdbc5eff5b590a6e5d81e365810e88a570d24cf507da2c7249100304b592e9e6a5b3671cfefc22ab3407ef5f8cd9a13e61bf70cfb985d5db53199b50aec28163d093be39abfb9cea40d369b4c01902ec601d6fd390054cacebc488b7b84bb24da11c6a1f212bb9b9116a889220198dc1a354f8f27216a2a63a7ea1008391b6fd5be709f7248502aa9290a9a4ed7dc37557a36d97957580d17d50cb6e1186a705bc0031ed3dfd7755e05d0a53a316915993c093f874a128f47472c29d413315bda9078941059642988889ab14425ab9e3a1d57ca0a1d68b4d83328bbb02dfbf9133f9819b95b008768d3240d27e1a6721e1d08054a55f2886ae1b7e158972d45e0292906f7010e57510b3e04b2539acf5f68ae174111edaa6eca3fec4f9619eb8563c0f03288d573748c7bfd86e5e4c609b79427015196f225f4829616979424836525151ef242171fb0eaee69bfaab591a65f8fefe48384f4d45cfc23790d10bca591c60365f0c332ff3ebf60fbec480f64523d6f5ec6708b58f54ce159abb26c929292002885e4c20f5bdfe7346c01b1e9f9667469337f78973bbf0519bcd5d015eebb5192c595f4a9c39d2714f3a2277bfa37cb3e4ce3936c9f5e6fc194b859a8c0d753c0072839ba0af03cdc1e0f48195f9adc9d90078cf61c7b4207d331c35026b0ff07f7fd07cab806ff4e7dde4afc6f9dcd009145c4c6c5ad7365aa2850bdc5e632b19365469e8d73d1b26c9e9744415f6a930cc624a58102def6ad79c9e7b5c374800e2befe4b241967016b79c893defcf6c4099d19907dc92cba7868fe0c342ece9a690ab82e23b1fa70e15d59d2*3*254*2*7*16*ac728fc581d899a012e009ab8d5ac6dd*65011712*43181e058f99d001:itachi
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 17010 (GPG (AES-128/AES-256 (SHA-1($pass))))
Hash.Target......: $gpg$*1*988*3072*a624c2bad5a9e46bef3aece49a6c3f464f...99d001
Time.Started.....: Sat Jan 21 22:39:02 2023, (1 min, 36 secs)
Time.Estimated...: Sat Jan 21 22:40:38 2023, (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 43 H/s (6.03ms) @ Accel:512 Loops:8192 Thr:1 Vec:4
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 4096/14344385 (0.03%)
Rejected.........: 0/4096 (0.00%)
Restore.Point....: 2048/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: slimshady -> oooooo
Started: Sat Jan 21 22:38:39 2023
Stopped: Sat Jan 21 22:40:40 2023得到密码itachi,导入私钥,解密文件
# gpg --import pem.txt
gpg: 密钥 CF39F6EB82082489:公钥 “hackerlor” 已导入
gpg: 密钥 CF39F6EB82082489:私钥已导入
gpg: 处理的总数:1
gpg: 已导入:1
gpg: 读取的私钥:1
gpg: 导入的私钥:1
# gpg -d Cirt.pdf.gpg > Cirt.pdf
gpg: 由 3072 位的 RSA 密钥加密,标识为 1785FDD68E2FB7C6,生成于 2023-01-12
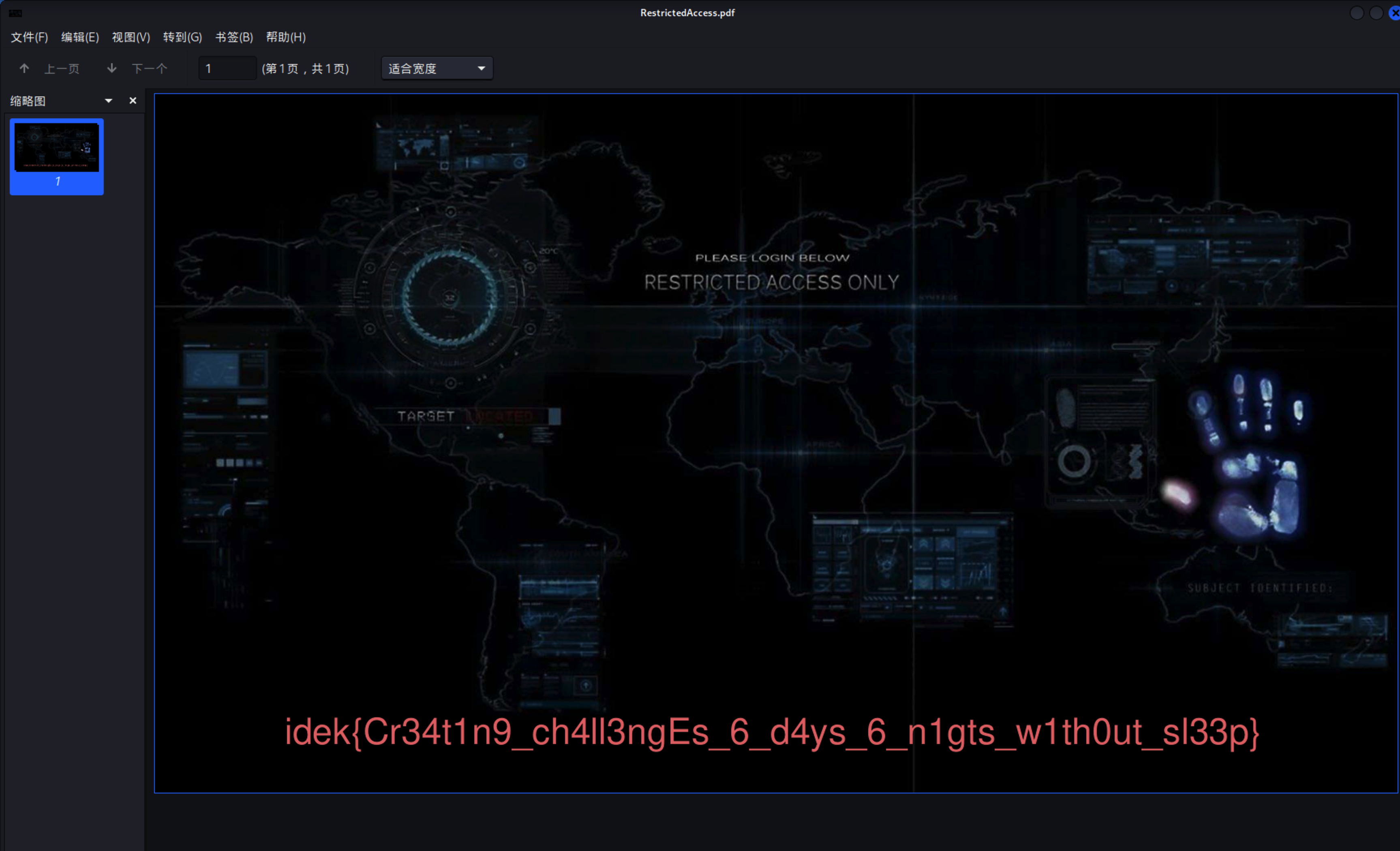
“hackerlor”
flag: https://pastebin.com/5Zh86iu6
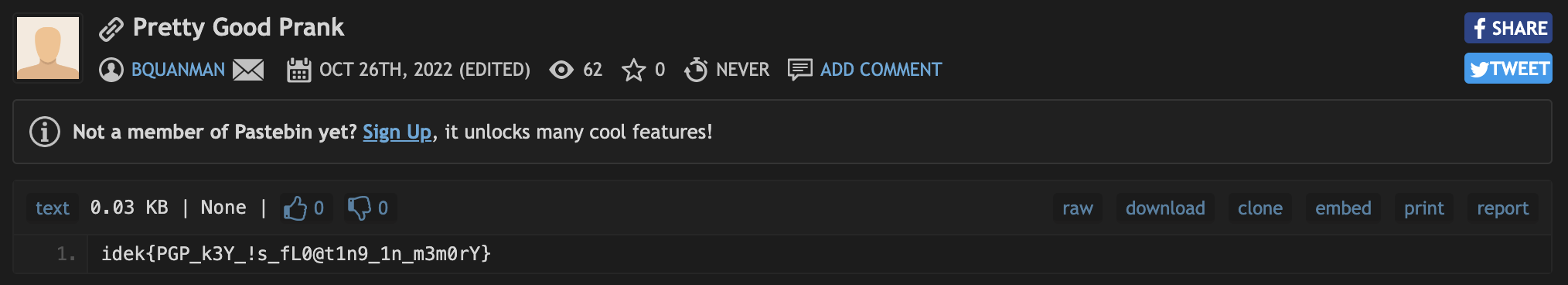
Stealth
Author: Bquanman #1805 A "độc lạ"(strange) incident happened when I had just used the archive manager to password protect my confidential document then a moment later, it disappeared right in front of my eyes. Fortunately, I have a network dump and memory dump on hand Note: archive password has no upper case letter https://mega.nz/file/Ssdk0ByZ#re1QTln9iN7M6bu8k5uZTvlGZhkaH9T-ce1W2R7ammg
流量使用udp传输了一个7z文件,bin文件是Linux内存文件,还是先提取7z并制作对应profile。7z使用低版本的wireshark导出tftp即可。
# strings Stealth.bin| grep "Linux version"
This is the GNU/Linux version of the popular PasswordSafe password manager, originally designed by the renowned security technologist Bruce Schneier and open sourced in 2002.
Linux version 5.10.0-11-amd64 (debian-kernel@lists.debian.org) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian 5.10.92-2 (2022-02-28)
Linux version 5.10.0-11-amd64 (debian-kernel@lists.debian.org) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian 5.10.92-2 (2022-02-28)
Linux version 5.10.0-11-amd64 (debian-kernel@lists.debian.org) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian 5.10.92-2 (2022-02-28)
MESSAGE=Linux version 5.10.0-8-amd64 (debian-kernel@lists.debian.org) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian 5.10.46-4 (2021-08-03)
Linux version 5.10.0-11-amd64 (debian-kernel@lists.debian.org) (gcc-10 (Debian 10.2.1-6) 10.2.1 20210110, GNU ld (GNU Binutils for Debian) 2.35.2) #1 SMP Debian 5.10.92-2 (2022-02-28)
# vol -f Stealth.bin --profile=LinuxDebian5_10_0-11x64 linux_bash
Volatility Foundation Volatility Framework 2.6.1
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
Pid Name Command Time Command
-------- -------------------- ------------------------------ -------
2733 bash 2023-01-12 06:07:58 UTC+0000 history
2733 bash 2023-01-12 06:07:58 UTC+0000 rm ~/.bash_history
2733 bash 2023-01-12 06:07:58 UTC+0000 ip a
2733 bash 2023-01-12 06:07:58 UTC+0000 sudo nano /etc/motd
2733 bash 2023-01-12 06:07:58 UTC+0000 nano /etc/motd
2733 bash 2023-01-12 06:08:00 UTC+0000 whoami
2733 bash 2023-01-12 06:08:04 UTC+0000 ls /dev/input/
2733 bash 2023-01-12 06:08:13 UTC+0000 cat /dev//input/event0 | xxd -p
2733 bash 2023-01-12 06:08:19 UTC+0000 sudo cat /dev/input/event0 | xxd -p
2733 bash 2023-01-12 06:10:16 UTC+0000 cd Documents/
2733 bash 2023-01-12 06:10:17 UTC+0000 ls
2733 bash 2023-01-12 06:10:23 UTC+0000 tftp
2733 bash 2023-01-12 06:10:28 UTC+0000 sudo apt install tftpd-hpa
2733 bash 2023-01-12 06:10:33 UTC+0000 cat /etc/default/tftpd-hpa
2733 bash 2023-01-12 06:10:39 UTC+0000 sudo mv Confidential.7z /srv/tftp/
2733 bash 2023-01-12 06:11:08 UTC+0000 ls
2733 bash 2023-01-12 06:11:21 UTC+0000 sudo rm -rf /srv/tftp/Confidential.7z
2733 bash 2023-01-12 06:11:21 UTC+0000
3373 bash 2023-01-12 06:12:57 UTC+0000 sudo nano /etc/motd
3373 bash 2023-01-12 06:12:57 UTC+0000 exit
3373 bash 2023-01-12 06:12:57 UTC+0000 cd Documents/
3373 bash 2023-01-12 06:12:57 UTC+0000 ATH??
3373 bash 2023-01-12 06:12:57 UTC+0000 ip a
3373 bash 2023-01-12 06:12:57 UTC+0000 ATUH?H?-?q
3373 bash 2023-01-12 06:12:57 UTC+0000 internal_fifos
3373 bash 2023-01-12 06:12:57 UTC+0000 nano /etc/motd
3373 bash 2023-01-12 06:12:57 UTC+0000 rm -rf Confidential.pdf
3373 bash 2023-01-12 06:12:57 UTC+0000 rm ~/.bash_history
3373 bash 2023-01-12 06:12:57 UTC+0000 history
3373 bash 2023-01-12 06:12:57 UTC+0000 ls
3373 bash 2023-01-12 06:12:57 UTC+0000
3373 bash 2023-01-12 06:13:05 UTC+0000 `
3373 bash 2023-01-12 06:13:05 UTC+0000 sudo ./avml idek.bin可以看到读取了/dev/input/event0,然后用tftp传输了一个Confidential.7z,流量是全过程流量包括了ssh连接的流量。在内存中又无法读取event0文件,考虑侧信道读取ssh流量。这里要用到一个vol2的插件。找到ssh进程号,并dump对应密钥。
# vol -f Stealth.bin --profile=LinuxDebian5_10_0-11x64 linux_pslist
Volatility Foundation Volatility Framework 2.6.1
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
Offset Name Pid PPid Uid Gid DTB Start Time
------------------ -------------------- --------------- --------------- --------------- ------ ------------------ ----------
……
0xffff910208af2f80 sshd 2723 595 0 0 0x0000000002dea000 2023-01-12 06:08:11 UTC+0000
0xffff91021d82df00 sshd 2732 2723 1000 1000 0x000000000a214000 2023-01-12 06:08:11 UTC+0000
……
# vol -f Stealth.bin --profile=LinuxDebian5_10_0-11x64 linux_sshkeys -p 2732
Volatility Foundation Volatility Framework 2.6.1
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
/\____/\
\ (_)/ OpenSSH Session Key Dumper
\ X By Jelle Vergeer
\ / \
\/
Scanning for OpenSSH sshenc structures...
WARNING : volatility.debug : Overlay structure cpuinfo_x86 not present in vtypes
Name Pid PPid Address Name Key IV
------- ----- ------ ------------------ ---------------------- ---------- ----------------------
sshd [] 2732 2723 0x0000559a7f449af0 aes256-gcm@openssh.com 895688678410a0b9b358b0b04ab909d49333791e864c89593c66d5ce5083b8e5 40e87818bef3d68c45c9a9f5
sshd [] 2732 2723 0x0000559a7f449c30 aes256-gcm@openssh.com f03b9e6c1b37ec53d89839e85deffb204d9a261076014850399499e913a1b32b dc972db4e5f7e8738ddf57d6然后使用ssh侧信道流量解密工具,解密流量。首先根据内存中的ssh-key要先构建json文件。
{"task_name": "sshd", "sshenc_addr": 94122048527088, "cipher_name": "aes256-gcm@openssh.com", "key": "895688678410a0b9b358b0b04ab909d49333791e864c89593c66d5ce5083b8e5", "iv": "40e87818bef3d68c45c9a9f5"}
{"task_name": "sshd", "sshenc_addr": 94122048527408, "cipher_name": "aes256-gcm@openssh.com", "key": "f03b9e6c1b37ec53d89839e85deffb204d9a261076014850399499e913a1b32b", "iv": "dc972db4e5f7e8738ddf57d6"}工具解密得到如下文件,文件中记录了shell操作,以及读取的event0文件内容。
network-parser -p Stealth.pcapng --popt keyfile=key.json --proto ssh -o dump/
有关event0的部分数据如下:
daa3bf63000000002b3b030000000000040004001e000000daa3bf630000
00002b3b03000000000001001e0001000000daa3bf63000000002b3b0300
000000000000000000000000daa3bf630000000091e10400000000000400
04001e000000daa3bf630000000091e104000000000001001e0000000000
daa3bf630000000091e10400000000000000000000000000daa3bf630000
000021660800000000000400040013000000daa3bf630000000021660800
000000000100130001000000daa3bf630000000021660800000000000000
000000000000daa3bf6300000000aaf70900000000000400040013000000
daa3bf6300000000aaf70900000000000100130000000000daa3bf630000
0000aaf70900000000000000000000000000daa3bf630000000052a80c00
00000000040004002e000000daa3bf630000000052a80c00000000000100
2e0001000000daa3bf630000000052a80c00000000000000000000000000根据数据特性猜测是键盘记录,对其进行解密处理:
from Crypto.Util.number import long_to_bytes
import struct
import sys
lines = open("result.txt", 'rb').readlines()
res = b""
for line in lines:
res += line.strip()
open("real.txt", 'wb').write(long_to_bytes(int(res, 16)))
FORMAT = 'llHHI'
EVENT_SIZE = struct.calcsize(FORMAT)
infile_path = "real.txt"
in_file = open(infile_path, "rb")
event = in_file.read(EVENT_SIZE)
keymap = {
0: "KEY_RESERVED", 1: "KEY_ESC", 2: "KEY_1", 3: "KEY_2", 4: "KEY_3", 5: "KEY_4", 6: "KEY_5", 7: "KEY_6", 8: "KEY_7",
9: "KEY_8", 10: "KEY_9", 11: "KEY_0", 12: "KEY_MINUS", 13: "KEY_EQUAL", 14: "KEY_BACKSPACE", 15: "KEY_TAB",
16: "KEY_Q", 17: "KEY_W", 18: "KEY_E", 19: "KEY_R", 20: "KEY_T", 21: "KEY_Y", 22: "KEY_U", 23: "KEY_I", 24: "KEY_O",
25: "KEY_P", 26: "KEY_LEFTBRACE", 27: "KEY_RIGHTBRACE", 28: "KEY_ENTER", 29: "KEY_LEFTCTRL", 30: "KEY_A",
31: "KEY_S", 32: "KEY_D", 33: "KEY_F", 34: "KEY_G", 35: "KEY_H", 36: "KEY_J", 37: "KEY_K", 38: "KEY_L",
39: "KEY_SEMICOLON", 40: "KEY_APOSTROPHE", 41: "KEY_GRAVE", 42: "KEY_LEFTSHIFT", 43: "KEY_BACKSLASH", 44: "KEY_Z",
45: "KEY_X", 46: "KEY_C", 47: "KEY_V", 48: "KEY_B", 49: "KEY_N", 50: "KEY_M", 51: "KEY_COMMA", 52: "KEY_DOT",
53: "KEY_SLASH", 54: "KEY_RIGHTSHIFT", 55: "KEY_KPASTERISK", 56: "KEY_LEFTALT", 57: "KEY_SPACE", 58: "KEY_CAPSLOCK",
59: "KEY_F1", 60: "KEY_F2", 61: "KEY_F3", 62: "KEY_F4", 63: "KEY_F5", 64: "KEY_F6", 65: "KEY_F7", 66: "KEY_F8",
67: "KEY_F9", 68: "KEY_F10", 69: "KEY_NUMLOCK", 70: "KEY_SCROLLLOCK", 71: "KEY_KP7", 72: "KEY_KP8", 73: "KEY_KP9",
74: "KEY_KPMINUS", 75: "KEY_KP4", 76: "KEY_KP5", 77: "KEY_KP6", 78: "KEY_KPPLUS", 79: "KEY_KP1", 80: "KEY_KP2",
81: "KEY_KP3", 82: "KEY_KP0", 83: "KEY_KPDOT", 85: "KEY_ZENKAKUHANKAKU", 86: "KEY_102ND", 87: "KEY_F11",
88: "KEY_F12", 89: "KEY_RO", 90: "KEY_KATAKANA", 91: "KEY_HIRAGANA", 92: "KEY_HENKAN", 93: "KEY_KATAKANAHIRAGANA",
94: "KEY_MUHENKAN", 95: "KEY_KPJPCOMMA", 96: "KEY_KPENTER", 97: "KEY_RIGHTCTRL", 98: "KEY_KPSLASH", 99: "KEY_SYSRQ",
100: "KEY_RIGHTALT", 101: "KEY_LINEFEED", 102: "KEY_HOME", 103: "KEY_UP", 104: "KEY_PAGEUP", 105: "KEY_LEFT",
106: "KEY_RIGHT", 107: "KEY_END", 108: "KEY_DOWN", 109: "KEY_PAGEDOWN", 110: "KEY_INSERT", 111: "KEY_DELETE",
112: "KEY_MACRO", 113: "KEY_MUTE", 114: "KEY_VOLUMEDOWN", 115: "KEY_VOLUMEUP", 116: "KEY_POWER", 117: "KEY_KPEQUAL",
118: "KEY_KPPLUSMINUS", 119: "KEY_PAUSE", 120: "KEY_SCALE", 121: "KEY_KPCOMMA", 122: "KEY_HANGUEL",
123: "KEY_HANJA", 124: "KEY_YEN", 125: "KEY_LEFTMETA", 126: "KEY_RIGHTMETA", 127: "KEY_COMPOSE",
128: "KEY_STOP", 129: "KEY_AGAIN", 130: "KEY_PROPS", 131: "KEY_UNDO", 132: "KEY_FRONT", 133: "KEY_COPY",
134: "KEY_OPEN", 135: "KEY_PASTE", 136: "KEY_FIND", 137: "KEY_CUT", 138: "KEY_HELP", 139: "KEY_MENU",
140: "KEY_CALC", 141: "KEY_SETUP", 142: "KEY_SLEEP", 143: "KEY_WAKEUP", 144: "KEY_FILE", 145: "KEY_SENDFILE",
146: "KEY_DELETEFILE", 147: "KEY_XFER", 148: "KEY_PROG1", 149: "KEY_PROG2", 150: "KEY_WWW", 151: "KEY_MSDOS",
152: "KEY_SCREENLOCK", 153: "KEY_DIRECTION", 154: "KEY_CYCLEWINDOWS",
155: "KEY_MAIL", 156: "KEY_BOOKMARKS", 157: "KEY_COMPUTER", 158: "KEY_BACK", 159: "KEY_FORWARD", 160: "KEY_CLOSECD",
161: "KEY_EJECTCD", 162: "KEY_EJECTCLOSECD", 163: "KEY_NEXTSONG", 164: "KEY_PLAYPAUSE", 165: "KEY_PREVIOUSSONG",
166: "KEY_STOPCD", 167: "KEY_RECORD", 168: "KEY_REWIND", 169: "KEY_PHONE", 170: "KEY_ISO", 171: "KEY_CONFIG",
172: "KEY_HOMEPAGE", 173: "KEY_REFRESH", 174: "KEY_EXIT", 175: "KEY_MOVE", 176: "KEY_EDIT", 177: "KEY_SCROLLUP",
178: "KEY_SCROLLDOWN", 179: "KEY_KPLEFTPAREN", 180: "KEY_KPRIGHTPAREN", 181: "KEY_NEW", 182: "KEY_REDO",
183: "KEY_F13", 184: "KEY_F14", 185: "KEY_F15", 186: "KEY_F16", 187: "KEY_F17", 188: "KEY_F18", 189: "KEY_F19",
190: "KEY_F20", 191: "KEY_F21", 192: "KEY_F22", 193: "KEY_F23", 194: "KEY_F24", 200: "KEY_PLAYCD",
201: "KEY_PAUSECD", 202: "KEY_PROG3", 203: "KEY_PROG4", 204: "KEY_DASHBOARD", 205: "KEY_SUSPEND", 206: "KEY_CLOSE",
207: "KEY_PLAY", 208: "KEY_FASTFORWARD", 209: "KEY_BASSBOOST", 210: "KEY_PRINT", 211: "KEY_HP", 212: "KEY_CAMERA",
213: "KEY_SOUND", 214: "KEY_QUESTION", 215: "KEY_EMAIL", 216: "KEY_CHAT", 217: "KEY_SEARCH", 218: "KEY_CONNECT",
219: "KEY_FINANCE", 220: "KEY_SPORT", 221: "KEY_SHOP", 222: "KEY_ALTERASE", 223: "KEY_CANCEL",
224: "KEY_BRIGHTNESSDOWN", 225: "KEY_BRIGHTNESSUP", 226: "KEY_MEDIA", 227: "KEY_SWITCHVIDEOMODE",
228: "KEY_KBDILLUMTOGGLE", 229: "KEY_KBDILLUMDOWN", 230: "KEY_KBDILLUMUP", 231: "KEY_SEND", 232: "KEY_REPLY",
233: "KEY_FORWARDMAIL", 234: "KEY_SAVE", 235: "KEY_DOCUMENTS", 236: "KEY_BATTERY", 237: "KEY_BLUETOOTH",
238: "KEY_WLAN", 239: "KEY_UWB", 240: "KEY_UNKNOWN", 241: "KEY_VIDEO_NEXT", 242: "KEY_VIDEO_PREV",
243: "KEY_BRIGHTNESS_CYCLE", 244: "KEY_BRIGHTNESS_ZERO", 245: "KEY_DISPLAY_OFF", 246: "KEY_WIMAX",
247: "KEY_RFKILL", 248: "KEY_MICMUTE"
}
shift = False
while event:
(tv_sec, tv_usec, tType, code, value) = struct.unpack(FORMAT, event)
if tType != 0 or code != 0 or value != 0:
if tType == 0x01: # EV_KEY
key = keymap[code]
if value == 1:
key_label = key[4:]
if len(key_label) == 1:
if shift:
sys.stdout.write(key_label.upper())
else:
sys.stdout.write(key_label.lower())
elif "SHIFT" in key:
print("SHIFT")
elif key_label == "LEFT BRACE":
sys.stdout.write("{")
elif key_label == "RIGHT BRACE":
sys.stdout.write("}")
else:
print(key_label)
else:
if "SHIFT" in key:
print("SHIFT")
event = in_file.read(EVENT_SIZE)
in_file.close()
# archiveSPACE
# managerENTER
# SHIFT
# cSHIFT
# onfidentials3cr3t7azLEFT
# BACKSPACE
# RIGHT
# pSHIFT
# 2SHIFT
# 5LEFT
# sRIGHT
# sLEFT
# BACKSPACE
# RIGHT
# wrLEFT
# 0RIGHT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# SHIFT
# dSHIFT
# SHIFT
# SHIFT
# 1SHIFT
# terminalENTER
# cdSPACE
# SHIFT
# dSHIFT
# ocuTAB
# ENTER
# lsENTER
# rmSPACE
# MINUS
# rfSPACE
# SHIFT
# cSHIFT
# onfidentialDOT
# pdfTAB
# ENTER
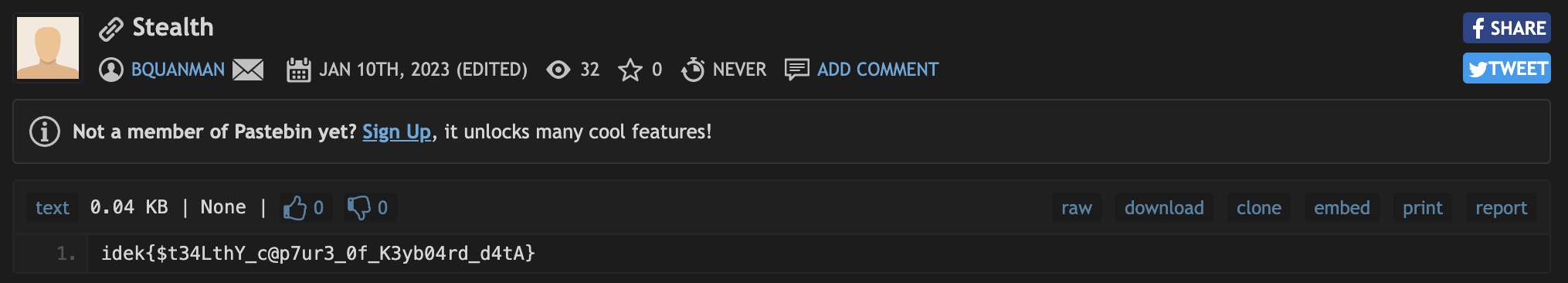
# exitENTER梳理得到
archive manager
Confidentials3cr3t7zP@ssw0rD!terminal
cd Docu
ls
rm -rf Confidential.pdf
exit结合题目描述:Note: archive password has no upper case letter,得到压缩包密码为s3cr3t7zp@ssw0rd!

flag:https://pastebin.com/VtwugbAi
2-layer security
Author: Bquanman #1805 The police organized a surprise attack to catch the hacker along with all the exhibits at the scene. However, the hacker had foreseen that, so he encrypted his secret file before that. He even sarcastically said "you are too stupid to decrypt my 2-layer security" https://mega.nz/file/Sg8UHCKI#m6Vlb9Sr_8idF9aybcws5V3GZLzQd-xvxHbXXZPpCAA
附件给了三个Linux目录文件
# tree -al
.
├── home
│ ├── kalilinux
│ │ ├── .ICEauthority
│ │ ├── .Xauthority
│ │ ├── .bash_logout
│ │ ├── .bashrc
│ │ ├── .bashrc.original
│ │ ├── .cache
│ │ │ ├── gstreamer-1.0
│ │ │ │ └── registry.x86_64.bin
│ │ │ ├── mesa_shader_cache
│ │ │ │ └── index
│ │ │ ├── obexd
│ │ │ ├── powershell
│ │ │ │ ├── ModuleAnalysisCache-AE0255EC
│ │ │ │ └── StartupProfileData-Interactive
│ │ │ ├── sessions
│ │ │ │ ├── thumbs-kalilinux2022:0
│ │ │ │ │ └── Default.png
│ │ │ │ ├── xfce4-session-kalilinux2022:0
│ │ │ │ └── xfce4-session-kalilinux2022:0.bak
│ │ │ ├── thumbnails
│ │ │ │ ├── large
│ │ │ │ └── normal
│ │ │ │ ├── 0f8090d56602d7eca6298b34118a23aa.png
│ │ │ │ └── f18d689c51512129d236408ecbff2d9e.png
│ │ │ └── zcompdump
│ │ ├── .config
│ │ │ ├── Mousepad
│ │ │ │ └── accels.scm
│ │ │ ├── Thunar
│ │ │ │ └── accels.scm
│ │ │ ├── cherrytree
│ │ │ │ └── config.cfg
│ │ │ ├── dconf
│ │ │ │ └── user
│ │ │ ├── gtk-3.0
│ │ │ │ └── bookmarks
│ │ │ ├── powershell
│ │ │ │ └── Microsoft.PowerShell_profile.ps1
│ │ │ ├── pulse
│ │ │ │ ├── 2f4a39def7304770b3a21e4ee09f42fd-card-database.tdb
│ │ │ │ ├── 2f4a39def7304770b3a21e4ee09f42fd-default-sink
│ │ │ │ ├── 2f4a39def7304770b3a21e4ee09f42fd-default-source
│ │ │ │ ├── 2f4a39def7304770b3a21e4ee09f42fd-device-volumes.tdb
│ │ │ │ ├── 2f4a39def7304770b3a21e4ee09f42fd-stream-volumes.tdb
│ │ │ │ └── cookie
│ │ │ ├── qt5ct
│ │ │ │ └── qt5ct.conf
│ │ │ ├── qterminal.org
│ │ │ │ └── qterminal.ini
│ │ │ ├── user-dirs.dirs
│ │ │ ├── user-dirs.locale
│ │ │ └── xfce4
│ │ │ ├── desktop
│ │ │ │ ├── icons.screen.latest.rc
│ │ │ │ ├── icons.screen0-1215x725.rc
│ │ │ │ ├── icons.screen0-1459x837.rc
│ │ │ │ ├── icons.screen0-1902x837.rc
│ │ │ │ ├── icons.screen0-784x555.rc
│ │ │ │ └── icons.screen0-940x835.rc
│ │ │ ├── panel
│ │ │ │ ├── cpugraph-13.rc
│ │ │ │ ├── genmon-15.rc
│ │ │ │ ├── launcher-5
│ │ │ │ │ └── 16461311651.desktop
│ │ │ │ ├── launcher-6
│ │ │ │ │ └── 16461311652.desktop
│ │ │ │ └── launcher-7
│ │ │ │ ├── 16461311653.desktop
│ │ │ │ ├── 16461311654.desktop
│ │ │ │ └── 16461311655.desktop
│ │ │ ├── xfconf
│ │ │ │ └── xfce-perchannel-xml
│ │ │ │ ├── displays.xml
│ │ │ │ ├── keyboards.xml
│ │ │ │ ├── thunar.xml
│ │ │ │ ├── xfce4-desktop.xml
│ │ │ │ ├── xfce4-keyboard-shortcuts.xml
│ │ │ │ ├── xfce4-notifyd.xml
│ │ │ │ ├── xfce4-panel.xml
│ │ │ │ ├── xfce4-power-manager.xml
│ │ │ │ ├── xfce4-session.xml
│ │ │ │ ├── xfwm4.xml
│ │ │ │ └── xsettings.xml
│ │ │ └── xfwm4
│ │ ├── .dmrc
│ │ ├── .face
│ │ ├── .face.icon
│ │ ├── .gnupg
│ │ │ ├── openpgp-revocs.d
│ │ │ │ ├── 5295D629A12B0703063559ED1E9F58A43C01EDBB.rev
│ │ │ │ ├── B719E23BEED6B02C76494DB43AE26A2802699708.rev
│ │ │ │ └── BD3EF2F8AFFDCC3A933E33E756EEDD86FA3AEBB6.rev
│ │ │ ├── private-keys-v1.d
│ │ │ │ ├── 086209F7CE0A6A241FF8E5165F172D6B23D94860.key
│ │ │ │ ├── 1CF28C08F8EDB31405B7E6FF06C0A68F19339D95.key
│ │ │ │ ├── 4A35B264D5836087860B82F7C3CA3A855AB39BD4.key
│ │ │ │ ├── 8EE9B7929AC7F8FFF5B65E91267E0FB37719B23C.key
│ │ │ │ ├── AF73C3D44EC1DF1DB750339D7A370AAE610B83E4.key
│ │ │ │ └── F7434A624A280A4ADFC3050D2A5E5D3EE6C89231.key
│ │ │ ├── pubring.kbx
│ │ │ ├── pubring.kbx~
│ │ │ ├── random_seed
│ │ │ └── trustdb.gpg
│ │ ├── .java
│ │ │ └── .userPrefs
│ │ │ └── burp
│ │ │ └── prefs.xml
│ │ ├── .local
│ │ │ ├── share
│ │ │ │ ├── Mousepad
│ │ │ │ ├── Trash
│ │ │ │ │ ├── expunged
│ │ │ │ │ ├── files
│ │ │ │ │ └── info
│ │ │ │ ├── gvfs-metadata
│ │ │ │ │ ├── home
│ │ │ │ │ └── home-fb50f72c.log
│ │ │ │ ├── icc
│ │ │ │ ├── powershell
│ │ │ │ │ ├── Modules
│ │ │ │ │ └── PSReadLine
│ │ │ │ │ └── ConsoleHost_history.txt
│ │ │ │ └── recently-used.xbel
│ │ │ └── state
│ │ │ └── pipewire
│ │ │ └── media-session.d
│ │ │ ├── bluez-autoswitch
│ │ │ └── default-routes
│ │ ├── .profile
│ │ ├── .zsh_history
│ │ ├── .zshrc
│ │ ├── Desktop
│ │ │ └── recycle.bin
│ │ ├── Documents
│ │ ├── Downloads
│ │ ├── Music
│ │ ├── Pictures
│ │ ├── Public
│ │ ├── Templates
│ │ └── Videos
│ └── lost+found
├── mnt
└── root
├── .bashrc
├── .bashrc.original
├── .cache
│ ├── dconf
│ ├── doc
│ ├── gstreamer-1.0
│ │ └── registry.x86_64.bin
│ ├── gvfs
│ ├── gvfsd
│ └── keyring-54OQY1
├── .config
│ ├── Thunar
│ │ └── accels.scm
│ ├── dconf
│ │ └── user
│ ├── gtk-3.0
│ └── xfce4
│ └── xfconf
│ └── xfce-perchannel-xml
│ └── thunar.xml
├── .dbus
│ └── session-bus
│ └── c604c00892aaac0691d30986621df2e7-0
├── .face
├── .face.icon
├── .local
│ └── share
│ ├── keyrings
│ └── nano
├── .profile
└── .zshrc
84 directories, 93 files读取home/kalilinux/.zsh_history,看到从pastebin下载了一个文件,用gpg加密了RestrictedAccess.pdf,又把加密后的文件随机明文重命名为T3C4U.SOS,最后改为recycle.bin。
# cat ./home/kalilinux/.zsh_history
cd ~
cd Desktop
ls
clear
cd ../../../../../../../../
cd /var/log
cd ~
sudo apt install curl
curl https://pastebin.com/raw/awhuFZse -0 tienbip.txt
LESSCLOSE=/usr/bin/lesspipe %s %s
cd -
cd Desktop
ls
gpg --quick-gen-key Cocainit
gpg --quick-gen-key VNvodich
gpg --quick-gen-key Siuuuuuu
ls
gpg -er VNvodich RestrictedAccess.pdf
ls
rm -rf RestrictedAccess.pdf
cat /etc/shadow | grep idek{
cat /etc/shadow | grep "idek{"
mv RestrictedAccess.pdf.gpg $(cat /dev/urandom | tr -dc 'a-zA-Z0-9' | fold -w 5 | head -n 1)
pwsh
ls
mv T3C4U.SOS recycle.bin
rebootpastebin的文件已被删除,recycle.bin在home/kalilinux/Desktop目录下,在home/kalilinux/.local/share/powershell/PSReadLine/目录下看到powershell历史记录文件。
# cat ./home/kalilinux/.local/share/powershell/PSReadLine/ConsoleHost_history.txt
ls
whoami
( nEw-oBJECT syStem.io.sTrEamReadeR( ( nEw-oBJECT sysTeM.iO.COMPReSsioN.deflAtEsTREaM([sySTEM.iO.MeMoRyStreaM] [ConVert]::froMbaSe64striNg('hVXbbuJIEH2PlH/omZfYGrAwtxCkPASWXLTDgGL2Mot46MENeGLaqN3WLov873uqbQPGiRZhulz3OlXVBKM/mWVZnw/tRnpw79JDs5Me2l3QOF0XNJ4mydqge+mh1cJ5i5Me6DQhAkVakLjQwLcNAXy1yB9em2QLaYto2HVIk94Rpw0dF2eLYkDWBN2ENxeOwepQCumBEqI3eqALWQvcDs42niY9FA+vYN+mn+srdsPyT3p9dX1VvHyfjoVcqv1OR4rd0ysX8ZjLm9oNXwsfrG/i7/rkx0+x1Mzbx1psHU8sExXovTM0dmvFd1BnJeNDKUS84WCTQ+eXIN5FsbBsKEBPGaKSjPAHey3iLKNjgs5McRmvIrV9DCQPYZ7rlVxkOVSCXXxOnGDFLJhNud7Y7CxvSm8QRss3ku5CHkgTq8YaNVbiOF+FXMP4ohCYn0ID9JTK5bsNcAt2G6HGkS8W/f5wMLw2lThT7vuBXKPo+cdIwzzXy+3/gnEVsxMIEG+zHCyQ/f6r4P5DGBpdquwxCIXzmIThN74VF0BBHCWakMm8lnTZF/ZTThxv4uG4vqJyR5M3+/+xptlScKCF8oQ2ru7JlSmSQoC2FyejuacV6l3kTcoEdjHFA7EOJHtv3gze+BnjKecExvsAQ2AVoeeTRO8S4sCXzzF/+wwFrRJRY1Oa+VOrXiYOpb6gVpYRUEInSlKBpMCOE850VAAMI/+jGaY2mzgEcME0c+kF/wowtVk+9gfqEPWRUljk+ljEMRSPQWWk2SpKpP/J9OqyQT+U4G9ldlqZhNPAU8AsaJEttVRvSr7T4+AXnRpJn8zMOGWJPix1EEnmIUWpw/0wkjqQyQV+NDOfKoOKjsMXtuGhgCrL6LIf/b4B5oHQIz7Os+HPp7tWvXqOYwyDZqebA3/GfO/GyOAwiN+zJygVK+s9UwLNnlkToSJzY4FcJTKDYJQFJzJ3OB9u/VDoQSBp2aF7thDTYn/APi3mVx5rU+ws2GbD6R679N7FeL4WZ2KwZ/udsOZxtnbFPkxpl8oL88G/BNWo6y+Am9VNt7/ThDsvv+PKOAGdG8OT4FrkAETHjK2nwsepT3apRsE+Ku9XsaflQF5o3dkcmjJUtMR2XNwYZeNsz8/+tYbRdpdo8czjjVVM2Ez8ox2kHVF/MGe/zR57DpLOhgtX4eVM3di2o8Q05EthWfPlM39ddO++ZMRtQbiNW7s292avL/JpkbFadxU7t9Et9N3G0UXFsF0x7BVxekezaryuzez/AA==' ), [SyStem.IO.comPreSSION.cOmpreSSIONModE]::DEcOmPREsS ) ), [text.ENcodiNg]::AScII)).ReAdToend()|&( $sHeLLid[1]+$shELliD[13]+'x')
Encryption -Path ./T3C4U
Remove-Item -Path ./T3C4U -Force -Recurse
exit解powershell脚本得到
iEX ((("{40}{19}{25}{46}{15}{11}{41}{20}{14}{48}{33}{47}{37}{35}{2}{1}{31}{23}{18}{8}{45}{9}{39}{28}{24}{43}{38}{27}{53}{13}{36}{49}{16}{30}{17}{26}{21}{12}{0}{51}{4}{6}{10}{50}{5}{32}{34}{52}{42}{22}{29}{3}{44}{7}"-f ' }
YPMencryptor = YPMaesMan','aged = New-Object System.Security.Cryptograp',' YPMaesMan','{
YPMshaManaged.Dispose()
','r()
YPMencryptedBytes = YPMencryptor.TransformFinal','edBytes
YPMaesManaged.Dispose()
if (YPMPath) {
','Block(YPMplainBytes, 0, YPMplainBytes.Length)
YPMen','se()
}
}','raphy.CipherMode]::CBC
','ed.Padding = [System.Security.Cryptography.PaddingMode]::Z','cryptedBytes = YPMaesManaged','m
(','::ReadAllBytes(YPMFile.FullName)
YPMoutPath = YPMFile.FullName + jnO.SOSjnO
','sEOk))
if (Y','arameterSetName = jnOCryptFilejnO)]
[String]YPMPath
)
Begin {
YPMshaMan','ra','M','
','ystem.Security.Cryptog','()]
[Outpu','(Mandatory = YPMtrue, P',' = [System.IO.File]','e
return jnOFile encrypted to YPMoutP','d
YPMaesManaged.Mode = [S','sManaged.BlockSize','t',' Write-Error -Message jnOFile not found!jnO
break
}
YPMplainBytes',' ',' YPMae','athjnO
}
}
End ','Path -ErrorAction SilentlyContinue
if (!YPMFile.FullName) {
','hy.AesManage',' [System.IO.File]::WriteA','stem.','llBytes(YPMoutPath, YPMencryptedBytes)
','256Managed
','PMPath) {
YPMFile = G','ography.SHA','28
','eros
','function Encryption {
[CmdletBinding','
[Parameter','= YPMFile.LastWriteTim',' = 1',' YPMaesManaged.Dispo','
YPMaesManag','Type([string])]
Pa','Security.Crypt','aged = New-Object Sy','et-Item -Path YP','.IV + YPMencrypt','aged.CreateEncrypto',' (Get-Item YPMoutPath).LastWriteTime ',' YPMaesManaged.KeySize = 256
}
Process {
YPMaesManaged.Key = YPMshaManaged.ComputeHash([System.Text.Encoding]::UTF8.GetBytes(EOkYPMencryptedByte')).rePlace(([cHaR]69+[cHaR]79+[cHaR]107),[STRInG][cHaR]39).rePlace(([cHaR]106+[cHaR]110+[cHaR]79),[STRInG][cHaR]34).rePlace(([cHaR]89+[cHaR]80+[cHaR]77),[STRInG][cHaR]36) )格式化上述代码:
function Encryption{
[CmdletBinding()]
[OutputType([string])]
Param(
[Parameter(Mandatory = $true, ParameterSetName = "CryptFile")]
[String]$Path
)
Begin {
$shaManaged = New-Object System.Security.Cryptography.SHA256Managed
$aesManaged = New-Object System.Security.Cryptography.AesManaged
$aesManaged.Mode = [System.Security.Cryptography.CipherMode]::CBC
$aesManaged.Padding = [System.Security.Cryptography.PaddingMode]::Zeros
$aesManaged.BlockSize = 128
$aesManaged.KeySize = 256
}
Process {
$aesManaged.Key = $shaManaged.ComputeHash([System.Text.Encoding]::UTF8.GetBytes('$encryptedBytes'))
if ($Path) {
$File = Get-Item -Path $Path -ErrorAction SilentlyContinue
if (!$File.FullName) {
Write-Error -Message "File not found!"
break
}
$plainBytes = [System.IO.File]::ReadAllBytes($File.FullName)
$outPath = $File.FullName + ".SOS"
}
$encryptor = $aesManaged.CreateEncryptor()
$encryptedBytes = $encryptor.TransformFinalBlock($plainBytes, 0, $plainBytes.Length)
$encryptedBytes = $aesManaged.IV + $encryptedBytes
$aesManaged.Dispose()
if ($Path) {
[System.IO.File]::WriteAllBytes($outPath, $encryptedBytes)
(Get-Item $outPath).LastWriteTime = $File.LastWriteTime
return "File encrypted to $outPath"
}
}
End {
$shaManaged.Dispose()
$aesManaged.Dispose()
}
} 代码的加密步骤,对recycle.bin第一次解密,其中可以看到IV是SOS文件的前16字节,key是sha256($encryptedBytes)。得到RestrictedAccess.pdf.gpg。
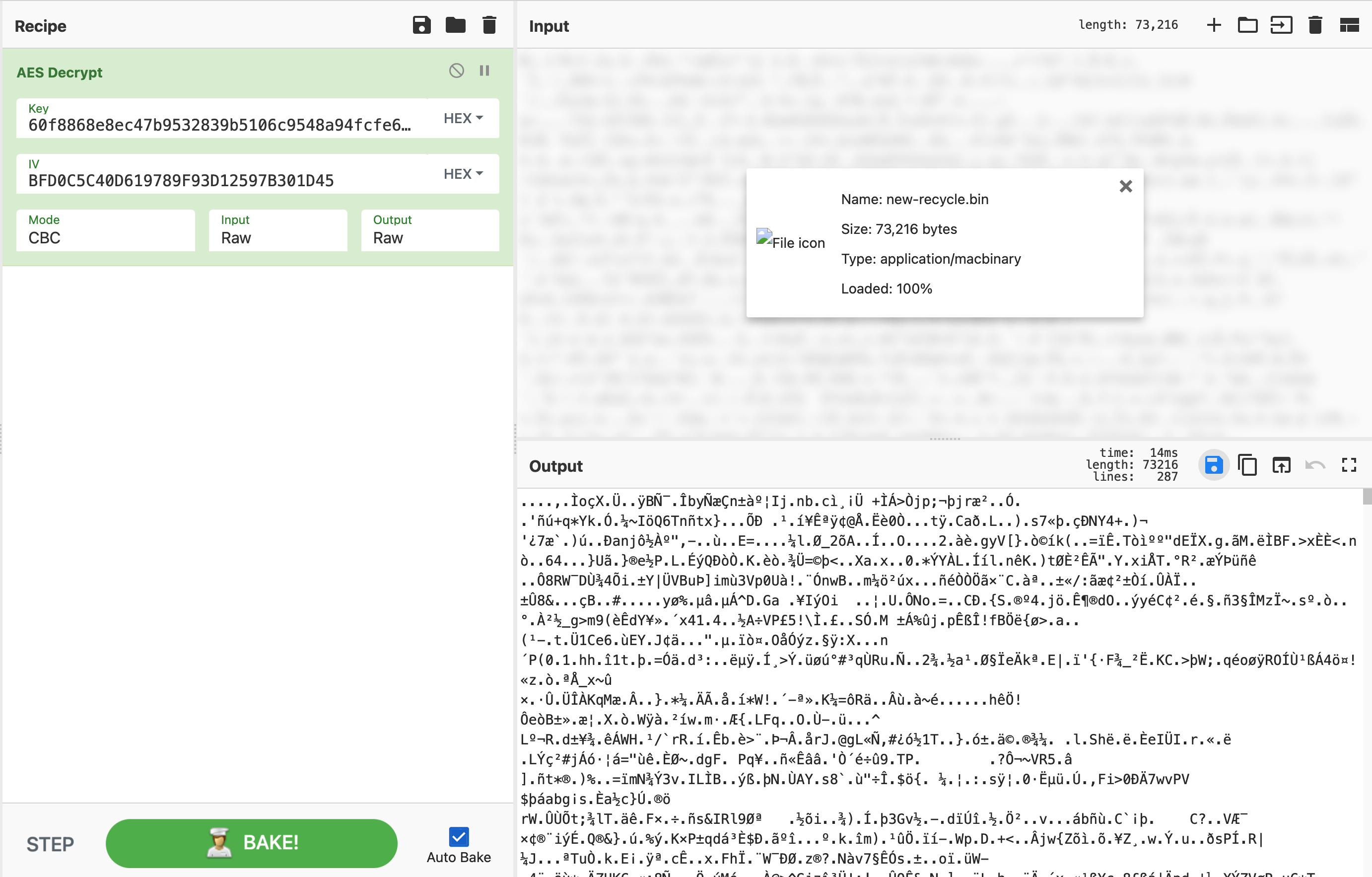
gpg解密将.gnupg替换掉本地尝试解密成功。
# gpg -d T3C4U.pdf.gpg > RestrictedAccess.pdf
gpg: 由 3072 位的 RSA 密钥加密,标识为 2C94CC6FE75882DC,生成于 2023-01-13
“VNvodich”
gpg: 警告:加密过的报文已经变造!